North Korean hackers use Thai servers for stealing data from 17 countries
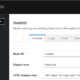
McAfee released a report on the details of the global hacking activity named “Operation GhostSecret.” The report shows that Hidden Cobra, a hacker group related to the North Korean government, uses servers in Thailand to conduct large-scale cyber espionage and malware attacks.
McAfee researchers said that Hidden Cobra’s attack on Turkish financial institutions from March 14 to 18 this year was only part of the operation. The final attack range spanned 17 countries, including Thailand, the United States, Germany, Japan, China, and Australia. The purpose of this series of hacking activities is to steal important data information from key global infrastructure (such as telecommunications, finance, medical, and entertainment organizations). After analysis, Operation GhostSecret is very complex. It uses a large number of implanted programs to steal information from the infected system, and the design is complex and complicated to escape the investigation and deception of forensic investigators.

In addition, the McAfee investigation found that the implant procedure included an unknown implant procedure similar to the Bankshot function. This new variant is similar to some of the Destover malware used in the 2014 hacker attacks on Sony Pictures. In addition, Hidden Cobra was also thought to have carried out Wanna Cry’s malware attack in May last year. The effects of this attack have spread all over the world.
At the same time, Computer Security Incident Response Team (ThaiCERT) announced on Wednesday that it has seized servers used by hacking activities and has handed them over to law enforcement agencies. It is reported that this server is located at the Thai National Legislative University in Bangkok, Thailand. This entity hosts the control server for the Sony Television implanter. This SSL certificate has been used to hide Cobra operations since Sony Pictures was attacked. Analyzing this certificate reveals that the attached control server uses the same Polar SSL certificate. Through further analysis of McAfee telemetry data, they identified several active IP addresses, two of which were in the same network segment as 2018 Destover-like implants.
Currently, McAfee is working with the Thai government authorities to cancel the “Operation GhostSecret” control server infrastructure while retaining the systems involved for further analysis by law enforcement agencies.