Codecepticon v1.2.2 releases: obfuscate C#, VBA/VB6 (macros), and PowerShell source code
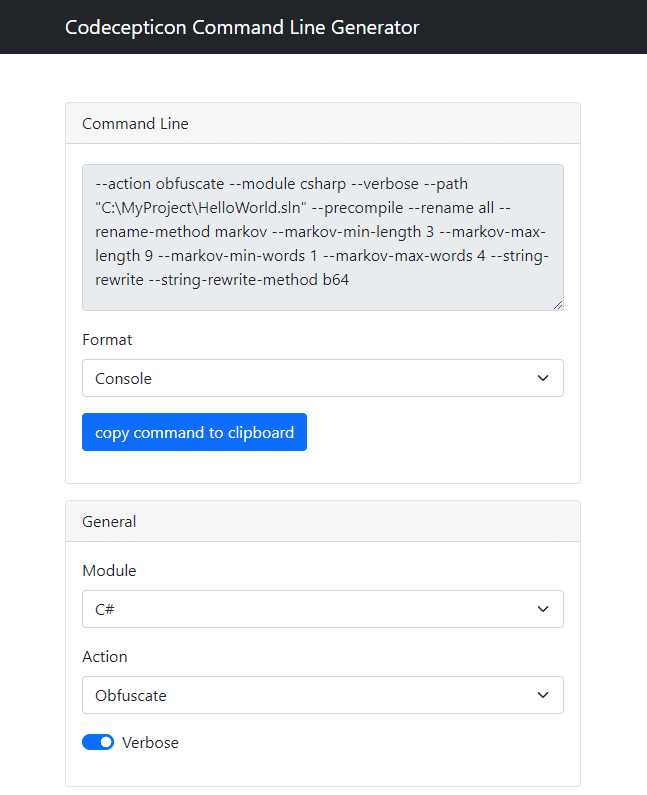
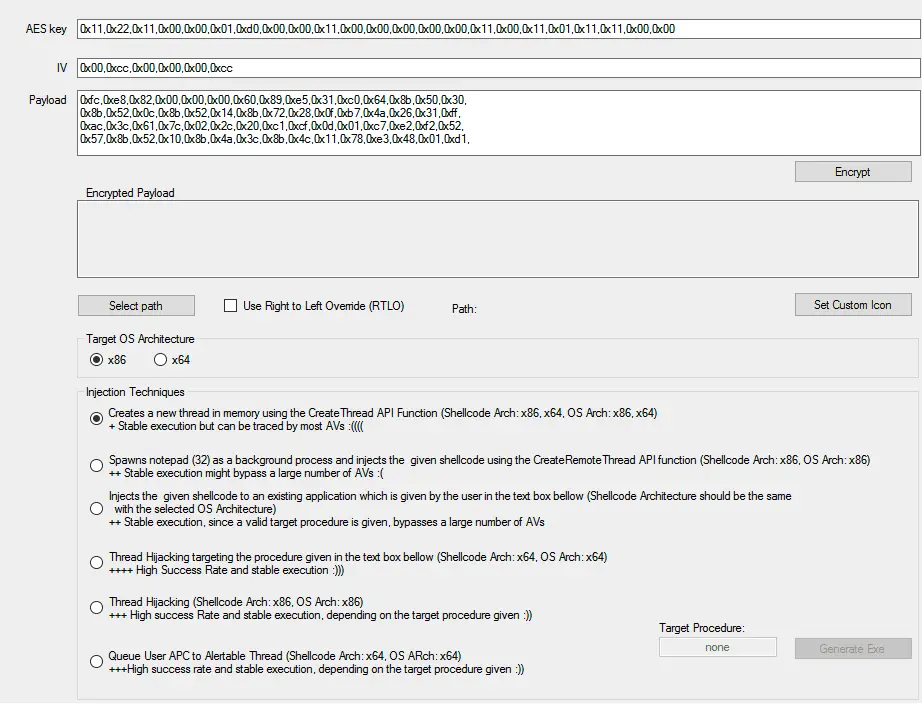
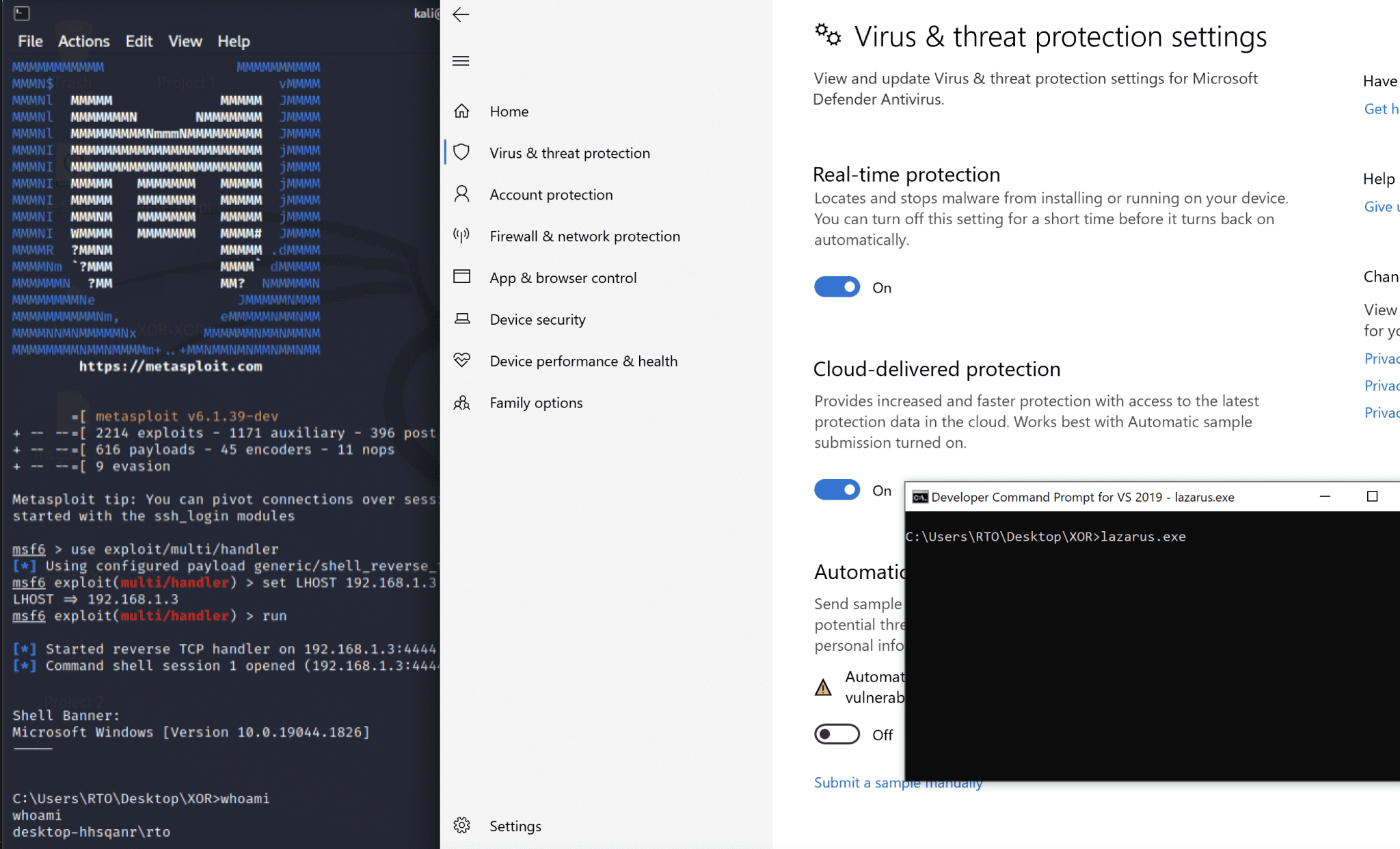
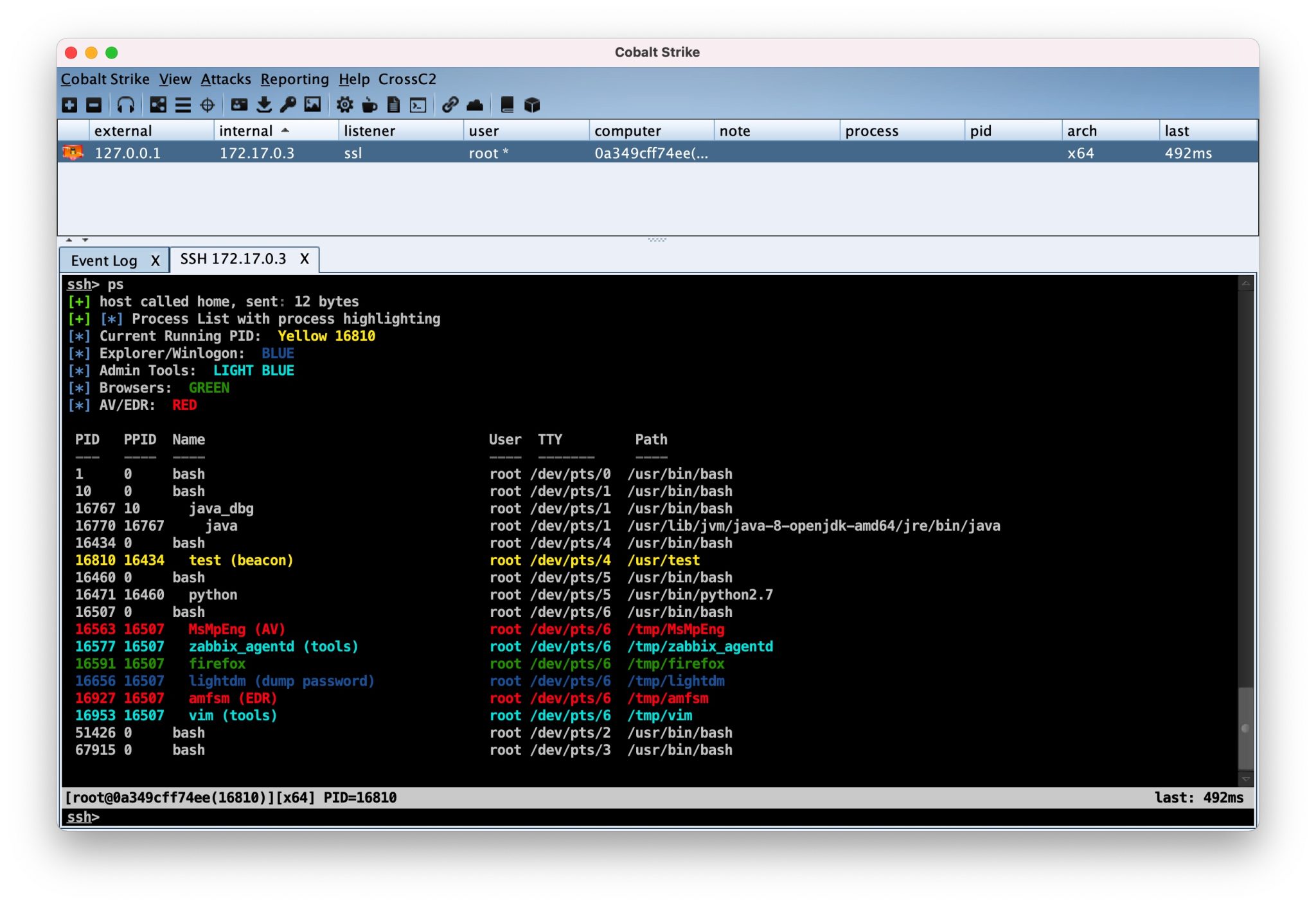
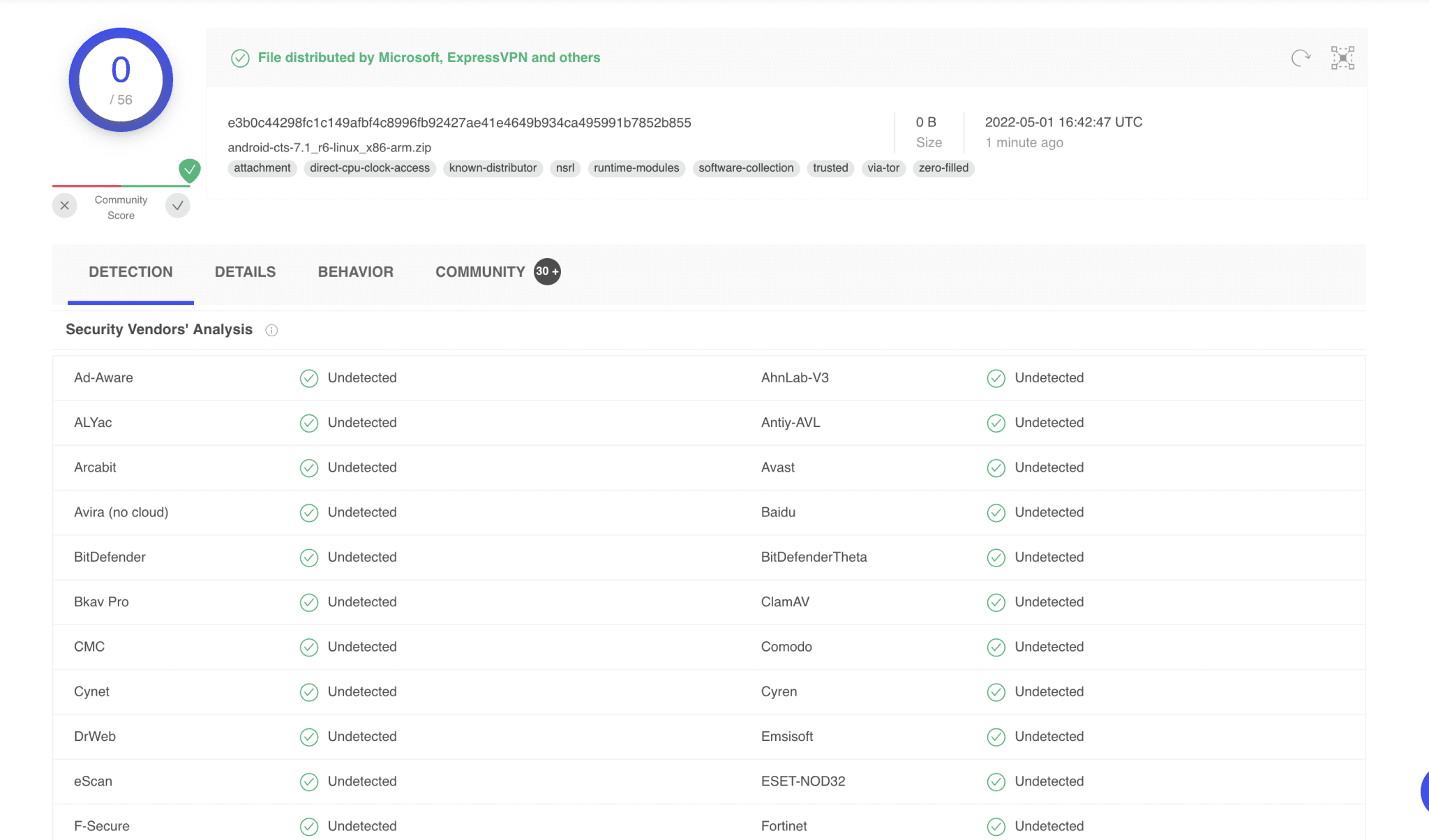
Codecepticon Codecepticon is a .NET application that allows you to obfuscate C#, VBA/VB6 (macros), and PowerShell source code, and is developed for offensive security engagements such as Red/Purple Teams. What...