polymorph v2.0.5 releases: multi-protocol real time manipulation framework
POLYMORPH
Polymorph is a framework written in the Python3 programming language that allows the modification of network packets in real-time, providing maximum control to the user over the contents of the packet. This framework is intended to provide an effective solution for real-time modification of network packets that implement practically any existing protocol, including private protocols that do not have a public specification. In addition to this, one of its main objectives is to provide the user with the maximum possible control over the contents of the packet and with the ability to perform complex processing on this information.
Changelog v2.0.5
Added some minor fixes:
- Removed the trail spaces from the command line
- The exception KeyboardInterrupt has been captured during the
captureprocess
Installation
Linux
apt-get install build-essential python-dev libnetfilter-queue-dev tshark tcpdump python3-pip wireshark
pip3 install –process-dependency-links polymorph
Windows
The requirements necessary for the framework to work correctly are the following:
- Installation of Python3 (add it to PATH). Download
- Installation of Wireshark (add it to the PATH). Download
- Installation of Visual C ++ Build Tools. Download
- WinPcap installation (If you have not installed it with Wireshark) Download
Once the dependencies are installed, the only thing that the user must do is open a console and execute the following command.
pip install –process-dependency-links polymorph
After completing the installation, Polymorph will be accessible from the terminal from any system path. It is important to note that in Windows, Polymorph must be executed in a console with administrative privileges.
Polymorph Interfaces
The framework is formed by a set of interfaces that change dynamically depending on the context in which the user is located.
In this way, the following subinterfaces can be distinguished:
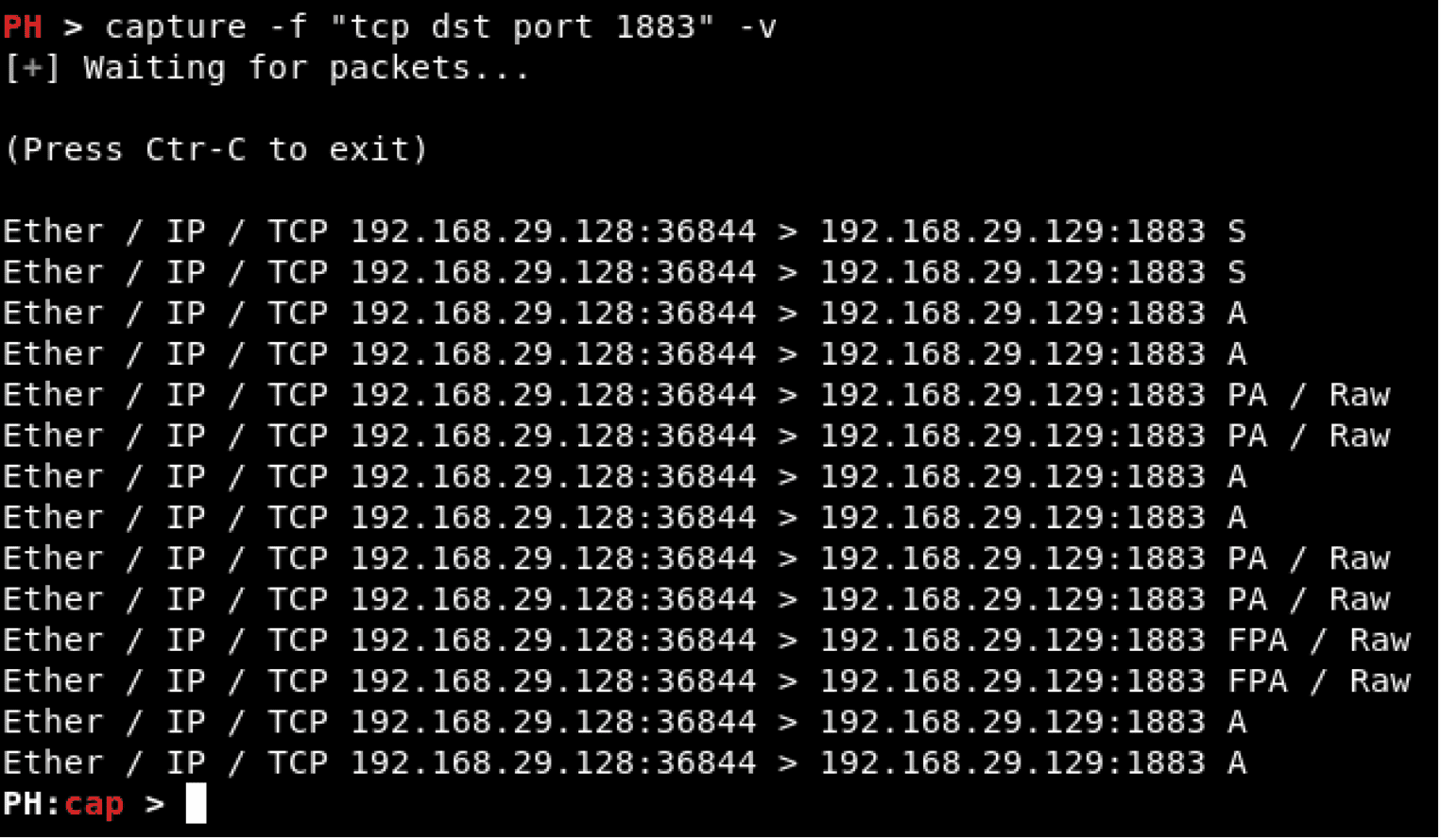
- Main interface: It corresponds to the first screen that is displayed when the application is executed, at this point, the user is not yet in a certain context. Allows the performance of actions such as spoofing or sniffing.
The prompt that is shown is the following:
PH>
• tlist interface: It corresponds to the interface that is shown after the completion of the sniffing process, as will be seen in the next section. The user is in the context of a list of templates that are generated from the captured packets. The prompt that is shown is the following:
PH: cap>
• template interface: It corresponds to the interface that is shown after the selection of a certain template (more details about it in the following sections). The user is in the context of a template and may take actions to modify their values. The prompt that is shown is the following:
PH: cap/ t5> - Layer interface: It corresponds to the interface that is displayed after the selection of a layer within a template (more details about it in the following sections). The user is in the context of a layer and can take actions to modify their values. The prompt that is shown is the following:
PH: cap/ t5 /TCP>
- Field interface: It corresponds to the interface that is displayed after the selection of a field within a layer (more details about it in the following sections). The user is in the context of a field and can perform actions to modify their values. The prompt that is shown is the following:
PH: cap/ t5 /TCP/ sp ort>
Usage

Copyright (C) 2018 shramos
Source: https://github.com/shramos/





