
Trend Micro’s latest analysis sheds light on the growing menace of fake software installers and cracked applications, which are increasingly being used to spread info stealers like LummaStealer and other malicious payloads. These threats exploit the allure of piracy and the trust users place in seemingly legitimate software sources.
Cybercriminals use fake installers to disguise malware as popular applications, targeting users seeking free alternatives to paid software. According to Trend Micro, “These malicious programs disguise themselves as legitimate applications, often appearing in search results or comments on platforms like GitHub“, making them seem credible.
Victims are often lured through deceptive means:
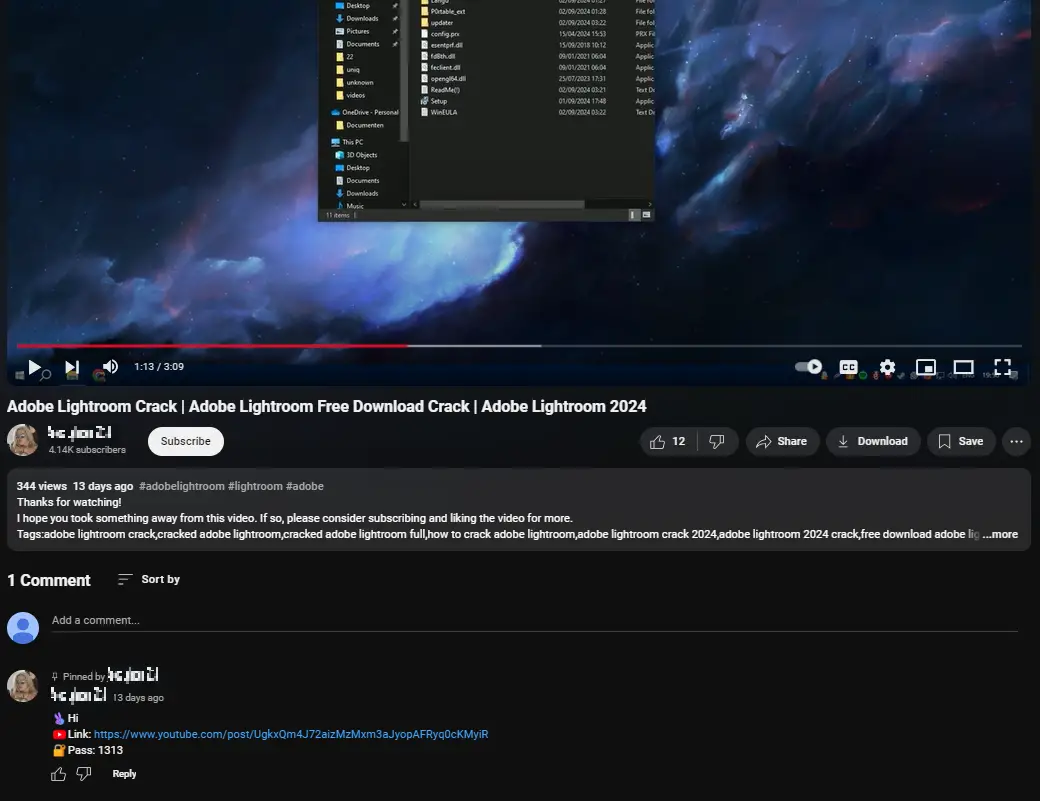
- YouTube Tutorials: Fraudsters pose as software installation guides, embedding malicious links in video descriptions.
- Search Results Manipulation: Keywords for popular software cracks lead users to fake links hosted on legitimate-looking platforms like OpenSea, SoundCloud, or Mediafire.
- Shortened Links and Password-Protected Archives: These tactics obscure malware and evade initial detection, complicating investigations.
The infection process begins when a user downloads and executes the malicious installer. Trend Micro highlights two real-world cases to showcase the attack chain:
- Case 1: After extracting a large, password-protected zip file, users unknowingly run an executable that spawns batch files, injects malicious code into legitimate processes, and establishes communication with command-and-control (C&C) servers.
- Case 2: A trojanized remote desktop application (RustDesk) installs additional malware, modifies registry entries for persistence, and silently runs in the background while appearing to have failed
In both cases, the malware employs DLL sideloading, process injection, and info stealers like MARSStealer, Vidar, and LummaStealer to exfiltrate sensitive information such as credentials and financial data.
The analysis highlights several evasion strategies used by attackers:
- Large File Sizes: Fake installers exceeding 900 MB can bypass sandbox analysis tools.
- Password-Protected Archives: These prevent automated scanning and delay investigation efforts.
- Legitimate File Hosting Services: Using platforms like Mega.nz and Mediafire adds credibility to the malware’s distribution.
- Code Injection into Legitimate Processes: This disguises malicious activity within trusted Windows applications, evading security defenses
Trend Micro urges users to exercise caution when seeking software online. “The hidden dangers of piracy that can jeopardize personal security and data integrity,” the report states.
Related Posts:
- Microsoft Announces Critical Change to .NET Installer Distribution Domains
- Micro Backdoor: Small and convenient C2 tool for Windows targets
- FakeBat Malware Surge Exposes the Dangers of Evolving Malvertising Campaigns
- Beware of Search Results: Hackers Using Fake Websites to Spread Malware