Nikto v2.5 releases – WebAPP Penetration Testing Tool
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
Nikto is not designed as a stealthy tool. It will test a web server in the quickest time possible and is obvious in log files or to an IPS/IDS. However, there is support for LibWhisker’s anti-IDS methods in case you want to give it a try (or test your IDS system).
Not every check is a security problem. Some items are “info only” type checks that look for things that may not have a security flaw, but Pentester may not know are present on the server. These items are usually marked appropriately in the information printed. There are also some checks for unknown items that have been seen scanned for in log files.
The goal of the project is to examine a web server to find potential problems and security vulnerabilities, including:
- Server and software misconfigurations
- Default files and programs
- Insecure files and programs
- Outdated servers and programs
- Pointers to lead a human tester to better manual testing
The vulnerability scanner discovers various issues that are potential security problems for your web server. The types of issues Nikto can identify are:
- Fingerprint the web server type and version
- Report old versions of server software if it contains known vulnerabilities
- Discover web server configuration problems (directory listing, backup files, old configuration files, etc)
- Identify specific web applications that are running on the web server
- Check for known application vulnerabilities
Changelog v2.5
This version contains hundreds of updates over several years, including the highlights below.
- IPv6 support (thanks to @richardleach)
- Updated
db_checksformat uses multiple reference - Hundreds of OSVDB and BID references replaced
- Removal of some very old and false-positive prone tests
- Decode Netscaler cookies (thanks to @canberkpolat)
- Add
-usecookiesflag to send received cookies with subsequent requests - Add
-followredirectsflag to signal 3xx responses should be fetched and tested - Add
-noslashto remove trailing slash from directories - Check for indexing on redirect paths
- Alert on
alt-svcheader - Hundreds of bug fixes, test updates and enhancements, and other optimization changes
Usage:
nikto -update #Directly update the database
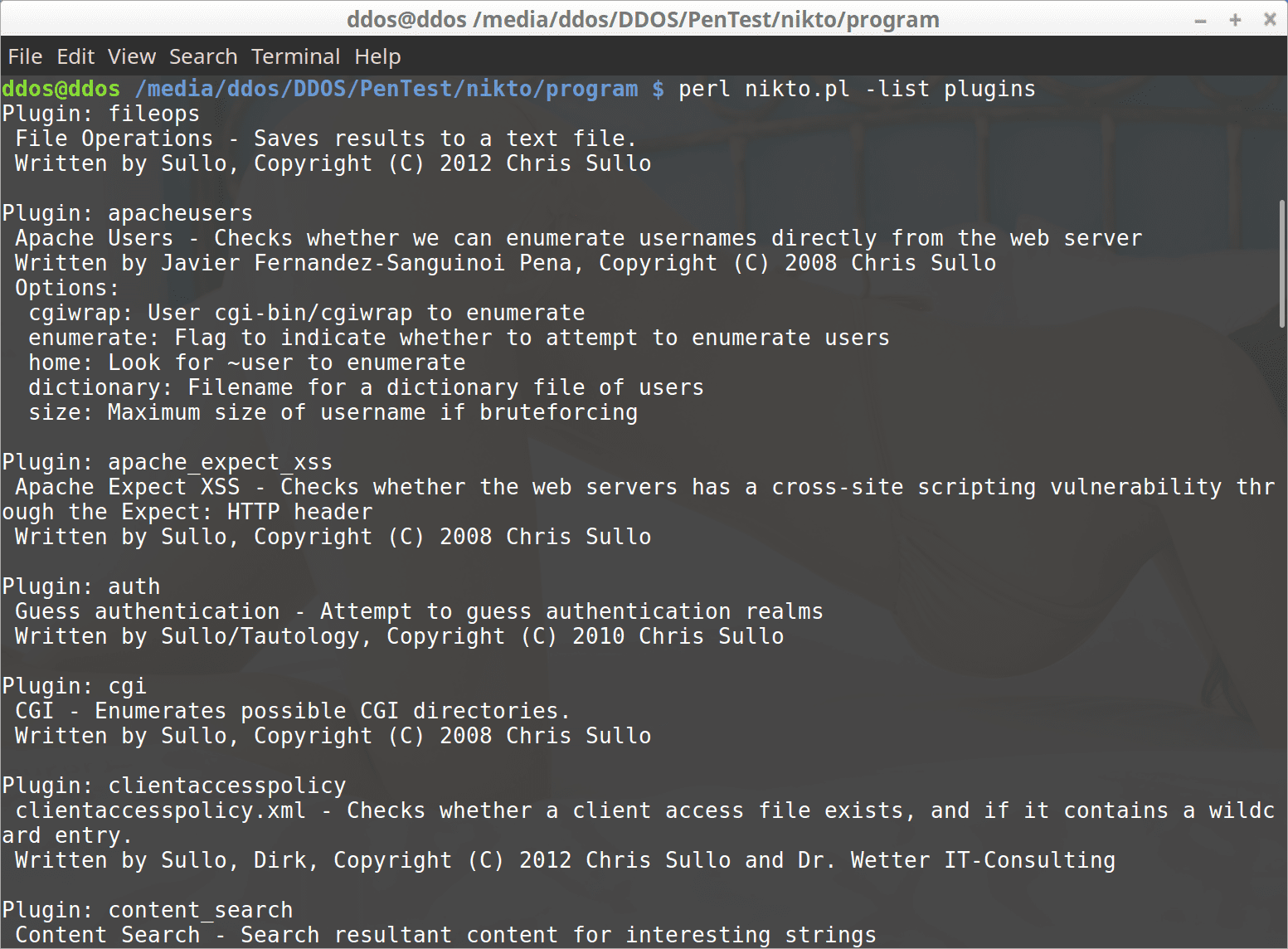
nikto -list-plugins #Plugin list
nikto -host http://192.168.1.16/DVWA/ #Specifies the site directory scan
nikto -host 192.168.1.1.109 -port 80,443 #Multiple ports can be specified
nikto –host target.txt #scanning multi target
nmap -p80 192.168.1.1/24 -oG – | nikto -host – #Combined with nmap, on a network segment of the open 80-port host scan
nikto –host https://securityonline.info -useproxy http://localhost:8080 #use proxy on your scanning
Interact with scanning mode
Scan tuning:
1 Interesting File / Seen in logs
2 Misconfiguration / Default File
3 Information Disclosure
4 Injection (XSS/Script/HTML)
5 Remote File Retrieval – Inside Web Root
6 Denial of Service
7 Remote File Retrieval – Server Wide
8 Command Execution / Remote Shell
9 SQL Injection
0 File Upload
a Authentication Bypass
b Software Identification
c Remote Source Inclusion
d WebService
e Administrative Console
x Reverse Tuning Options (i.e., include all except specified)
Encoding technique:
1 Random URI encoding (non-UTF8)
2 Directory self-reference (/./)
3 Premature URL ending
4 Prepend long random string
5 Fake parameter
6 TAB as request spacer
7 Change the case of the URL
8 Use Windows directory separator (\)
A Use a carriage return (0x0d) as a request spacer
B Use binary value 0x0b as a request spacer
You can configure nikto.conf
- Supports specified cookies
- Modify user agent





