
A critical vulnerability has been unearthed in PyTorch, one of the most beloved deep learning frameworks out there. Security researcher Ji’an Zhou has identified a critical Remote Command Execution (RCE) flaw in one of the most trusted functions used by developers to safely load models — even when configured for security.
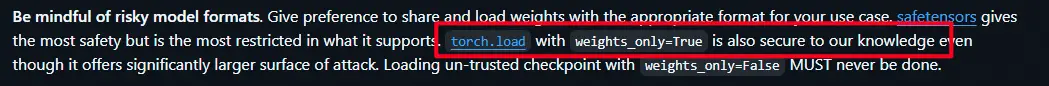
The vulnerability, tracked as CVE-2025-32434, carries a CVSS v4 score of 9.3, making it a critical security issue. It affects PyTorch versions ≤2.5.1 and resides in the torch.load() function — specifically when invoked with the parameter weights_only=True.
For those unfamiliar, PyTorch, now under the Linux Foundation umbrella after its initial development by Meta AI, is a powerhouse for applications ranging from crafting intelligent computer vision systems to understanding the nuances of natural language. Its free and open-source nature, coupled with a user-friendly Python interface, has made it a go-to choice for researchers and developers worldwide.
“Since everyone knows that weights_only=False is unsafe, they will use the weights_only=True to mitigate the security issue,” noted Zhou. “But now, I just proved that even if you use weights_only=True, it still can achieve RCE.”
If a malicious actor crafts a model file designed to exploit this flaw, they can execute arbitrary commands on the target machine — potentially leading to data breaches, system compromise, or even lateral movement in cloud-hosted AI environments.
And because many developers trust weights_only=True as a safeguard, the exploit may succeed in environments where security practices are otherwise in place.
The good news is that the PyTorch team has swiftly addressed this critical issue. A patched version, 2.6.0, is now available. Therefore, the immediate and most crucial step you must take is to update your PyTorch installation to version 2.6.0 or higher.
Here’s how you can typically update PyTorch:
Using pip:
Using conda:
