Huntress, a prominent cybersecurity firm, has recently uncovered a new wave of malicious activities involving the well-known SocGholish or FakeUpdates malware. The attackers have recently been observed leveraging the legitimate BOINC (Berkeley Open Infrastructure Network Computing) software to establish a foothold in compromised systems.
SocGholish has traditionally relied on deceptive browser update prompts to trick users into downloading malware. However, Huntress has discovered a new infection chain where, following the initial compromise, SocGholish is not only deploying common Remote Access Trojans (RATs) but also installing and misusing BOINC.
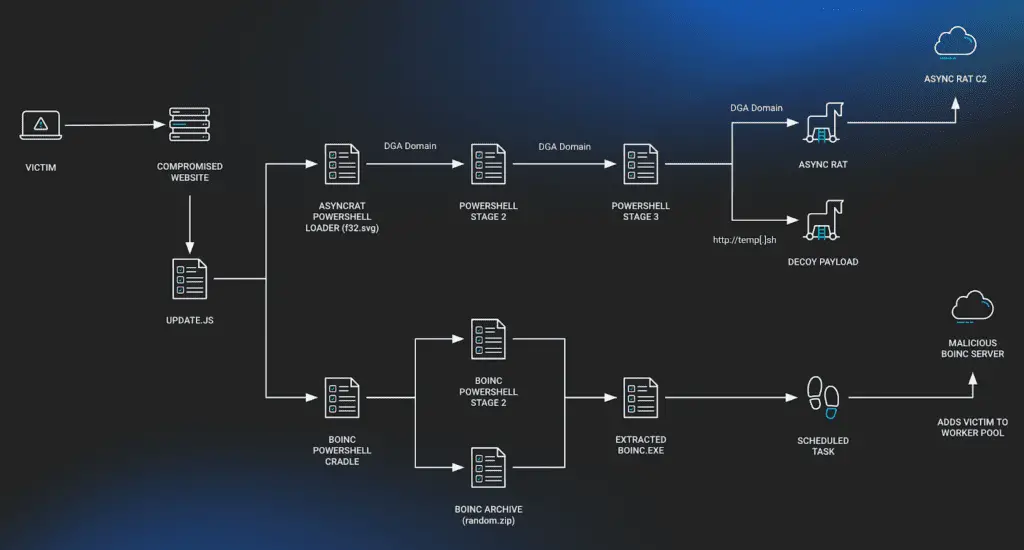
The infection chain observed by Huntress begins with a malicious JavaScript file responsible for downloading subsequent stages. Interestingly, this time there are two distinct chains:
- Fileless AsyncRAT Installation: In this chain, heavily obfuscated PowerShell loaders bypass security measures and install a fileless version of AsyncRAT.
- Malicious BOINC Installation: The other chain leads to the installation of BOINC, a software platform designed for volunteer computing. However, instead of connecting to legitimate projects, the compromised BOINC connects to malicious servers.
BOINC, typically used for volunteer computing projects, is being hijacked by SocGholish to create a covert command-and-control (C2) channel. By connecting victims’ machines to rogue BOINC servers, attackers can exfiltrate data, deliver additional malware, or perform other malicious activities.
Huntress noted that despite the unusual use of BOINC, no additional malicious tasks were executed by the infected hosts. However, the presence of a malicious C2 infrastructure poses significant risks, including the possibility of ransomware deployment or further system compromises. The BOINC Project Administrators are aware of this misuse, as similar behaviors have been discussed in their forums since late June 2024.
To avoid falling victim to these scams, users are urged to exercise caution when encountering browser update prompts. Always download updates directly from official vendor websites and keep security software up to date.
For more detailed information and mitigation strategies, refer to Huntress’s full report.