Category: Malware Analysis
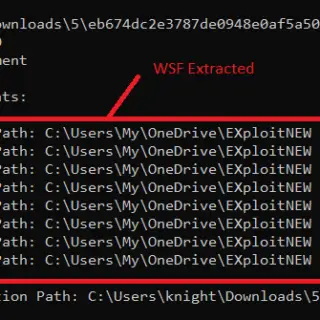
OneNoteAnalyzer A C# based tool for analyzing malicious OneNote documents Description Recently we came across a few malicious OneNote Documents being distributed in the wild by various threat actors. This gave us the idea...
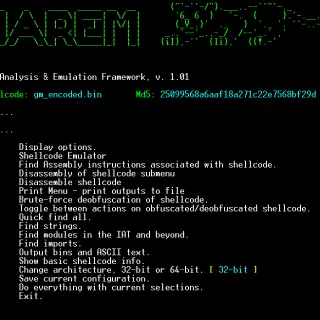
sharem SHAREM is intended to be the ultimate Windows shellcode tool, with support to emulate over 12,000 WinAPIs, virtually all user-mode Windows syscalls, and SHAREM provides numerous new features. SHAREM was released on September...
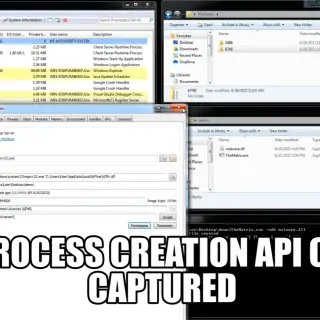
TheMatrix This project was created to ease the malware analysis process. The goal is to create an activator binary whose purpose is to load a user-defined binary and monitor the execution by using Win32...
Malware Detection using machine learning Analysis modules: Static: Features are extracted from PE file headers (mainly Optional Header) Dynamic: Features are the API calls traced using Cuckoo Sandbox Datasets construction Static Malware samples were...
DotDumper An automatic unpacker and logger for DotNet Framework targeting files! This tool has been unveiled at Black Hat USA 2022. The automatic detection and classification of any given file in a reliable manner is...
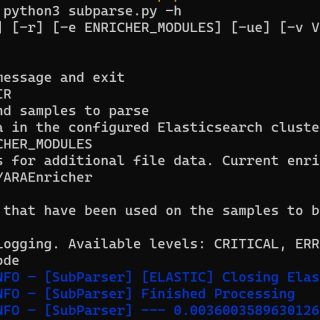
subparse Subparse is a modular framework developed by Josh Strochein, Aaron Baker, and Odin Bernstein. The framework is designed to parse and index malware files and present the information found during the parsing in...
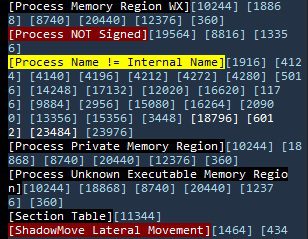
WhacAMole WhacAMole is a program that analyzes processes in memory in an integral way, detecting and alerting of anomalies related to the malware and presenting and saving in files all the relevant information for...
THE YARALYZER Visually inspect all of the regex matches (and their sexier, more cloak-and-dagger cousins, the YARA matches) found in binary data and/or text. See what happens when you force various character encodings upon those...
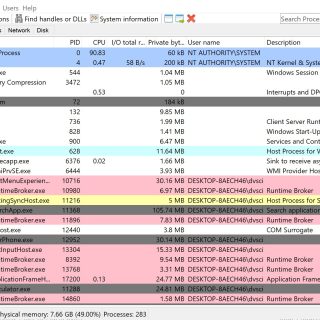
systeminformer A free, powerful, multi-purpose tool that helps you monitor system resources, debug software and detect malware. Brought to you by Winsider Seminars & Solutions, Inc. Features A detailed overview of system activity with...
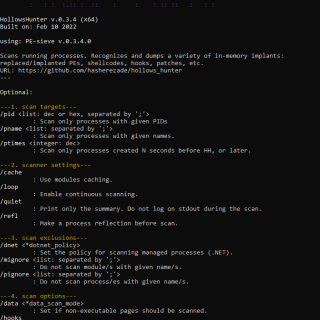
hollows_hunter Scans all running processes. Recognizes and dumps a variety of potentially malicious implants (replaced/implanted PEs, shellcodes, hooks, in-memory patches). It is an application based on PE-sieve (a library version), so there is a big overlap...
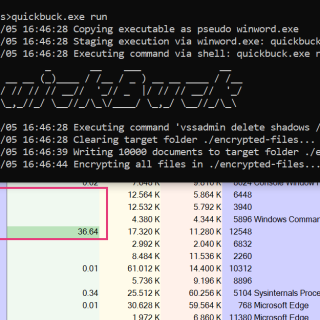
Ransomware Simulator The goal of this repository is to provide a simple, harmless way to check your AV’s protection on ransomware. This tool simulates typical ransomware behaviour, such as: Staging from a Word document...
DroidDetective DroidDetective is a Python tool for analysing Android applications (APKs) for potential malware-related behaviour and configurations. When provided with a path to an application (APK file) Droid Detective will make a prediction (using...
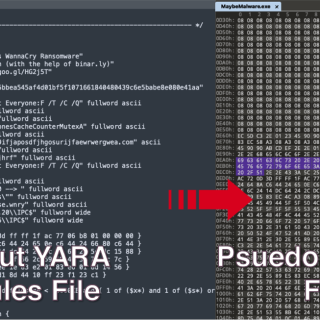
Arya – The Reverse YARA Arya is a unique tool that produces pseudo-malicious files meant to trigger YARA rules. You can think of it as a reverse YARA because it does exactly the opposite...
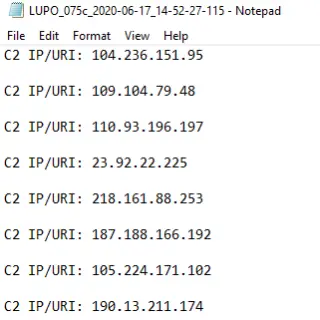
Lupo — Malware IOC Extractor Debugging module for Malware Analysis Automation Introduction Working on security incidents that involve malware, we come across situations on a regular basis where we feel the need to automate...
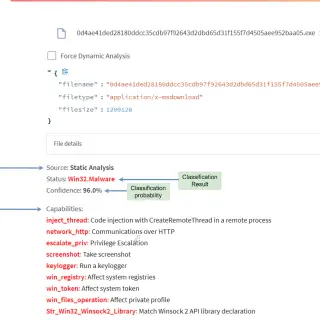
Verdict-as-a-Service Verdict-as-a-Service (VaaS) is a service that provides a platform for scanning files for malware and other threats. It allows easy integration in your application. With a few lines of code, you can start scanning...