
Check Point Research has issued a warning over the active exploitation of a newly disclosed vulnerability—CVE-2025-24054—that allows attackers to leak NTLMv2-SSP hashes through specially crafted .library-ms files. The vulnerability, which Microsoft patched on March 11, 2025, affects all supported versions of Windows and has already been weaponized in the wild less than two weeks after disclosure.
The flaw enables NTLM hash disclosure via spoofing and is triggered simply by interacting with a malicious .library-ms file. “This event will trigger Windows Explorer to initiate an SMB authentication request to a remote server and, as a result, it leaks the user’s NTLM hash without any user interaction,” the report states.
Unlike traditional attack vectors that require users to open or execute files, CVE-2025-24054 can be exploited through passive interactions such as right-clicking, drag-and-dropping, or merely navigating to the folder containing the malicious file.
Despite Microsoft’s timely patch, attackers moved quickly. “Threat actors began actively exploiting CVE-2025-24054 just eight days after the patch was released,” Check Point confirmed.
The exploitation campaign, dubbed NTLM Exploits Bomb, was first detected around March 20–21, 2025, targeting government and private organizations in Poland and Romania. Victims received Dropbox-hosted archives via malspam. Once extracted, these archives initiated NTLM hash leaks to attacker-controlled SMB servers hosted across Russia, Bulgaria, the Netherlands, Australia, and Turkey.
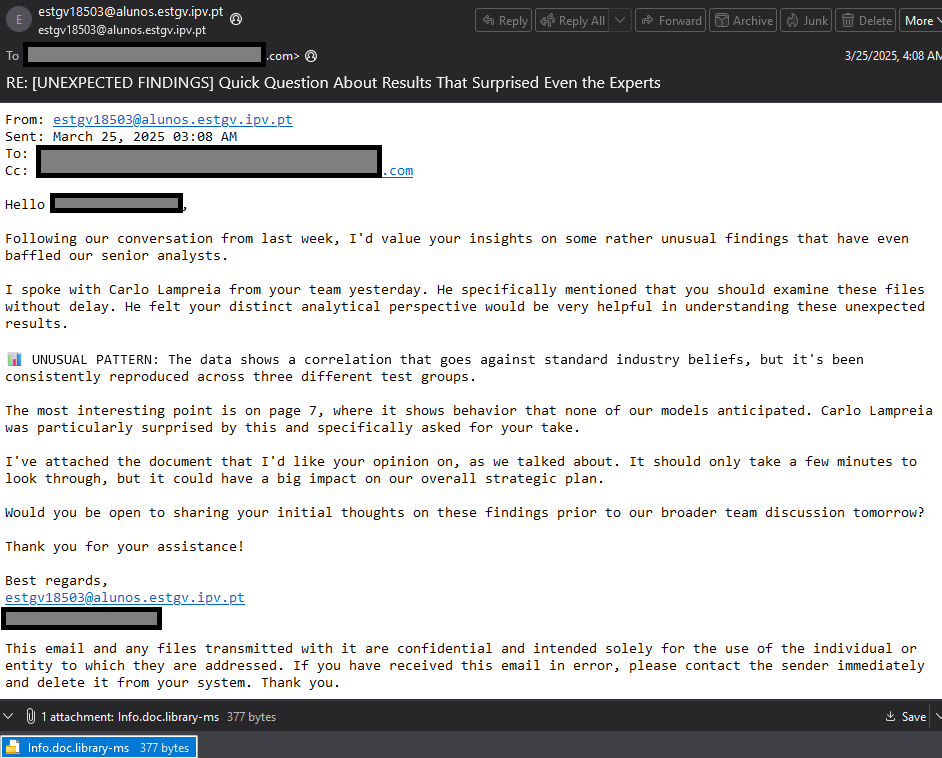
The malicious .zip files typically contained:
- xd.library-ms – exploited CVE-2025-24054
- xd.url – reused CVE-2024-43451, previously linked to Russian APT group UAC-0194
- xd.website and xd.lnk – also capable of triggering SMB authentication requests
Worryingly, attackers have evolved beyond archived payloads. By March 25, Check Point identified a campaign distributing .library-ms files outside of ZIP archives, making them triggerable with minimal interaction, such as hovering or single-clicking in a file browser.
Captured hashes were transmitted to IP addresses like 159.196.128[.]120 and 194.127.179[.]157. The former has previously been tied to APT28 (Fancy Bear), though Check Point noted that attribution in this case remains unconfirmed.
Additionally, several email addresses tied to academic institutions were found to be involved in distribution, indicating possible compromise or misuse of student accounts for global phishing operations.
NTLM hash disclosure vulnerabilities—particularly when exploited via near-zero-interaction methods—represent a severe risk to enterprise security. These hashes can be:
- Brute-forced offline
- Relayed in pass-the-hash attacks
- Used for privilege escalation and lateral movement, especially if the stolen credentials belong to privileged users
As Check Point concludes: “The minimal user interaction required for the exploit to trigger and the ease with which attackers can gain access to NTLM hashes make it a significant threat.”
Organizations should take immediate steps to protect against CVE-2025-24054 and similar threats:
- Apply the latest Microsoft patch (March 11, 2025)
- Block outbound SMB connections to untrusted networks
- Enable SMB signing and NTLM relay protections
- Disable automatic previews and navigation for untrusted file types
Related Posts:
- PoC Released: Windows Explorer CVE-2025-24071 Vulnerability Exposes NTLM Hashes
- Critical Microsoft Access Vulnerability Exploited for NTLM Token Theft
- Microsoft Strengthens Default Security Posture Against NTLM Relay Attacks
