Category: Malware Analysis
medusa Medusa is an extensible framework for Android applications which automates processes and techniques practised during the dynamic analysis of a malware investigation. Some of the framework’s features are the following: Tracing and instrumentation of...
FileInsight-plugins: decoding toolbox of McAfee FileInsight hex editor for malware analysis FileInsight-plugins is a large set of plugins for the McAfee FileInsight hex editor. It adds many capabilities such as...
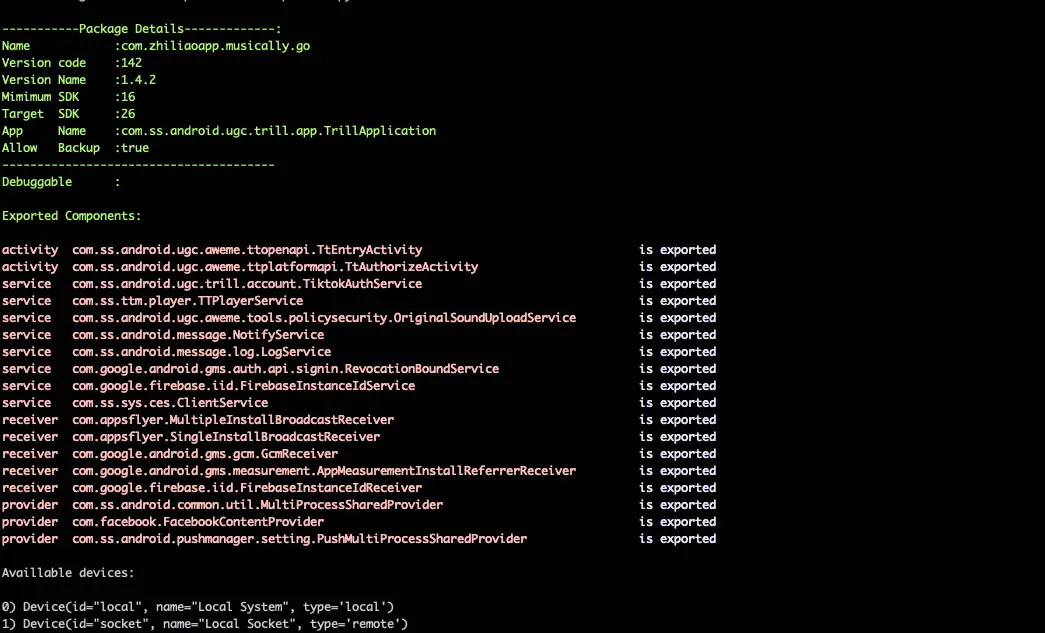
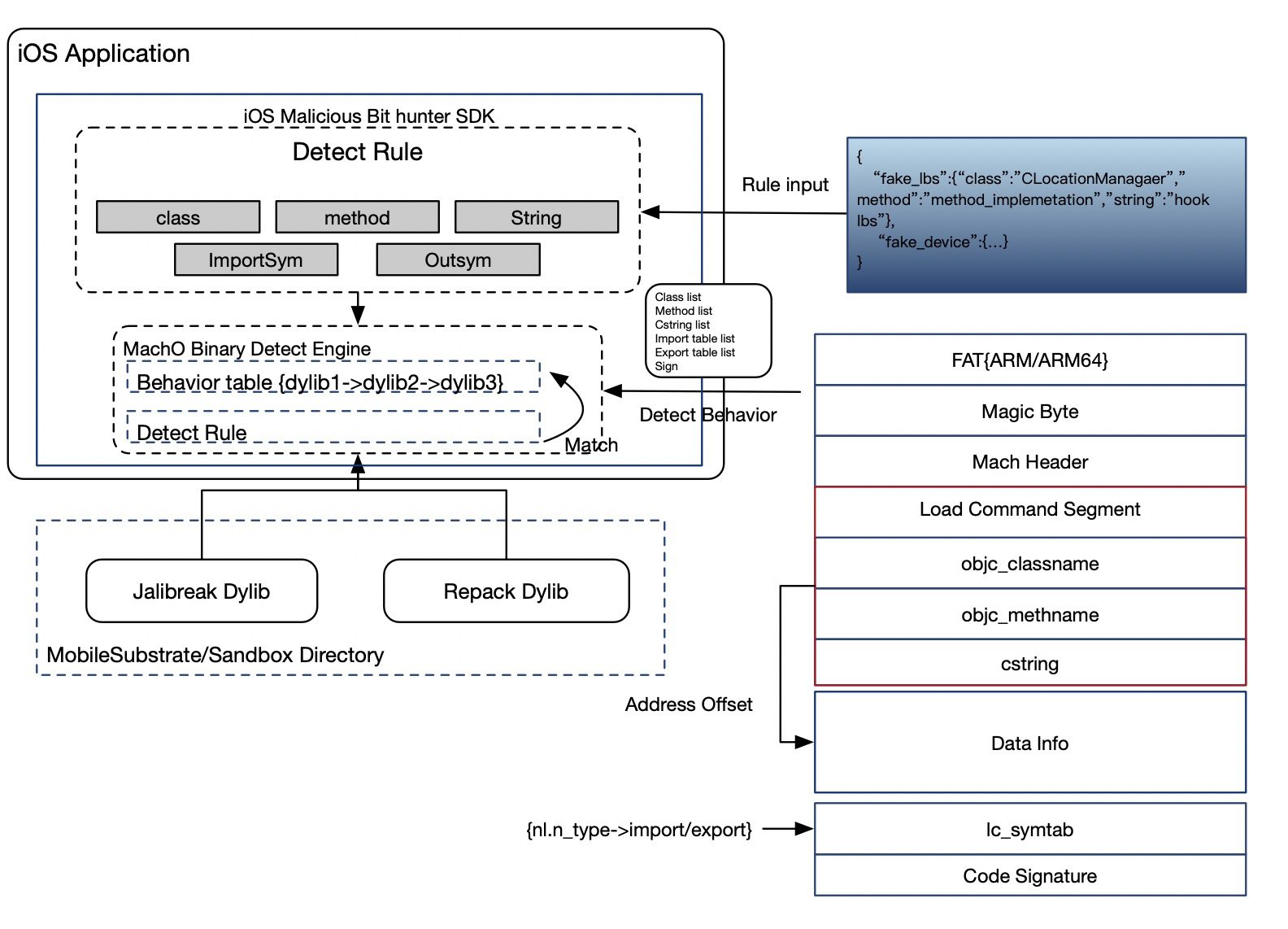
iOS Malicious Bit Hunter iOS Malicious Bit Hunter is a malicious plug-in detection engine for iOS applications. It can analyze the head of the macho file of the injected dylib...
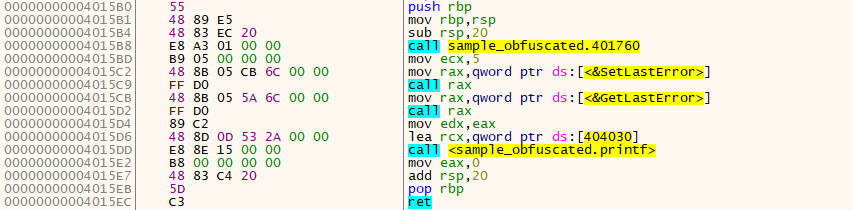
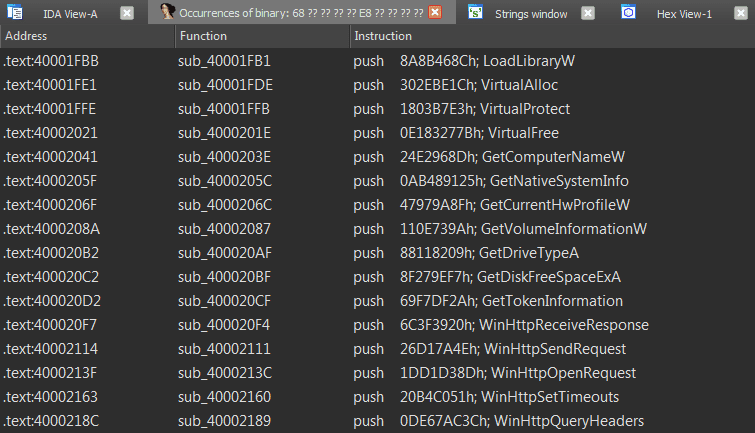
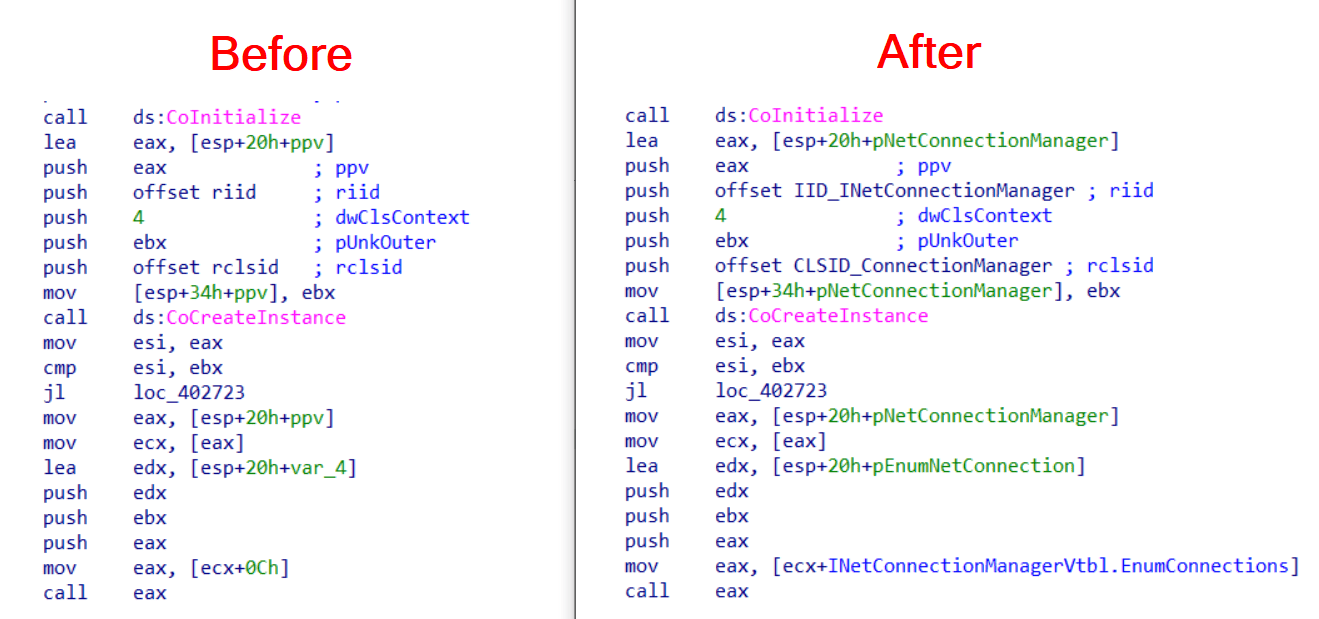
CallObfuscator Obfuscate (hide) the PE imports from static/dynamic analysis tools. Theory This’s pretty forward, let’s say I’ve used VirtualProtect and I want to obfuscate it with Sleep, the tool will...
Strafer Elasticsearch infections are rising exponentially. The adversaries are exploiting open and exposed Elasticsearch interfaces to trigger infections in the cloud and non-cloud deployments. During this talk, we will release...
Trend Micro ELF Hash (telfhash) telfhash is a symbol hash for ELF files, just like imphash is imports hash for PE files. Telfhash is an architecture-agnostic hash based on symbols...
Uchihash Uchihash is a small utility that can save malware analysts the time of dealing with embedded hash values used for various things such as: Dynamically importing APIs (especially in...
COM-Code-Helper Two IDAPython Scripts help you to reconstruct Microsoft COM (Component Object Model) Code Especially malware reversers will find this useful, as COM Code is still regularly found in malware....
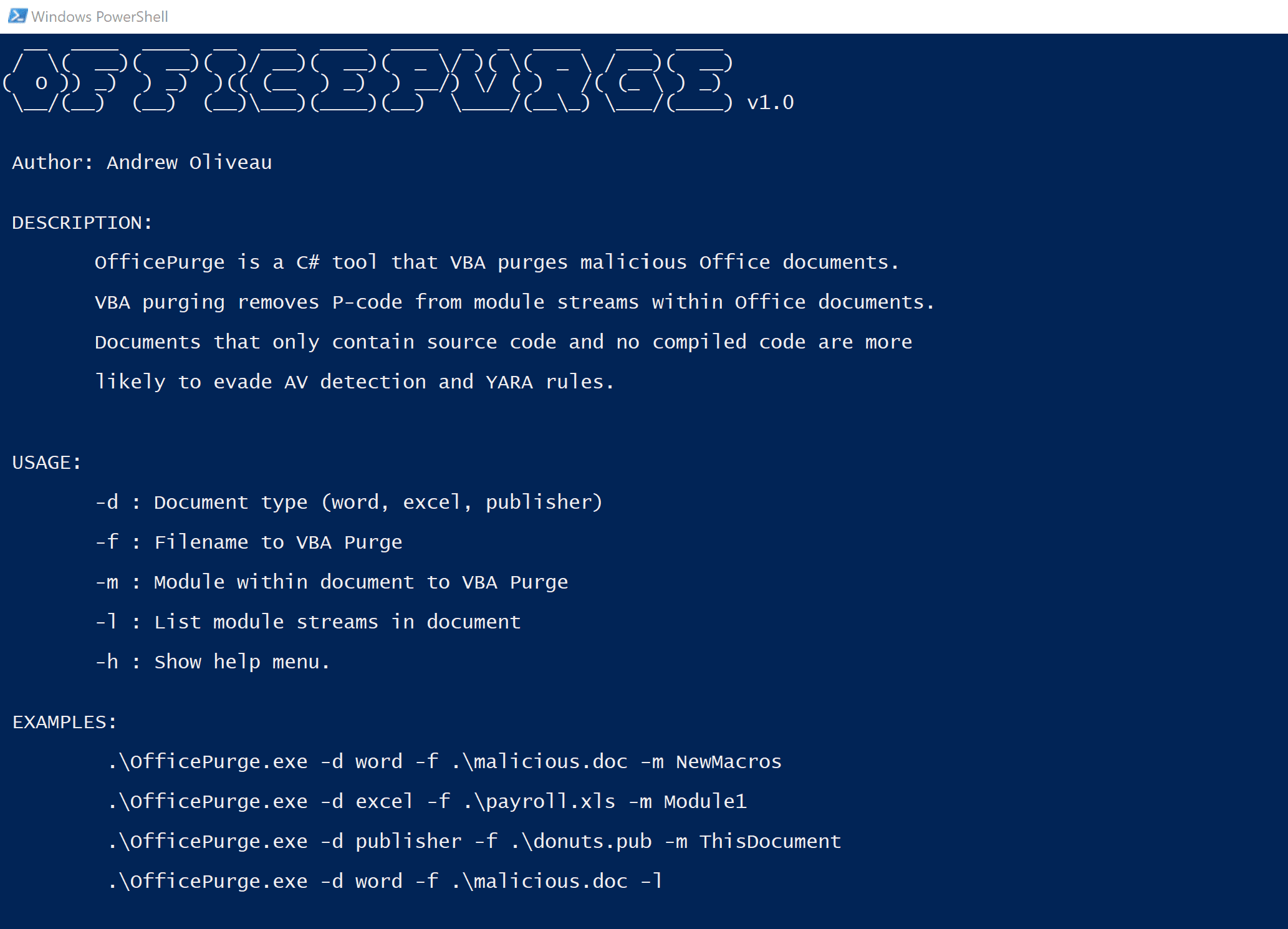
OfficePurge VBA purge your Office documents with OfficePurge. VBA purging removes P-code from module streams within Office documents. Documents that only contain source code and no compiled code are more...
ATMMalScan ATMMalScan is a commandline tool for Windows operating systems version 7 and higher, which helps to search for malware traces on an ATM during the DFIR process. This tool...
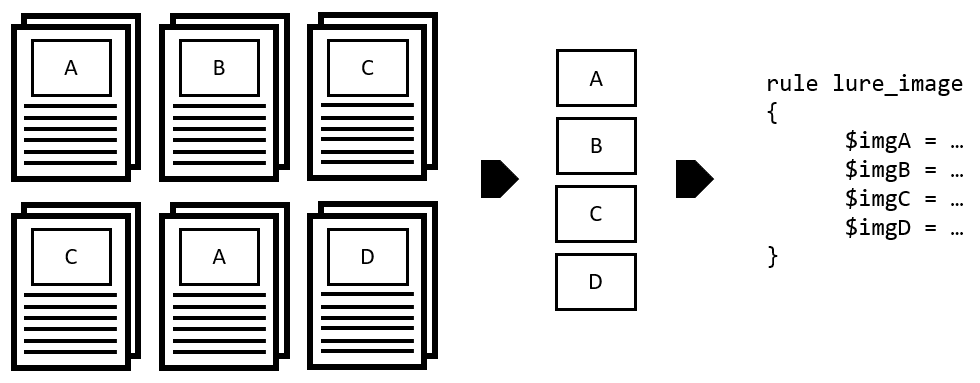
Halogen Halogen is a tool to automate the creation of yara rules against image files embedded within a malicious document. Download git clone https://github.com/target/halogen.git Use Testing it out We’ve...
Malduck Malduck is your ducky companion in malware analysis journeys. It is mostly based on the Roach project, which derives many concepts from mlib library created by Maciej Kotowicz. The purpose of the fork...
freki Freki is a free and open-source malware analysis platform. Goals Facilitate malware analysis and reverse engineering; Provide an easy-to-use REST API for different projects; Easy deployment (via Docker); Allow...
ThreatPursuit-VM Threat Pursuit Virtual Machine (VM): A fully customizable, open-sourced Windows-based distribution focused on threat intelligence analysis and hunting designed for intel and malware analysts as well as threat hunters...
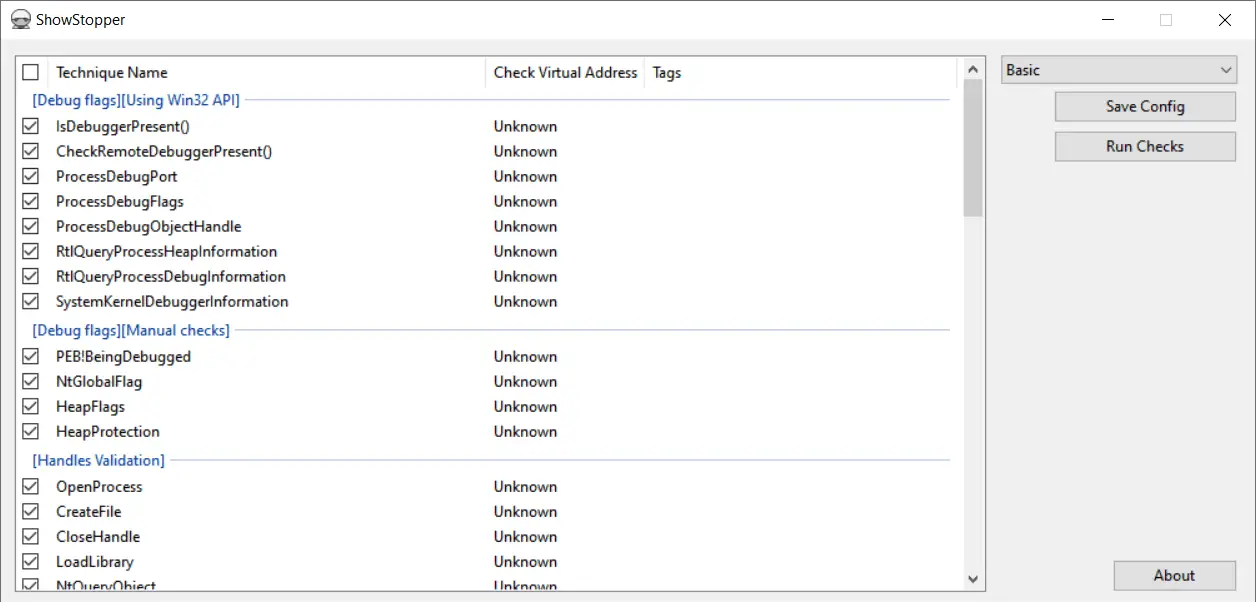
ShowStopper – Anti-Debug tricks exploration tool The ShowStopper project is a tool to help malware researchers explore and test anti-debug techniques or verify debugger plugins or other solutions that clash with standard...