patching: Interactive Binary Patching Plugin for IDA Pro
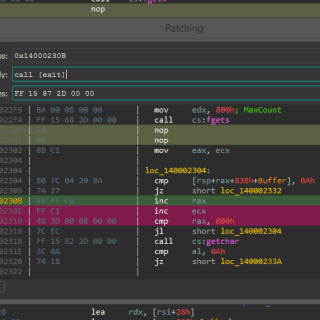
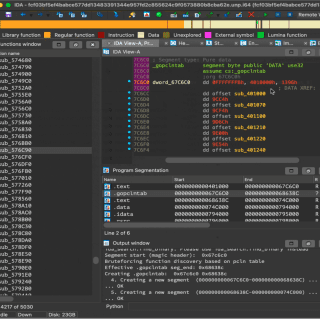
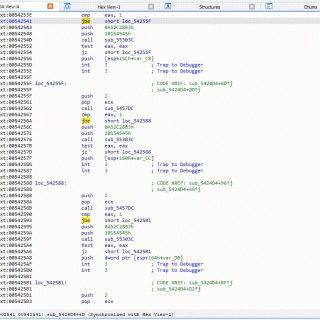
Patching – Interactive Binary Patching for IDA Pro Patching assembly code to change the behavior of an existing program is not uncommon in malware analysis, software reverse engineering, and broader domains of security research....