
A recent investigation by Sucuri revealed a sophisticated credit card skimming attack on a WordPress website. The attack involved the injection of a malicious script that created a fake credit card form and used a deceptive domain to exfiltrate stolen data.
The website owner contacted Sucuri due to concerns about credit card theft, with users reporting unauthorized charges shortly after making purchases. Sucuri’s investigation uncovered two key indicators of compromise: a strange credit card form and an unfamiliar domain on the website’s checkout page. The suspicious domain, italicfonts[.]org, initially appeared to be related to fonts. However, an online search yielded no evidence of legitimate use, prompting further scrutiny.
Digging deeper, Sucuri’s team found a heavily obfuscated script in the theme’s footer.php file, containing the suspicious domain. The file’s recent modification date, which differed from other files in the theme, raised a red flag.
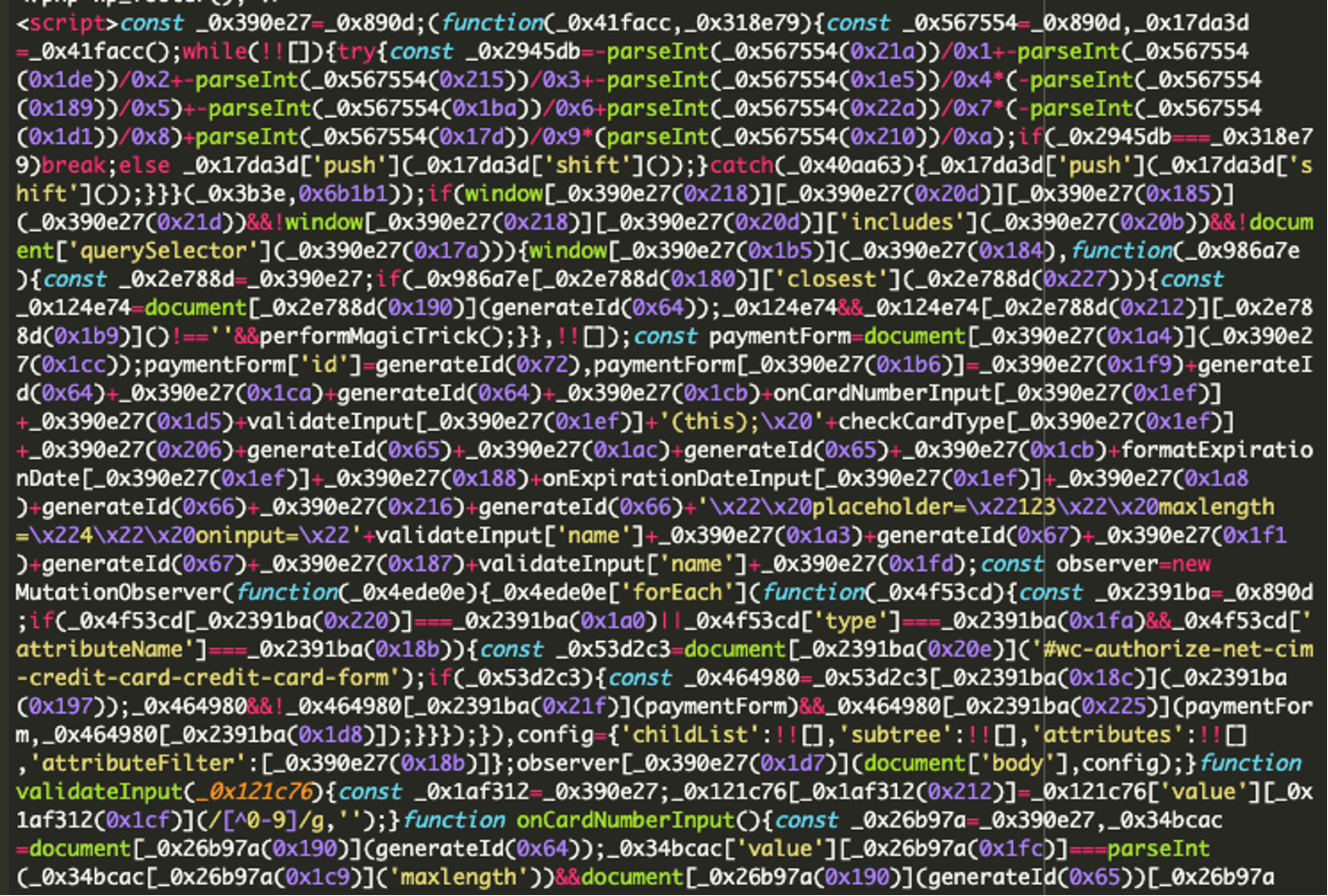
The injected script was designed to steal credit card information through the following steps:
- Injecting the malicious domain (italicfonts[.]org).
- Creating a fake credit card form on the checkout page.
- Capturing input events from the credit card fields and storing the data.
- Sending the stolen credit card details to the attacker’s server.
The attackers employed several tactics to evade detection. The choice of the domain “italicfonts[.]org” was particularly cunning. As the report states, “To avoid detection even further, the attacker chose a domain mimicking a real font website“. This helped the domain blend in and appear legitimate at first glance.
Sucuri used several techniques to confirm the malicious nature of the domain. A Google search using “site:italicfonts.org” revealed no indexed pages, which is unusual for a legitimate website. Additionally, the domain was registered only a few months prior to the attack, a common tactic used by attackers to avoid detection. As the report states, “New domains can be a sign of malicious behavior as attackers cycle through domains quickly to avoid detection as long as possible“.
The injected script also created a fake credit card form that closely resembled the legitimate checkout form. This form included fields for billing information and card details, designed to deceive users into entering their sensitive information. As the report states, “The form is designed to mimic real payment fields to make it look legitimate upon checkout“.
The consequences of such an attack can be severe. Credit card theft can lead to financial losses for customers and significant reputational damage for the affected business. As the report emphasizes, “Credit card theft can have serious consequences and damage a business’s reputation“. The loss of customer trust can result in decreased sales, lost customers, and potential legal repercussions.
Related Posts:
- Credit Card Skimmer and Backdoor Found Lurking on WordPress E-commerce Site
- Stealthy Malware Campaign Switches Tactics, Targets WordPress Sites
- Credit Card Skimmer Malware Uncovered: Targeting Magento Checkout Pages
- Silent Skimmer Reemerges: New Tactics Target Payment Gateways
- Telegram: The Dark Horse of Website Malware Attacks