Detect MS17-010 SMB vulnerability using Metasploit
What is MS-17-010?
Remote code execution vulnerabilities exist in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerabilities could gain the ability to execute code on the target server.
To exploit the vulnerability, in most situations, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv1 server.
Detect MS17-010 SMB vulnerability using Metasploit
- Update Metasploit
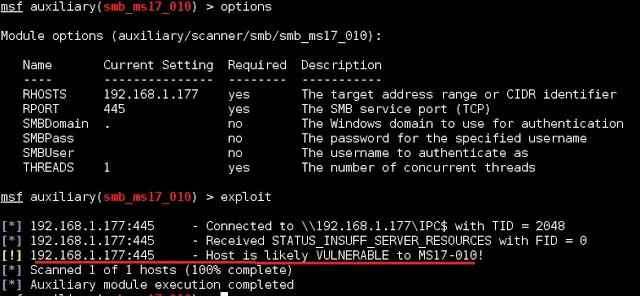
- Open msfconsole, use module auxiliary/scanner/smb/smb_ms17_010. Set RHOSTS and RPORT parameter.
Module info:Uses information disclosure to determine if MS17-010 has been patched or not.
Specifically, it connects to the IPC$ tree and attempts a transaction on FID 0.
If the status returned is “STATUS_INSUFF_SERVER_RESOURCES”, the machine does
not have the MS17-010 patch.
If the machine is missing the MS17-010 patch, the module will check for an
existing DoublePulsar (ring 0 shellcode/malware) infection.
This module does not require valid SMB credentials in default server
configurations. It can log on as the user “\” and connect to IPC$. - How to exploit, please read my post.





