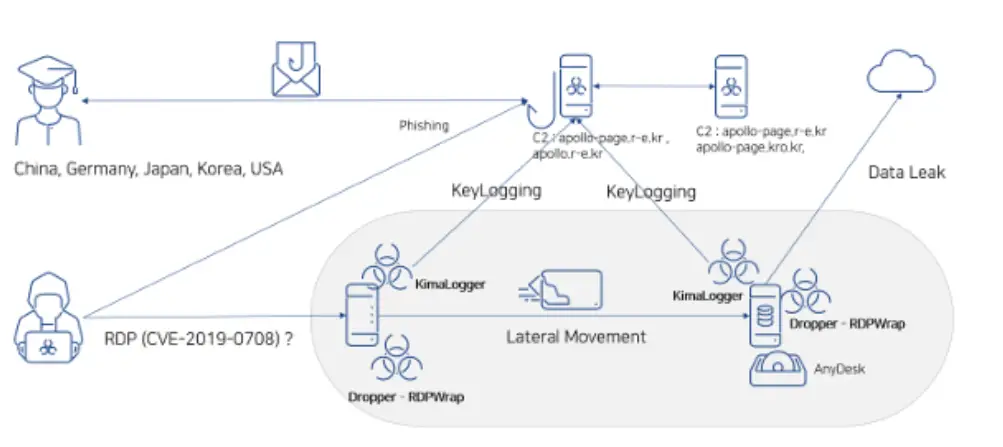
Attack Method | Image: ASEC
A new cybersecurity report from the AhnLab Security intelligence Center (ASEC) has shed light on a recently identified operation linked to the notorious Kimsuky group. Dubbed “Larva-24005,” this campaign demonstrates the group’s persistent evolution and their continued focus on high-impact cyber espionage.
The ASEC investigation, triggered by a breach, uncovered a disturbing pattern: threat actors leveraging Remote Desktop Protocol (RDP) vulnerabilities to infiltrate systems, establish persistent remote access, and exfiltrate sensitive data.
Since October 2023, the Larva-24005 group has been actively targeting a range of industries in South Korea, including software, energy, and finance. However, the scope of their operations extends far beyond the Korean peninsula. The ASEC analysis of the attackers’ infrastructure reveals a global footprint, with victims identified in countries across Asia, Europe, and North America. Specifically, the report indicates that these threat actors have been targeting South Korea, the United States, China, Japan, Germany, Singapore, and others since September 2023, also including South Africa, the Netherlands, Mexico, Vietnam, Belgium, the United Kingdom, Canada, Thailand, and Poland.
The Larva-24005 campaign employs a multi-stage attack methodology. Initial access is frequently gained through the exploitation of RDP vulnerabilities, including the infamous BlueKeep vulnerability (CVE-2019-0708). While the report notes the discovery of RDP vulnerability scanners on compromised systems, it also clarifies that the actual use of these tools for initial access isn’t always confirmed.
Phishing emails and the exploitation of Microsoft Office Equation Editor vulnerability (CVE-2017-11882) are also used to distribute malware.
Once inside a system, the attackers deploy a dropper to install the MySpy malware and RDPWrap, a tool that facilitates persistent remote access. To further their surveillance capabilities, the threat actors install keyloggers, such as KimaLogger or Random Query, to capture user keystrokes.
The ASEC report provides a detailed overview of the malware and tools employed by Larva-24005:
- RDPScanner (Type A & B): Command-line and GUI-based tools for scanning RDP vulnerabilities. The GUI version “reads the IP list from a text file and performs the scanning. The scan results are stored in the RDP_result.txt file in the tool’s execution path.”
- MySpy: Malware used for “estimation of system information collection”.
- RDPWrap: Tool used for establishing remote control.
- KimaLogger & Random Query: Keyloggers used to capture user input.
The Larva-24005 campaign highlights the Kimsuky group’s adaptability and their persistent focus on leveraging known vulnerabilities to achieve their objectives. The group’s use of RDP exploits, in conjunction with sophisticated malware, poses a significant threat to organizations across various sectors.
Related Posts:
- Silver Fox APT Targets Philips DICOM Viewers in Healthcare Espionage Campaign
- Google removes hundreds of Android apps that infected with Windows executable files
- Midnight Blizzard Targets 100+ Organizations in RDP Phishing Attack
- Rogue RDP: Abusing RDP for File Theft and Espionage
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
