
In a concerning escalation of social engineering and persistence techniques, cybersecurity firm ReliaQuest has uncovered a new backdoor malware campaign that began with Microsoft Teams phishing and escalated to include a novel COM Type Library (TypeLib) hijacking technique—a persistence method never previously observed in the wild.
The attack, discovered during incident response investigations across the finance and professional services sectors, mirrors early tactics attributed to the Storm-1811 (aka STAC5777) threat group—known for delivering Black Basta ransomware—but introduces entirely new behaviors and tooling that suggest either group evolution or splintering.
“We identified a previously unreported persistence method leveraging TypeLib COM hijacking plus a new PowerShell backdoor,” ReliaQuest stated.
The campaign began with phishing messages via Microsoft Teams, spoofing IT support personnel using a fraudulent tenant:
techsupport[at]sma5smg.sch[.]id
What set these phishing attempts apart was their precise targeting:
- Messages were timed between 2:00 p.m. and 3:00 p.m., exploiting the post-lunch lull.
- Only executives and high-privilege employees were targeted.
- Victims had female-sounding names, hinting at demographic profiling based on phishing susceptibility research.
“This wasn’t a wide net—it was a sniper shot aimed at people with power and access,” noted ReliaQuest analysts.
Once trust was gained, attackers used Windows Quick Assist to establish remote access—blending seamlessly into legitimate IT support workflows.
After gaining access, the adversaries executed a novel persistence method involving TypeLib hijacking of a COM object tied to Internet Explorer.
“When Explorer.exe references this hijacked object, the malware is downloaded and executed—persisting across system reboots,” the report explained.
The hijack leveraged the following registry modification:
This command instructed Windows to download and execute a remote script every time the COM object was accessed—even by core Windows processes like Explorer.exe.
Security researchers have discussed TypeLib hijacking before, but this marks the first confirmed case of it being exploited in the wild.
The hosted file (5.txt) contained heavily obfuscated JScript + PowerShell code wrapped in misleading, space-themed junk variables like “Galaxy,” “Orion,” and “Cosmos.”
Once decrypted, the PowerShell payload:
- Extracted the system’s hard drive serial number
- Created a unique beaconing URL (e.g., http://181.174.164.180/<serial>)
- Maintained an infinite C2 loop
- Used a mutex to avoid duplicate execution
- Bypassed PowerShell execution policies
- Reported success to a Telegram bot, confirming C2 link establishment
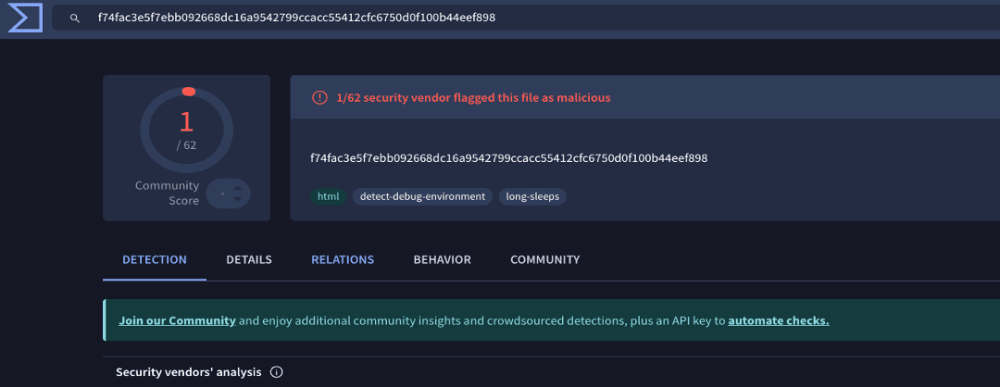
“At the time of writing, the file has minimal malicious scoring on VirusTotal, meaning it could slip right under the radar,” ReliaQuest observed.
ReliaQuest traced earlier versions of the malware back to January 2025, when it was distributed via malicious Bing ads targeting users searching for Microsoft Teams. These early variants lacked obfuscation and used localhost IPs for testing, hinting at staged development.
Interestingly, the Telegram bot logs used by the malware contained Russian-language syntax, reinforcing suspicions that the developers are Russian-speaking.
Despite infrastructure and code overlaps with the earlier Bing Ads campaign, ReliaQuest believes this new activity may not be directly tied to Black Basta or Storm-1811.
“It is realistically possible that a different group is responsible for the recent activity,” the report concludes.
Related Posts:
- Uncovering a New Persistence Technique: TypeLib Hijacking with Explorer.exe
- “The Com” Phishing Attacks Escalate, Targeting Businesses with Fake Login Pages
- Google Project Zero team found a Windows zero-day vulnerability
