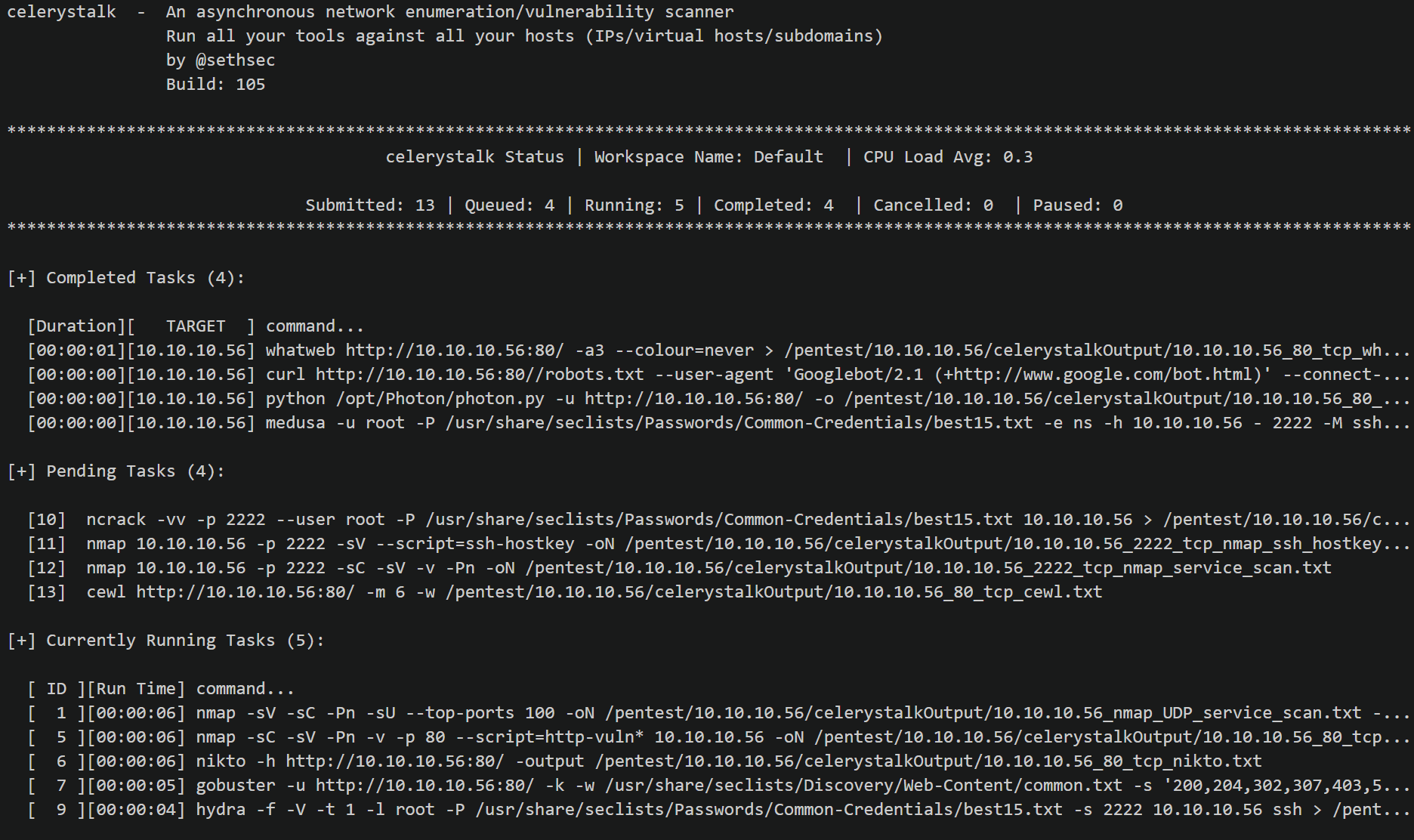
celerystalk
celerystalk helps you automate your network scanning/enumeration process with asynchronous jobs (aka tasks) while retaining full control of which tools you want to run.
- Configurable – Some common tools are in the default config, but you can add any tool you want
- Service Aware – Uses Nmap/Nessus service names rather than port numbers to decide which tools to run
- Scalable – Designed for scanning multiple hosts, but works well for scanning one host at a time
- VirtualHosts – Supports subdomain recon and virtualhost scanning
- Job Control – Supports canceling, pausing, and resuming of tasks, inspired by Burp scanner
- Screenshots – Screenshots (aquatone) every in-scope URL that was identified by any tool (you can limit # of screenshots if you’d like)
What celerystalk can automate for you
| Phase | Command | Examples of tools used |
|---|---|---|
| DNS Recon/Enumeration | ./celerystalk subdomains -d domain1,domain2 | Amass, sublist3r |
| Define Scope, Import nmap/nessus | ./celerystalk import [scan_data,scope_files,etc.] | celerystalk |
| Port Scanning | ./celerystalk nmap | nmap |
| Directory and File Enumeration, Vulnerability Identification | ./celerystalk scan | Gobuster, Nikto, Photon, sqlmap, wpscan, hydra, Medusa, wappalyzer, whatweb, etc. |
| Screenshots | ./celerystalk screenshots | Aquatone |
| Analysis | ./celerystalk report | celerystalk |
Changelog v1.3.1
- Updated gobuster in default config to run twice, once with append slash and once without
- Now that screenshots are no longer async, the report command will run the screenshots and then create report all in one.
Install
- Supported Operating Systems: Kali (Setup script supports Ubuntu, but for now you’re on your own for installing tools like gobuster, Nikto, etc…)
- Supported Python Version: 2.x
Use
[CTF/HackTheBox mode] – How to scan one host by IP only
[URL Mode] – How to scan a URL (scans the specified path, not the root).
[Vulnerability Assessment Mode] – How to scan a list of in-scope hosts/networks and any subdomains that resolve to any of the in-scope IPs
Copyright 2018 Seth Art
Source: https://github.com/sethsec/
