A recent report from Qi’anxin Threat Intelligence Center exposes an advanced cyber-espionage campaign dubbed Operation Sea Elephant,...
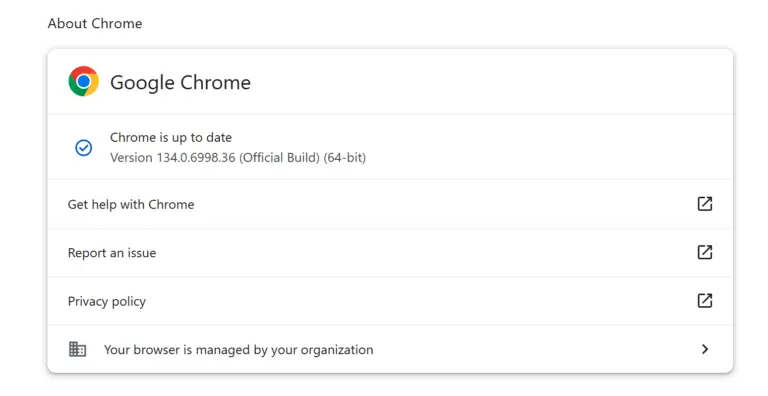
The Google Chrome team has officially pushed Chrome 134 to the stable channel for Windows (134.0.6998.35/36), Mac...
A severe security vulnerability has been discovered in GiveWP, the popular WordPress donation plugin, putting over 100,000...
A recent report from FortiGuard Labs has shed light on an advanced cyber campaign leveraging the open-source...
Broadcom, the parent company of VMware, has released a critical security advisory (VMSA-2025-0004) detailing multiple vulnerabilities affecting...
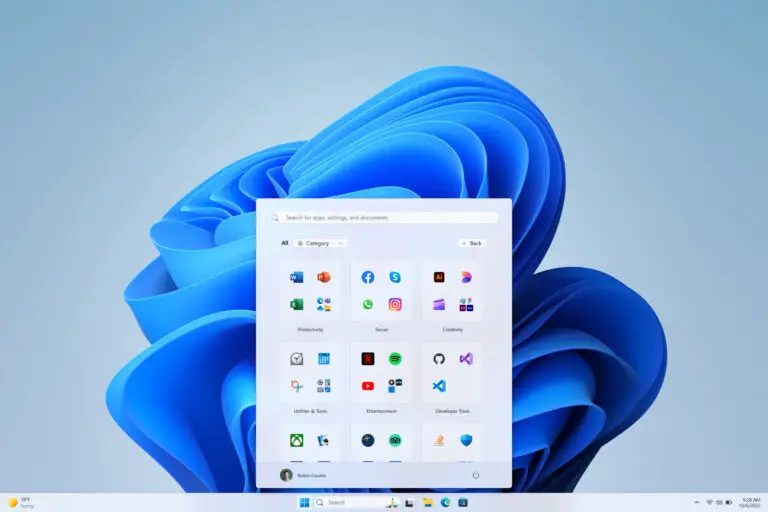
Microsoft recently updated the Windows 11 hardware compatibility page, removing hundreds of Intel processors, including models from...
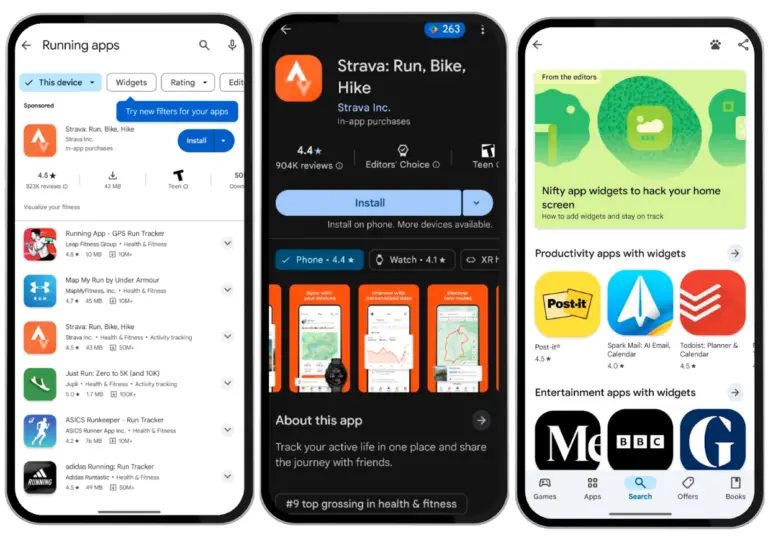
Google has announced a series of interface enhancements for the Google Play Store, aimed at making it...
Microsoft has recently announced the deprecation of the Data Encryption Standard (DES), a symmetric-key block cipher introduced...
Google has released the Android Security Bulletin for March 2025, detailing multiple security vulnerabilities affecting Android devices....
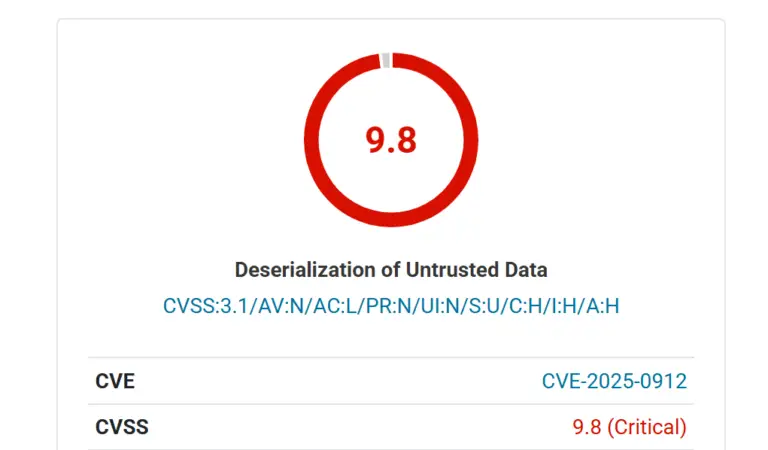
Security researchers from VulnCheck have disclosed a critical unauthenticated remote code execution (RCE) vulnerability in BigAntSoft BigAnt...
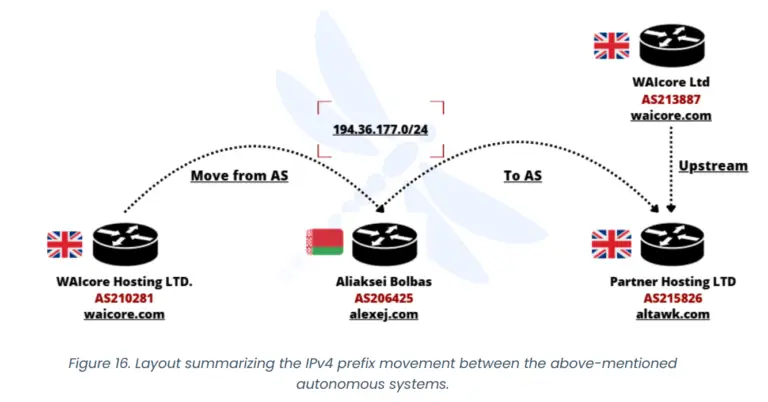
A recent report by cybersecurity firm Intrinsec has unveiled an ongoing large-scale disinformation campaign, known as Doppelgänger,...
IBM has issued a security bulletin disclosing two vulnerabilities affecting the graphical user interface (GUI) of several...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning for federal agencies to mitigate...
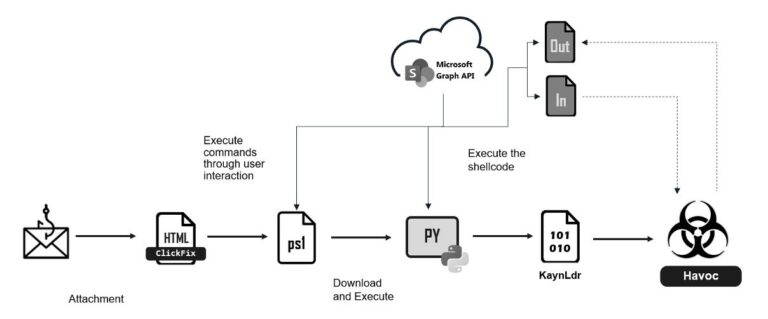
Security researchers from Unit 42 have uncovered an advanced phishing campaign orchestrated by the JavaGhost threat actor...
A newly uncovered malware distribution campaign is exploiting GitHub repositories to spread Redox Stealer, a malicious information-stealing...