
North Korea’s notorious Lazarus APT group has been observed employing advanced social engineering tactics in a campaign dubbed “Contagious Interview.” This operation targets job seekers on platforms like LinkedIn, Telegram, and Discord by masquerading as recruiters for prominent companies. The campaign utilizes the ClickFix technique, a deceptive method designed to trick victims into executing malicious code. The findings come from an in-depth analysis by Efstratios Lontzetidis, Cyber Threat Intelligence Researcher, and shed light on Lazarus’s evolving tactics.
Lazarus APT, a long-standing North Korean threat group, has been active since at least 2009 and is linked to the North Korean government’s Reconnaissance General Bureau. Known for financially motivated attacks, they target sectors such as cryptocurrency, financial institutions, and FinTech. Proceeds from these operations are believed to fund North Korea’s weapons programs.
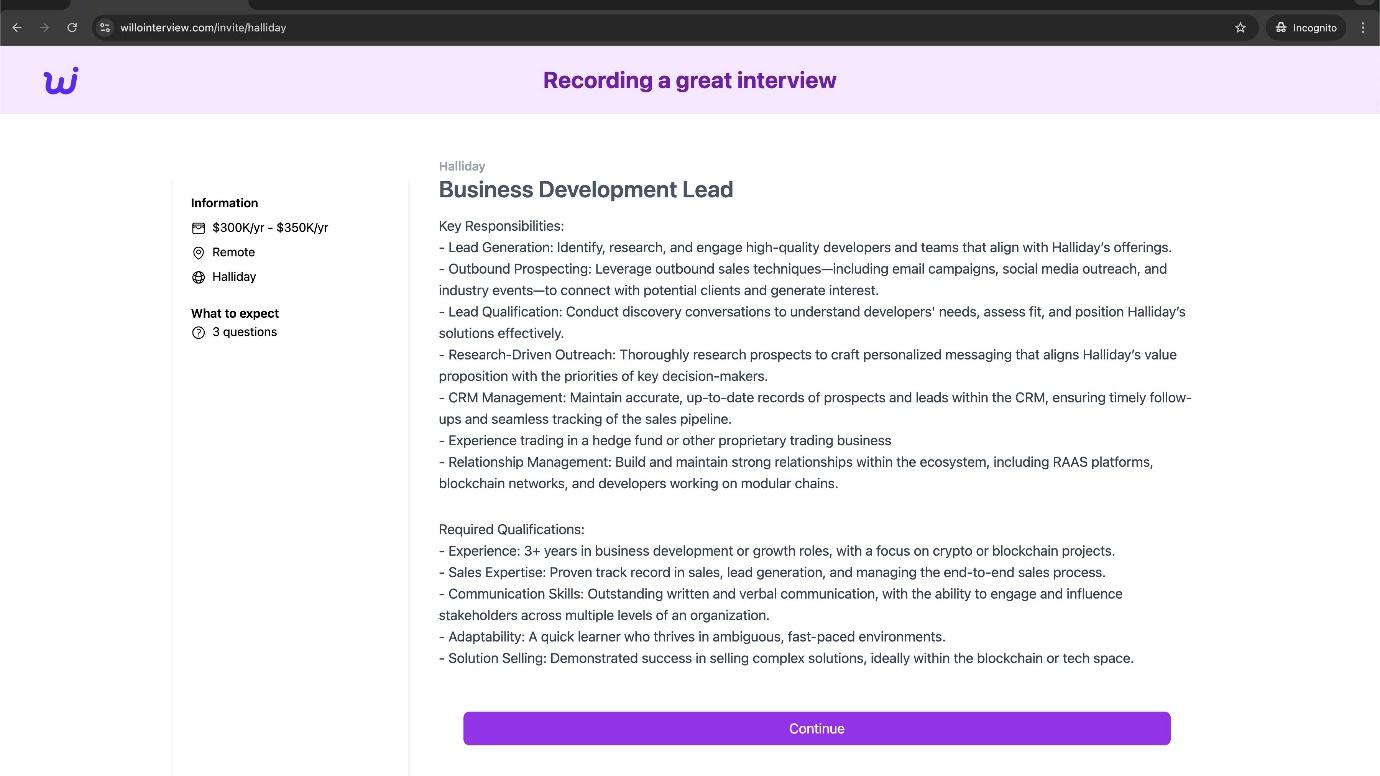
The Contagious Interview campaign, first identified in December 2022, leverages fake video job interviews to trick victims into installing malware. North Korean actors contact software developers through job search platforms, posing as prospective employers to lure them into downloading backdoor malware.
One of the standout tactics in this campaign is ClickFix, a social engineering method that uses fake error messages or verification steps to manipulate users into executing malicious commands. Victims are guided through pop-ups resembling reCAPTCHA or system prompts, asking them to copy and paste code into their terminals.
This sophisticated method ensures the malware payload remains inconspicuous until it’s executed by the user, targeting Windows, macOS, and Linux systems.
Campaign Details
- Initial Contact: Fake recruiters claiming to represent companies like Kraken, Meta, and Gemini offer attractive job opportunities.
- Malware Delivery: Victims are directed to a fraudulent video interviewing platform, willoassess[.]com, where the malware is delivered during “interview verification” steps.
- Payload Variants: Malware families deployed include BeaverTail, InvisibleFerret, and CivetQ, capable of credential theft, system reconnaissance, and persistence.
The report details an extensive investigation into the campaign’s supporting infrastructure. Using the Validin platform, researchers uncovered:
- Domains with naming conventions such as willo, talent, and blockchain linked to Lazarus campaigns.
- Hosting patterns across multiple Autonomous Systems, including AS 54290 (Hostwinds) and AS 30860.
- Connections between malicious domains and the legitimate Willo platform, identified via unique HOST-META headers.
Lontzetidis emphasizes, “It is up to us, security researchers to identify their behaviours and patterns and detect their infrastructure before it gets weaponized.”
For a detailed report and additional findings, visit Validin Threat Intelligence.
Related Posts:
- Beware of Fake Google Meet Invites: ClickFix Campaign Spreading Infostealers
- ClickFix: The Rising Threat of Clipboard-Based Social Engineering
- North Korean Threat Actors Targeting Tech Job Seekers with Contagious Interview Campaign
- North Korean Hackers Launch Job Interview Scam to Deploy BeaverTail and InvisibleFerret Malware
- Temptation from Money: Lazarus APT extended to cryptocurrencies