
Trend Micro has uncovered a targeted ransomware campaign conducted by a newly identified threat group dubbed CrazyHunter. The campaign zeroes in on critical infrastructure in Taiwan, specifically healthcare institutions, educational bodies, and industrial organizations—sectors where disruption could cause nationwide consequences.
The attackers employ a Bring Your Own Vulnerable Driver (BYOVD) technique, a method that enables the circumvention of advanced antivirus and endpoint detection tools. Central to this tactic is a customized process killer derived from the open-source project ZammoCide, which exploits the zam64.sys driver to neutralize defenses.
“The group uses a tailored variant of an open-source process killer tool called ZammoCide and adapts it to be an AV/EDR killer,” Trend Micro notes.
The campaign’s toolkit is overwhelmingly based on open-source software, with 80% of its components sourced from GitHub, including powerful tools like Prince Ransomware Builder and SharpGPOAbuse—used for lateral movement and privilege escalation via Group Policy Objects.
At the main of the attack is a Go-based ransomware variant, built using the Prince ransomware builder. The malware encrypts files using ChaCha20 and ECIES algorithms, appends the extension .Hunter, modifies the desktop wallpaper, and delivers a ransom note titled Decryption Instructions.txt.
To evade detection and maintain operational continuity, the ransomware strategically whitelists certain file extensions (e.g., .exe, .dll, .sys) and system directories (e.g., Program Files, System32, Windows)—allowing the OS to keep running while encrypting valuable data.
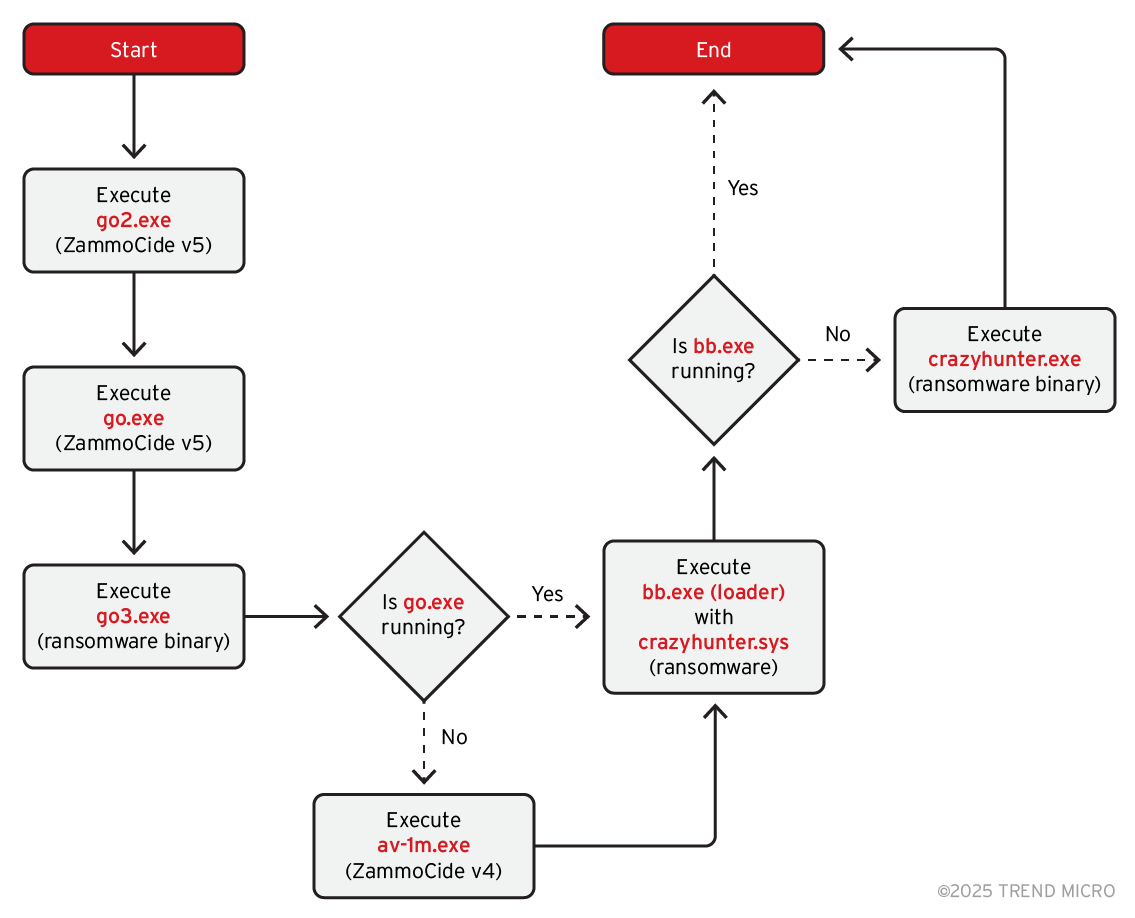
The group’s execution chain is highly resilient. It involves batch scripts that invoke multiple binaries (go2.exe, go.exe, bb.exe) in sequence to ensure successful ransomware deployment. If any component fails, alternatives are launched to maintain attack continuity.
“These redundant measures ensure that ransomware deployment remains effective even if primary methods fail,” the report explains.
Additionally, a utility named file.exe—another Go-based tool—operates in dual modes: monitoring web-related files for changes and acting as a web server for potential data exfiltration.
Trend Micro’s telemetry and the ransomware group’s own data leak site confirm the exclusive targeting of Taiwanese victims, particularly small and medium-sized enterprises (SMEs).
“Our internal data also reveals that this group exclusively targets small and medium-sized businesses within Taiwan,” the report notes.
Even the ransom note features a region-specific contact email—payment.attack-tw1337@proton[.]me—emphasizing their deliberate focus.
Related Posts:
- Threat Actor Deploys LummaC2 and Rhadamanthys Stealers in Attacks on Taiwanese Facebook Accounts
- CVE-2025-0289: Paragon Partition Manager Flaw Exploited in BYOVD Ransomware Attacks
- Unpacking Kasseika: The Latest Ransomware to Exploit BYOVD Tactics
- New Report Reveals SmokeLoader’s Advanced Tactics in Taiwan Campaign
