CVE-2022-22980: Spring Data MongoDB SpEL Expression injection vulnerability
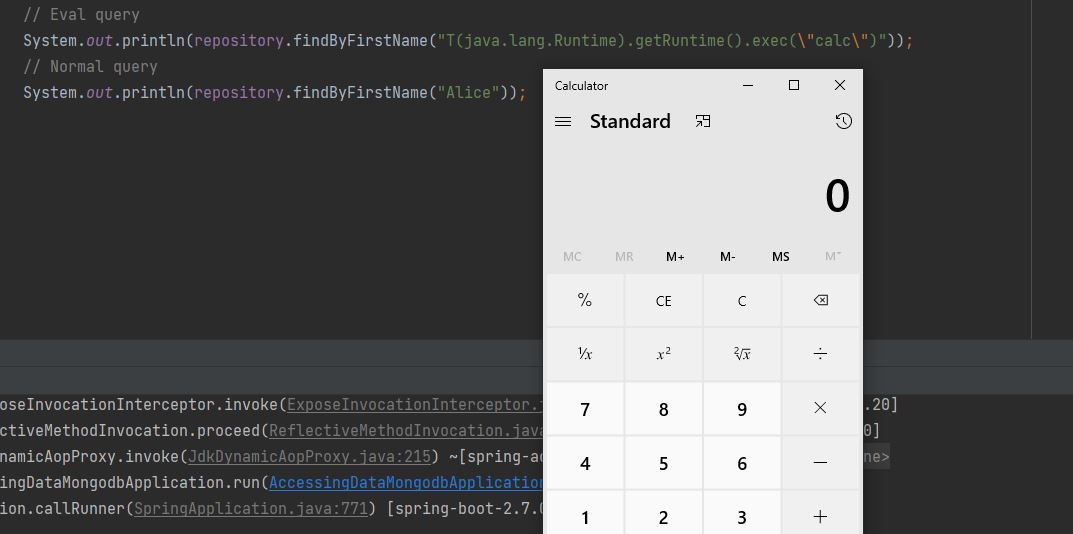
Recently, VMware issued a security bulletin to disclose a SpEL Expression injection vulnerability (CVE-2022-22980) in Spring Data MongoDB. This flaw’s severity is high. The vulnerability affects Spring Data MongoDB applications using repository query methods that are annotated with @Query or @Aggregation and use parametrized SpEL statements. A specific exploit requires the usage of non-sanitized input to the repository query method. This vulnerability was responsibly reported by Zewei Zhang from NSFOCUS TIANJI Lab on Monday, June 13, 2022.

The Spring Data MongoDB project provides integration with the MongoDB document database. Key functional areas of Spring Data MongoDB are a POJO centric model for interacting with a MongoDB DBCollection and easily writing a Repository style data access layer.
VMware said that the CVE-2022-22980 is impacted if three conditions are true
- A repository query method is annotated with @Query or @Aggregation
- The annotated query or aggregation value/pipeline contains SpEL parts using the parameter placeholder syntax within the expression
- The user-supplied input is not sanitized by the application
A remote attacker can execute arbitrary code on the target system. Successful exploitation of this vulnerability may result in a complete compromise of a vulnerable system. There are many proof-of-concept [1,2] (PoC) exploit codes for this bug.
Affected version
- Spring Data MongoDB
- 3.4.0
- 3.3.0 to 3.3.4
- Older, unsupported versions are also affected
At present, the new Spring Data MongoDB version has been released (3.4.1+ and later & 3.3.5+ and later) to fix the CVE-2022-22980 vulnerability, please upgrade to the unaffected version as soon as possible. We encourage users and administrators to review this flaw and follow the mitigation:
- Rewrite query or aggregation declarations to use parameter references (“[0]” instead of “?0“) within the expression
- Sanitize parameters before calling the query method
- Reconfigure the repository factory bean through a BeanPostProcessor with a limited QueryMethodEvaluationContextProvider