adidnsdump – Active Directory Integrated DNS dump tool
By default, any user in Active Directory can enumerate all DNS records in the Domain or Forest DNS zones, similar to a zone transfer. This tool enables enumeration and exporting of all DNS records in the zone for recon purposes of internal networks.
For more info, read the associated blog post.
Install
pip install adidnsdump
Use
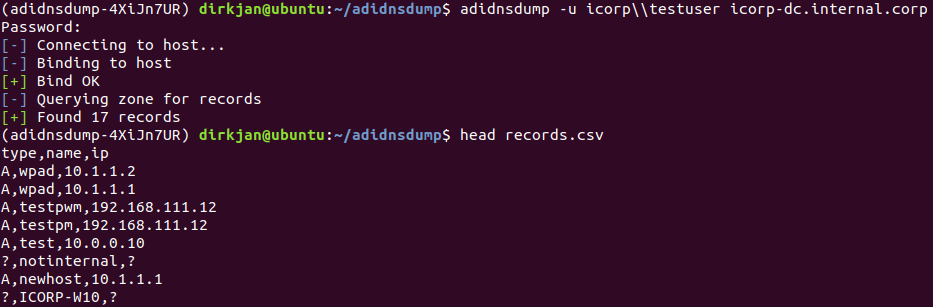
it is possible to enumerate all records in the DNS zone. To get started, first display the zones in the domain where you are currently in with –print-zones. This will show which zones are present. Not all zones are interesting, for example forward, cache and stub zones don’t contain all the records for that domain. If you find these zones, it’s better to query the domain to which they actually belong. The output below shows that my test domain has only the default zones:
If we specify the zone to the tool (or leave it empty for the default zone), we will get a list of all the records. Records which can be listed but not read (so-called “hidden” records) are shown but only with a question mark, as it is unknown which type of record is present and where it points to. The records are all saved to a file called records.csv.

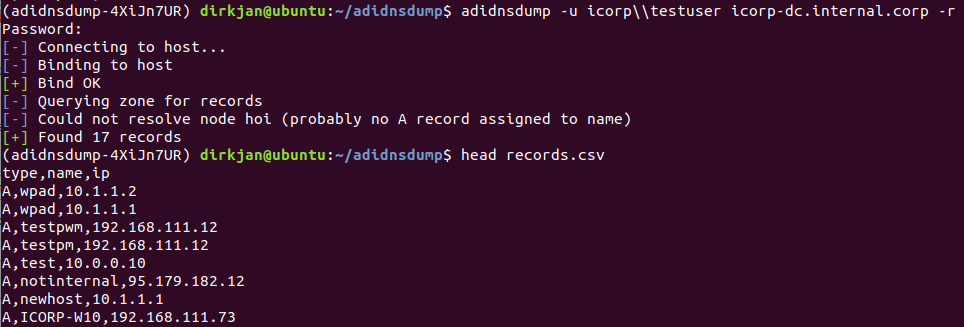
To resolve the unknown records, specify the -r flag, which will perform an A query for all unknown records (you can easily change this to AAAA in the code if you’re in an IPv6 network). Several nodes which were blank before now suddenly have records:
If you don’t have a direct connection but are working via an agent, you can proxy the tool through socks and perform the DNS queries over TCP with the –dns-tcp flag.
Copyright (c) 2019 Dirk-Jan
Source: https://github.com/dirkjanm/