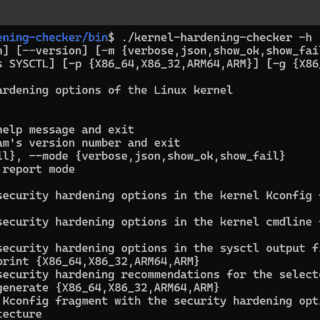
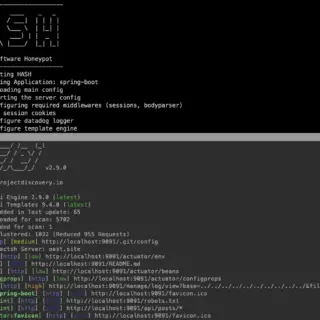
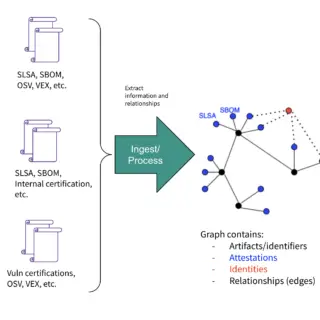
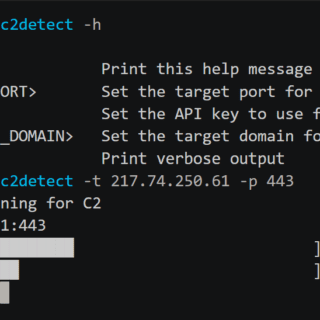
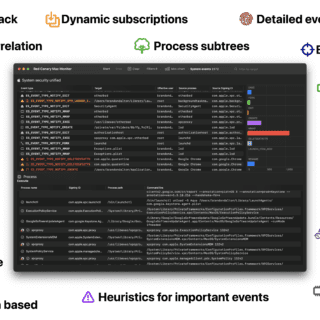
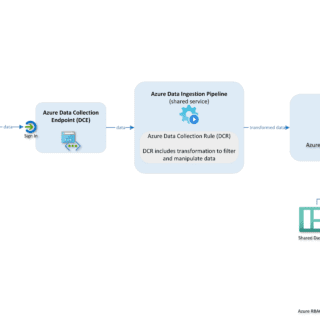
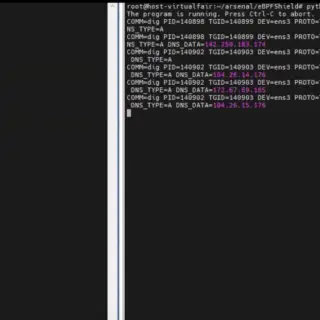
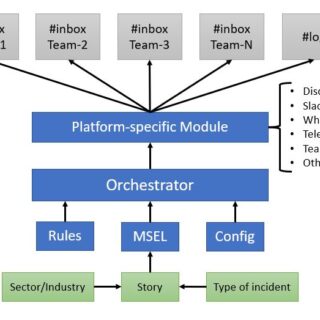
kernel hardening checker v0.6.6 releases: checking the hardening options in the Linux kernel config
kernel hardening checker There are plenty of Linux kernel hardening config options. A lot of them are not enabled by the major distros. We have to enable these options ourselves to make our systems...