Category: Post Exploitation
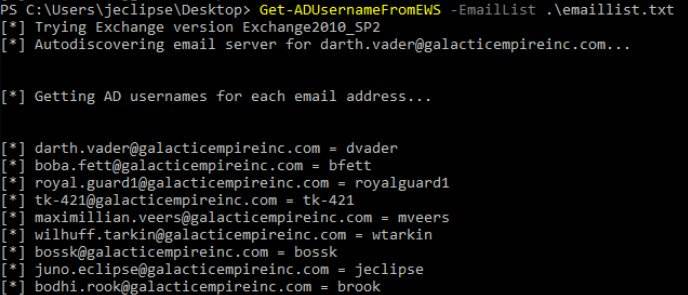
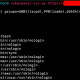
MailSniper MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). It can be used...
Description A JavaScript and VBScript shellcode launcher. This will spawn a 32-bit version of the binary specified and inject shellcode into it. DotNetToJScript can be found here: https://github.com/tyranid/DotNetToJScript Download Usage: Choose...
A JavaScript and VBScript Based Empire Launcher – by Cn33liz 2017 Both Launchers run within their own embedded PowerShell Host, so we don’t need PowerShell.exe. This might be useful when...
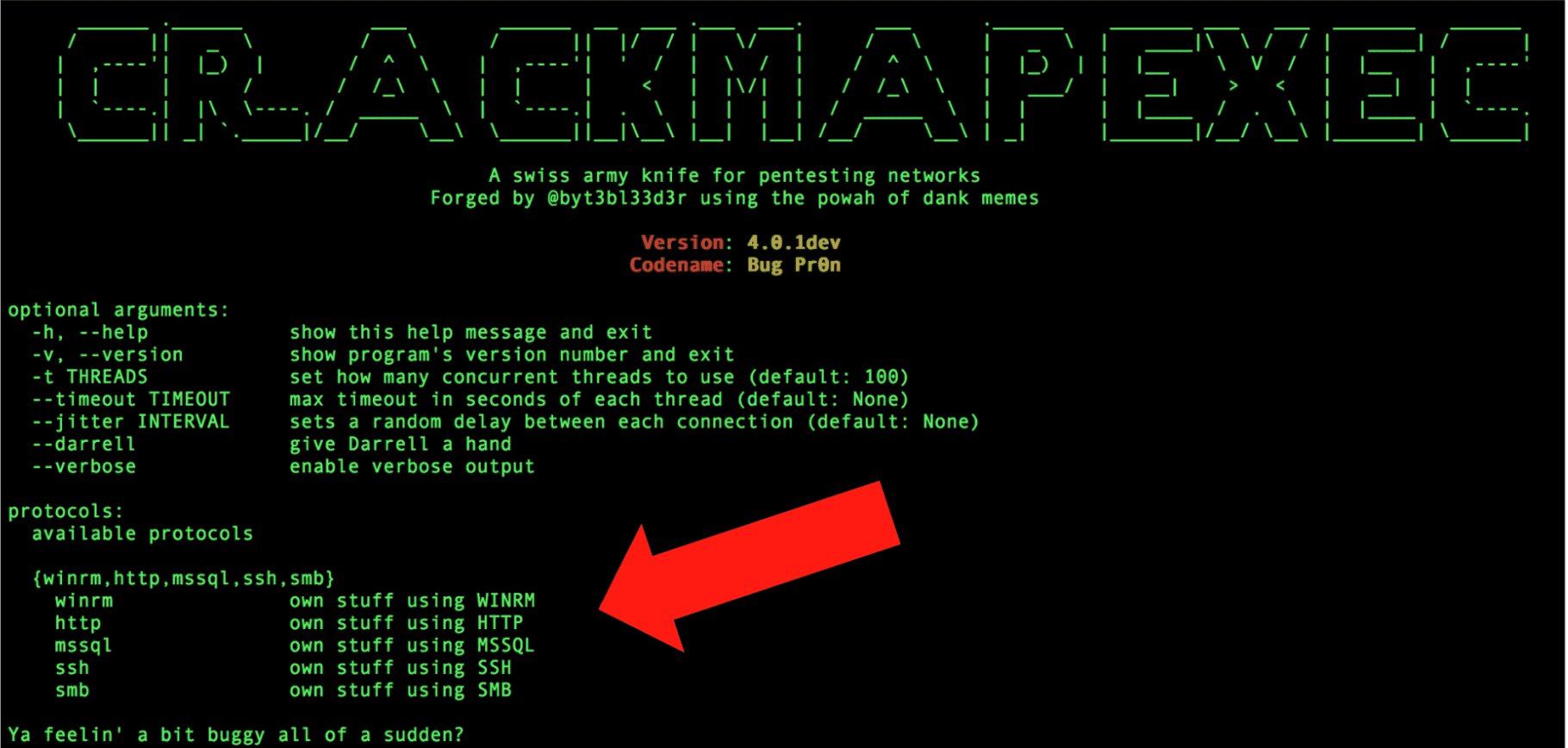
CRACKMAPEXEC CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of “Living off...
Radium-Keylogger Python keylogger with multiple features Feature –> Applications and keystrokes logging –> Screenshot logging –> Drive tree structure –> Logs sending by email –> Password Recovery for • Chrome...
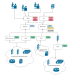
DeathStar is a Python script that uses Empire’s RESTful API to automate gaining Domain Admin rights in Active Directory environments using a variety of techinques. The following picture can be a good...
Invoke-Vnc executes a VNC agent in-memory and initiates a reverse connection, or binds to a specified port. Password authentication is supported. Execute agent remotely via WMI If you have authenticated...
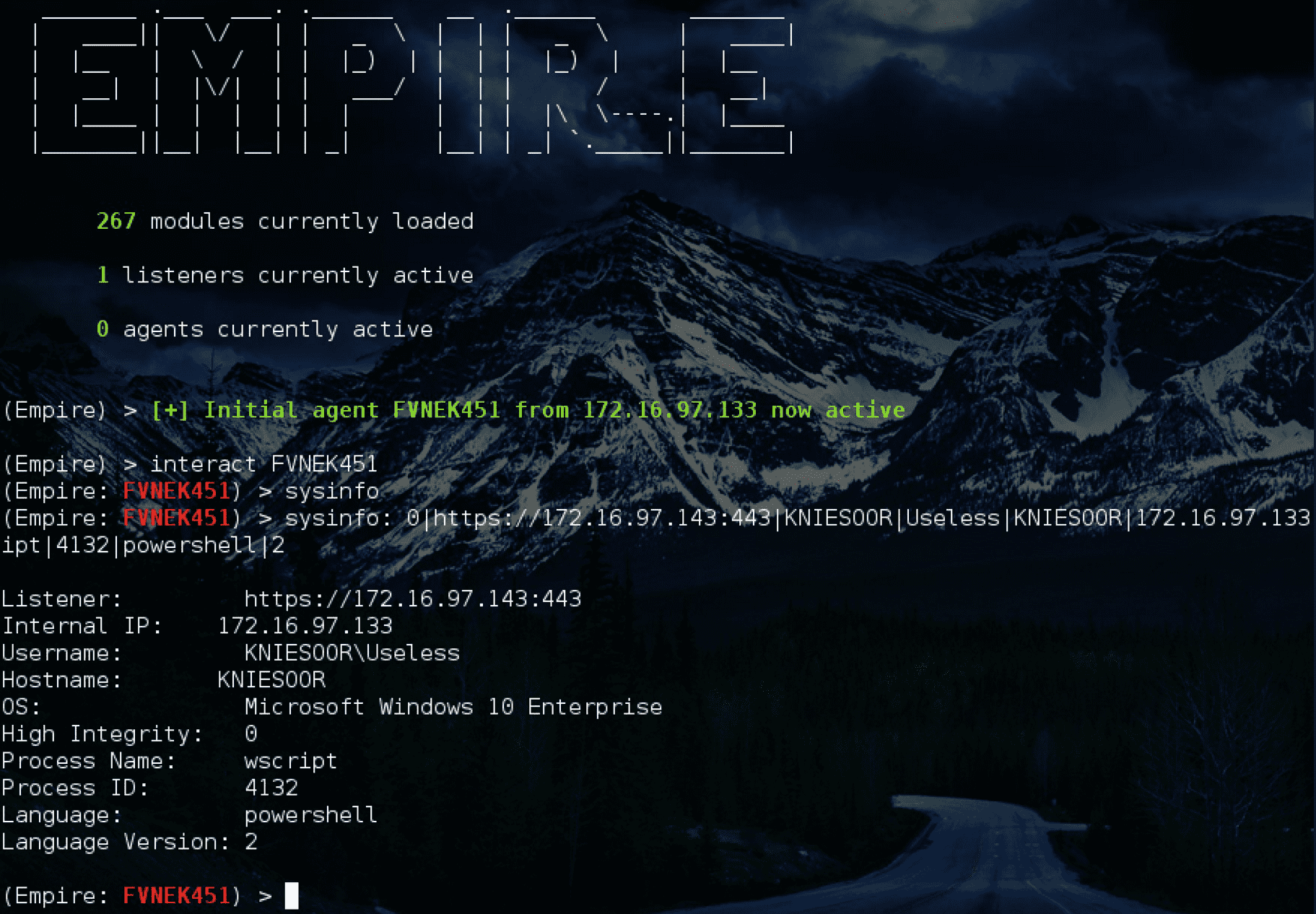
Empire is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent. It is the merge of the previous PowerShell Empire and Python...
exploit/windows/local/bypassuac_fodhelper module This module will bypass Windows 10 UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get...
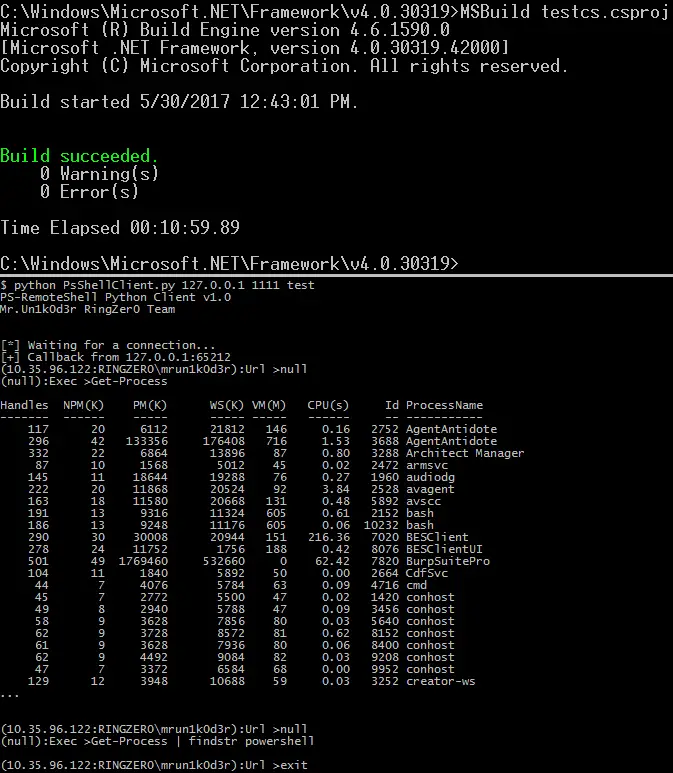
PowerLessShell rely on MSBuild.exe to remotely execute PowerShell scripts and commands without spawing powershell.exe. To add another layer of crap the payload will copy msbuild.exe to something random and build...
RedSnarf is a pen-testing / red-teaming tool by Ed William and Richard Davy for retrieving hashes and credentials from Windows workstations, servers and domain controllers using OpSec Safe Techniques. RedSnarf...
mimikittenz is a post-exploitation powershell tool that utilizes the Windows function ReadProcessMemory() in order to extract plain-text passwords from various target processes. mimikittenz can also easily extract other kinds of...
Hi, here is my first post. I want to list some great Windows command Enable RDP reg add “hklm\system\currentcontrolset\control\terminal server” /f /v fDenyTSConnections /t REG_DWORD /d 0 netsh firewall set...
What version of the system? What is its kernel version? What is the environment variables? Is there a printer? What services are running? What kind of service has what user...
PowerMemory: https://github.com/giMini/PowerMemory Exploit the credentials present in files and memory ReflectiveDLLInjection: https://github.com/stephenfewer/ReflectiveDLLInjection Reflective DLL injection is a library injection technique that is primarily used to perform the loading of a...