Image: Knownsec 404 Advanced Threat Intelligence Team
A recent investigation by the Knownsec 404 Advanced Threat Intelligence Team has uncovered a new wave of sophisticated cyberattacks launched by the infamous DarkHotel APT group. Leveraging advanced techniques including modular RPC-based execution, double-layer DLL injection, and system file mimicry, the operation marks another evolution in this group’s ever-advancing cyber arsenal.
The DarkHotel organization first came to the attention of security vendors in 2014, with activities reportedly dating back to 2010. The group gained notoriety for targeting business executives and state dignitaries staying in luxury hotels, hence the name “DarkHotel”. While their initial focus was on the hotel industry, the Knownsec 404 team has observed a shift in their targets in recent years. DarkHotel now targets a broader range of sectors, including foreign trade, government agencies, research institutions, and military industries. The report emphasizes that DarkHotel is “one of the APT groups that frequently launch attacks against neighboring countries“. Their attack targets include China, North Korea, Japan, Myanmar, India, and several European countries.
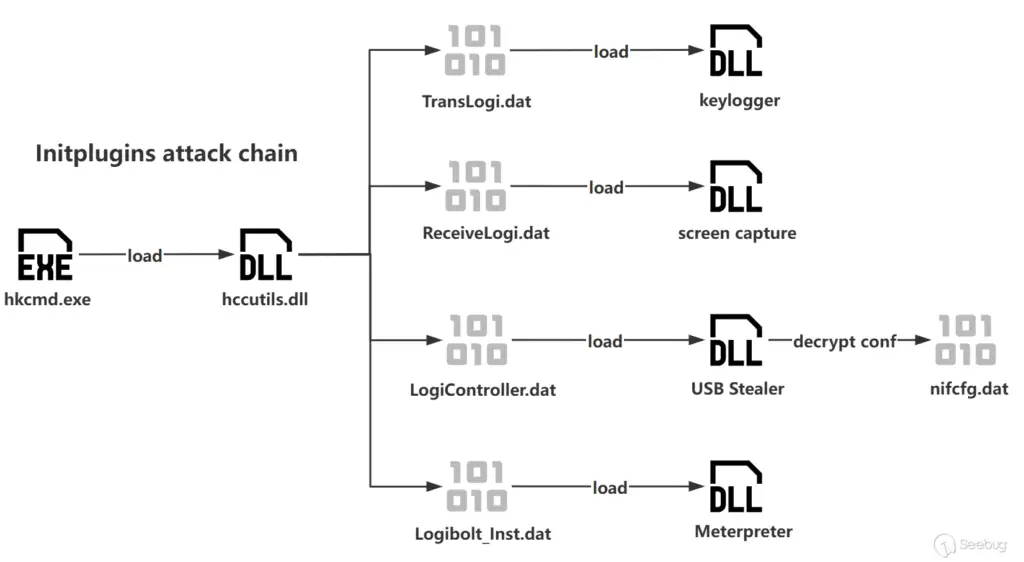
The latest attack activity captured by the Knownsec 404 team utilized Microsoft-signed system programs to side-load malicious DLL files, ultimately leading to the decryption and loading of malicious components. Interestingly, the report notes that “Compared to the InitPlugins framework used by the organization discovered in 2023, the framework has been upgraded in this attack activity“.
The report underscores DarkHotel’s sophisticated approach to cyberattacks. The group exhibits high anti-detection capabilities, capable of carrying out attacks “even with active defense and antivirus software running on victim hosts“. The attackers demonstrate proficiency in MFC-related loading mechanisms and possess “extremely strong coding abilities“. Their code incorporates various obfuscation techniques and a dual-layer injection mechanism, increasing the difficulty of analysis and concealing their activities while ensuring the stability of the injected code.
DarkHotel employs a modular loading approach, disguising encrypted module files as system files. To enhance deception, “they even modified the timestamp of the disguised files to match the timestamp of the system file kernel32.dll,” a tactic designed to make the malicious files appear legitimate. Furthermore, the attackers utilize RPC technology to execute component functions, separating communication components from functional components and using different scheduled tasks to maintain persistence.
The captured attack involved several components, including keyloggers, screen capture tools, USB stealers, and the Meterpreter framework. Knownsec’s analysis reveals a strong connection to previous DarkHotel activities. Specifically, “The components loaded in this captured attack activity are identical to those used in the 2023 initplugins attack activity“. Additionally, the attackers continue to use XOR algorithms for encryption and decryption, a hallmark of DarkHotel operations. These similarities in tactics, techniques, and procedures (TTPs) lead Knownsec to conclude “with high confidence that the samples captured this time are the work of the DarkHotel organization“.
The report highlights an important evolution in DarkHotel’s tactics. “Compared to previous attack activities of this organization, this time DarkHotel has separated the remote control component (meterpreter) from functional components (keyboard logging, screen capture, and USB theft) for separate loading and operation“. Knownsec suggests that this separation may be an attempt to improve the resilience of their attacks, preventing the failure of the entire operation if a single component is detected.
Related Posts:
- Patchwork Group Expands Cyber Espionage with Advanced Tools
- Stealthy New Golang Trojan Exploits Fake Certificates for Evasive Communication
- Google Releases Major Update and Open Source Component for Material Design Language