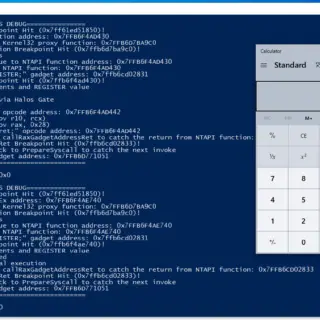
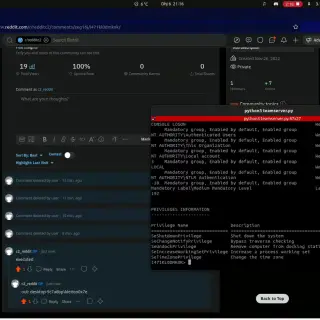
HWSyscalls: new method to execute indirect syscalls
HWSyscalls HWSyscalls is a new method to execute indirect syscalls using 3 main components: Hardware breakpoints and Vectored Exception Handler to control the flow of execution. HalosGate is used to find syscall numbers and...