Buck Shlegeris, the CEO of the non-profit organization Redwood Research, encountered an unforeseen challenge while using an...
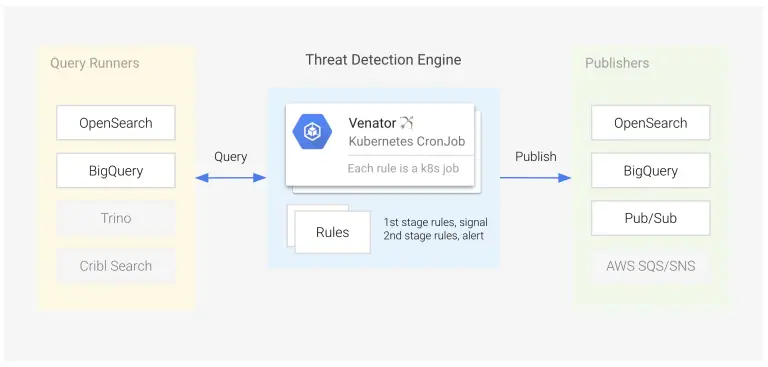
In today’s increasingly complex threat landscape, organizations require agile and scalable security solutions to effectively identify and...
Experts from the AhnLab Security Intelligence Center (ASEC) have uncovered new attacks on MS-SQL servers, targeting unsecured...
Red Barrels, the studio behind the acclaimed Outlast horror game series announced on Wednesday that it was...
The White House recently hosted the fourth gathering of the International Counter Ransomware Initiative (CRI), a coalition...
Google is stepping up its fight against cybercrime in India with a new pilot program for Google...
The Indian Computer Emergency Response Team (CERT-In) has issued an urgent advisory concerning two critical vulnerabilities discovered...
Identity and access management giant, Okta, recently addressed a vulnerability that could have allowed malicious actors with...
A severe security vulnerability has been identified in the Linear eMerge e3-Series access control systems, affecting versions...
ESET researchers have exposed a newly identified advanced persistent threat (APT) group, dubbed CeranaKeeper, targeting governmental institutions...
Cybersecurity analysts at Doctor Web have identified a new modification of the notorious Skidmap mining trojan targeting...
Kaspersky Labs has uncovered a sophisticated cyberattack campaign that abuses an open-source Security Information and Event Management...
The Australian Federal Police (AFP)-led Criminal Assets Confiscation Taskforce (CACT) has successfully restrained $9.3 million in cryptocurrency...
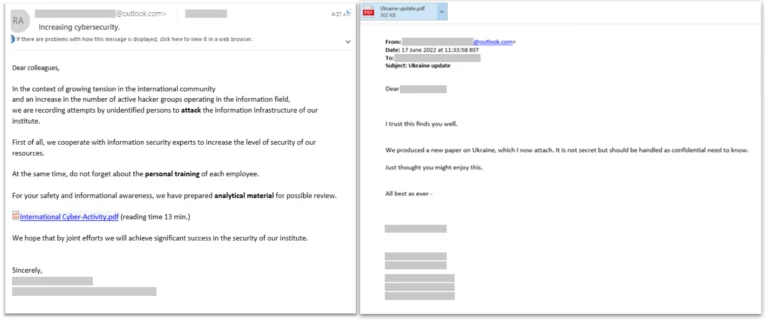
Yesterday, the Justice Department announced the seizure of 41 internet domains used by Russian intelligence agents to...
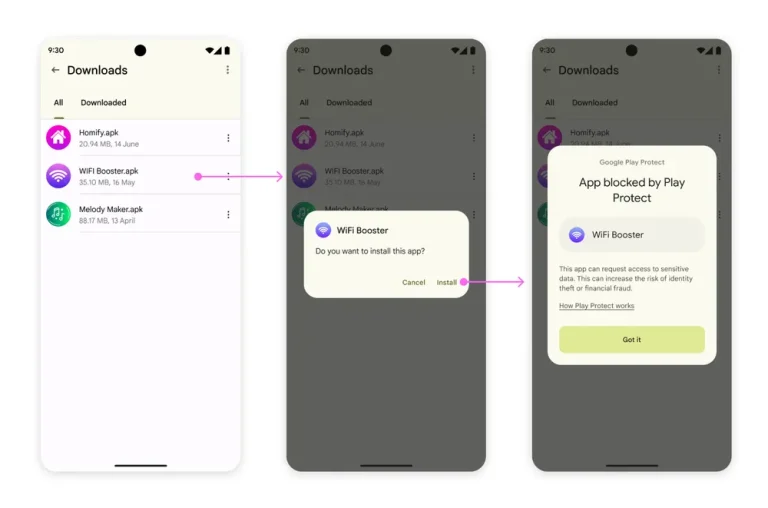
In a new blog post, Google has unveiled cutting-edge security features for its latest Pixel 9 lineup,...