POCKINT (a.k.a. Pocket Intelligence) is the OSINT swiss army knife for DFIR/OSINT professionals. Designed to be a lightweight and portable GUI program (to be carried within USBs or investigation VMs), it provides users with essential OSINT capabilities in a compact form factor: POCKINTs input box accepts typical indicators (URL, IP, MD5) and gives users the ability to perform basic OSINT data mining tasks in an iterable manner.
Features
Why use it? POCKINT is designed to be simple, portable and powerful.
Simple: There are a plethora of awesome OSINT tools out there. Trouble is they either require analysts to be reasonably comfortable with the command line (think pOSINT) or give you way too many features (think Maltego). POCKINT focuses on simplicity: INPUT > RUN TRANSFORM > OUTPUT … rinse and repeat. It’s the ideal tool to get results quickly and easily through a simple interface.
Portable: Most tools either require installation, a license or configuration. POCKINT is ready to go whenever and wherever. Put it in your jump kit USBs, investigation VMs or laptop and it will just run. Nobody needs graphs on an incident response 🙂
Powerful: POCKINT combines cheap OSINT sources (whois/DNS) with the power of specialized APIs. From the get-go, you can use a suite of in-built transforms. Add in a couple of API keys and you can unlock even more specialized data mining capabilities.
The beta version is capable of running the following data mining tasks:
Domains
- dns: ip lookup
- dns: mx lookup
- dns: txt lookup
- dns: ns lookup
- virustotal: downloaded samples
- virustotal: detected urls
- virustotal: subdomains
IP Adresses
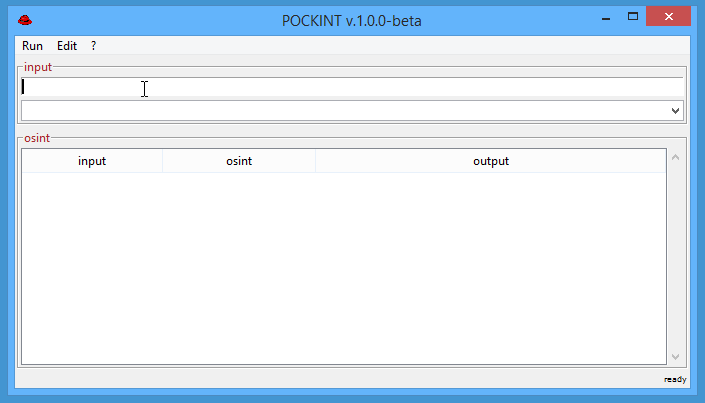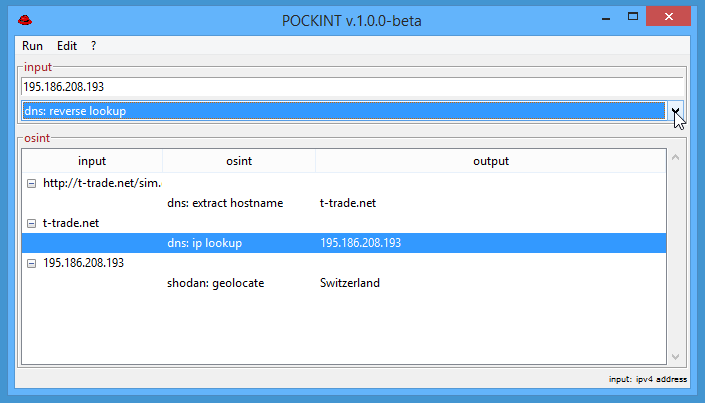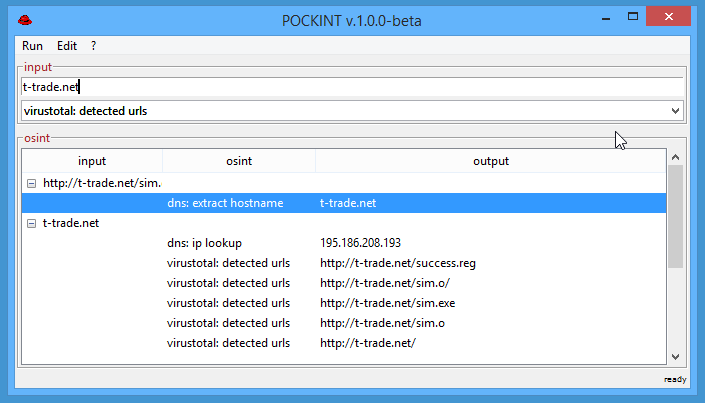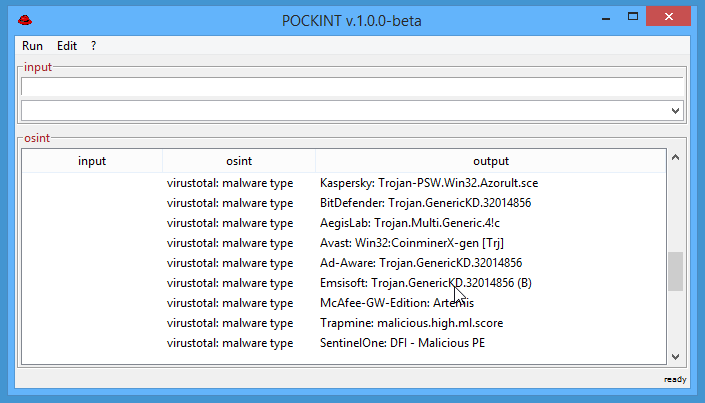
- dns: reverse lookup
- shodan: ports
- shodan: geolocate
- shodan: coordinates
- shodan: cves
- shodan: isp
- shodan: city
- shodan: asn
- virustotal: network report
- virustotal: communicating samples
- virustotal: downloaded samples
- virustotal: detected urls
Urls
- dns: extract hostname
- virustotal: malicious check
- virustotal: reported detections
Hashes
- virustotal: malicious check
- virustotal: malware type
Emails
- extract domain
Changelog v1.2
Added
- Subdomain discovery transform using crt.sh api
- Whois data mining integration
- Alienvault otx directconnect api integration
Fixed
- Transform error handling
Removed
- Linux support
Use
Copyright (c) 2019 NetEvert
Source: https://github.com/netevert/