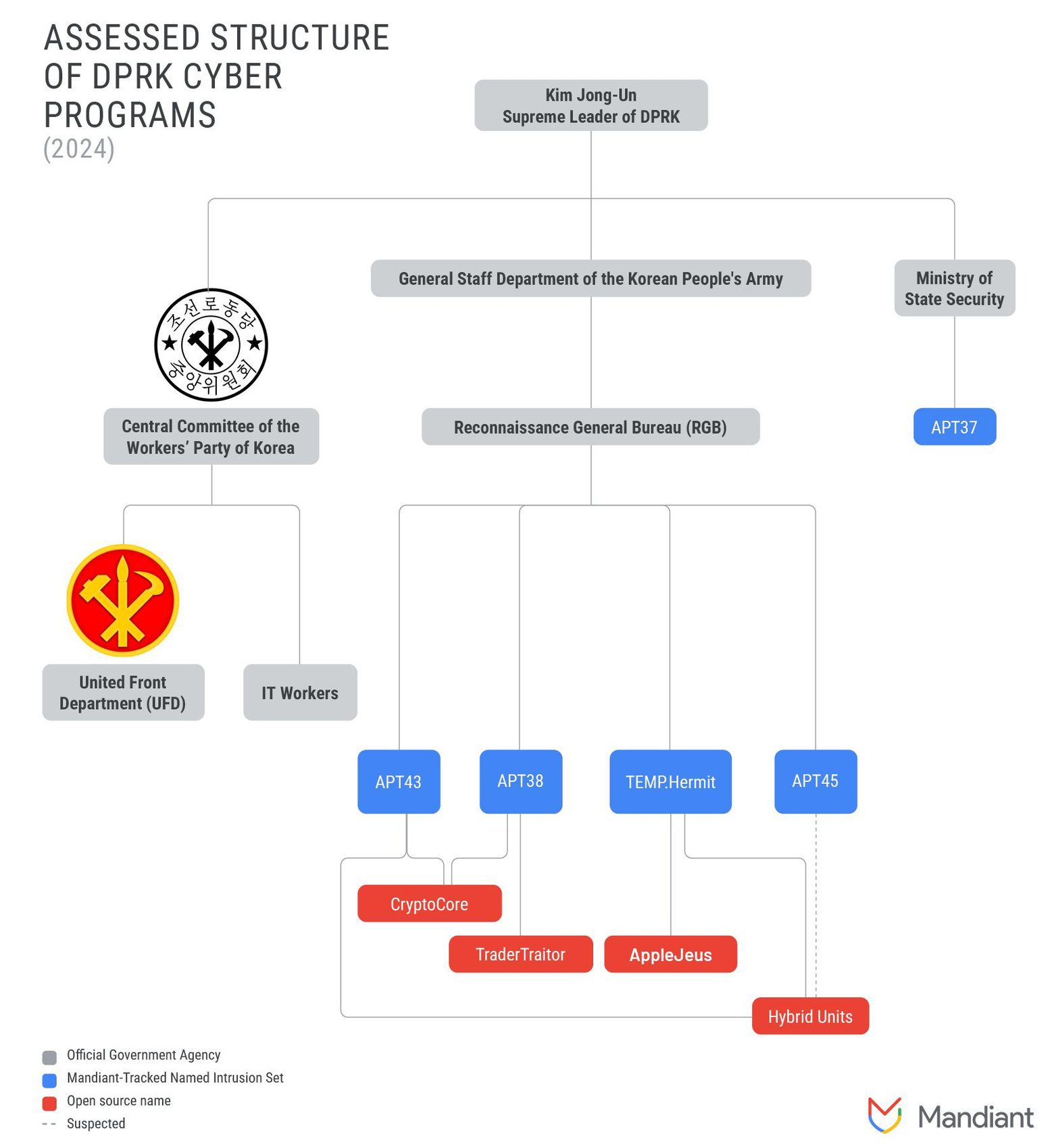
Assessed structure of DPRK cyber operations in 2024
The North Korean hacker group Andariel is accused of stealing confidential information and weapons blueprints from various countries worldwide. The cybersecurity company Mandiant has published the results of a two-year investigation into the group’s activities.
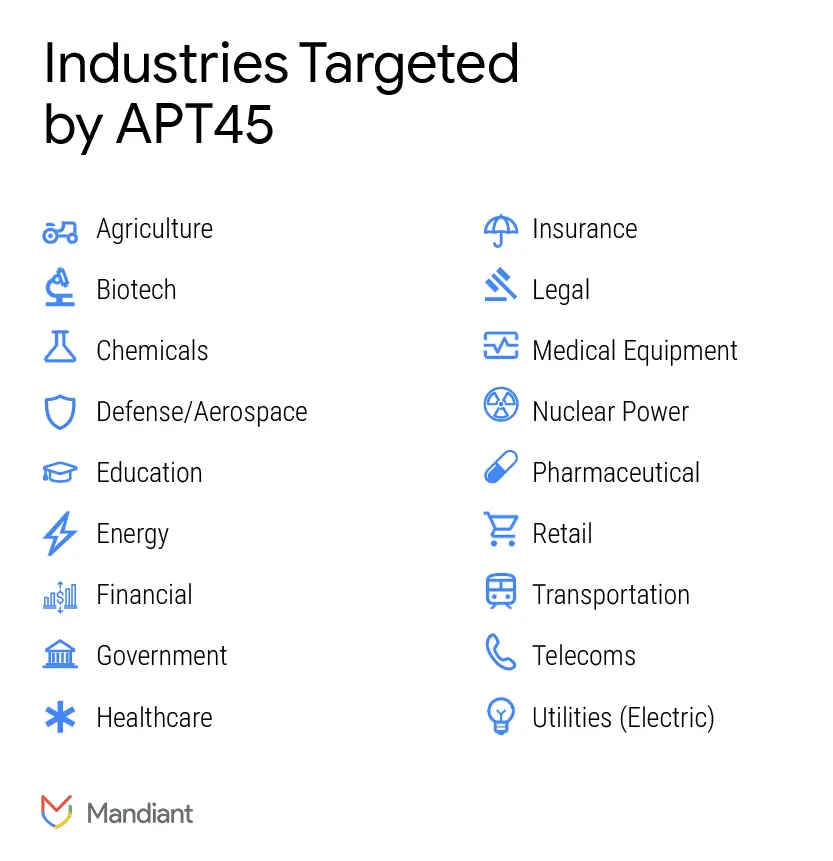
The investigation revealed that APT45 had stolen sensitive data on numerous weapon systems and technologies, including tanks, artillery, warships, submarines, drones, missiles, missile defense systems, satellites, and satellite communication systems.
Andariel conducted large-scale cyberattacks on critical infrastructure, surpassing traditional governmental espionage. In recent years, the group has also engaged in ransomware attacks on hospitals, banks, and defense companies in South Korea.
According to Mandiant, many of North Korea’s military achievements can be directly linked to the group’s successful espionage operations against governments and defense organizations worldwide. Given the increasing complexity of Andariel’s operations, Mandiant has classified the group as an Advanced Persistent Threat (APT) and assigned it the code number APT45.
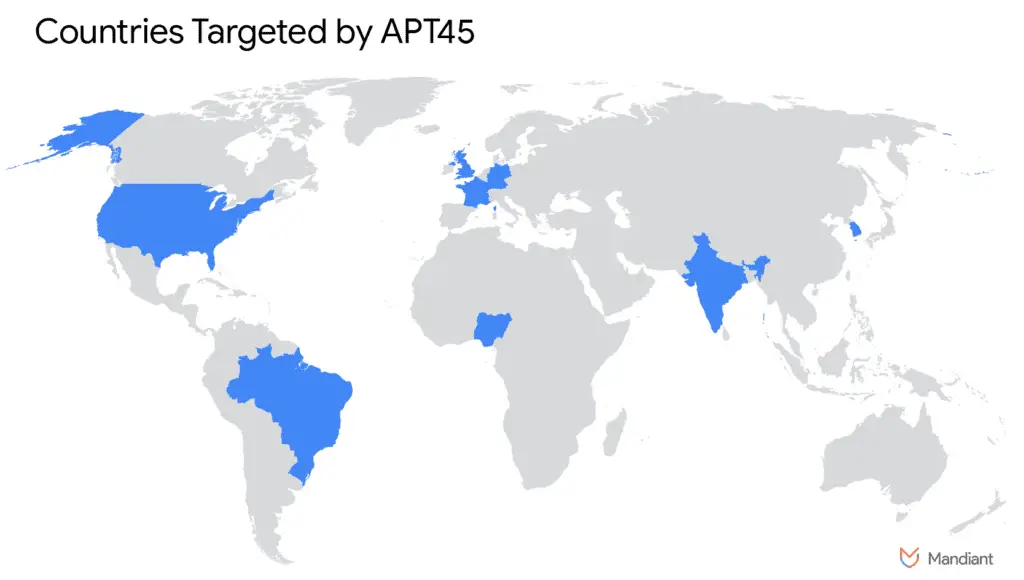
The group’s cyber espionage dates back to 2009, and since then, the hackers have gradually expanded their operations, including financially motivated attacks. In 2019, the group attacked India’s Kudankulam Nuclear Power Plant and other nuclear facilities and power plants. Other victims include agricultural complexes and medical and pharmaceutical companies.
Researchers note that APT45 is one of North Korea’s oldest groups. The hackers’ activities reflect the country’s geopolitical priorities, and despite shifting from classic cyber espionage against state structures to attacks on healthcare and agricultural systems, financially motivated attacks remain a crucial part of APT45’s strategy.
Andariel is a subgroup of the Lazarus Group, which has organized attacks on foreign companies, government agencies, private corporations, and South Korea’s defense industry to gather information and create disruption.
In July, AhnLab specialists identified cases of attacks on Korean ERP systems, during which Andariel took control of corporate networks and spread malware. The primary targets of the attacks were Korean defense and manufacturing enterprises.
In 2019, the U.S. Treasury Department imposed sanctions on three North Korean groups that carried out cyberattacks on government and private organizations worldwide. The sanctioned entities included Lazarus Group, Bluenoroff, and Andariel.
In March, a UN expert group presented a new report investigating 58 cyberattacks carried out by North Korean hacker groups over the past six years. Experts estimate the attacks brought the criminals about $3 billion in illegal revenue. The experts meticulously traced the activities of several groups—Kimsuky, Lazarus Group, Andariel, and BlueNoroff—hackers who regularly appear in cybersecurity researchers’ reports.
Related Posts:
- Expert: North Korean hackers harvest 11,000 Bitcoins in 2017
- Andariel: North Korea’s Cyber Threat Actor Steals Data, Launches Ransomware Attacks
- India announces to use artificial intelligence to develop weapon systems
- Russian nuclear weapons scientists arrested for using supercomputer to mine Bitcoins