Red Team Scripts
Red Team Scripts is a collection of red teaming related tools, scripts, techniques, and notes developed or discovered over time during engagements. Related tool release blog posts can be found at Threat Express an Information Security and Red Teaming Blog.
Situational Awareness
Perform situational awareness on a local host or domain upon initial compromise.
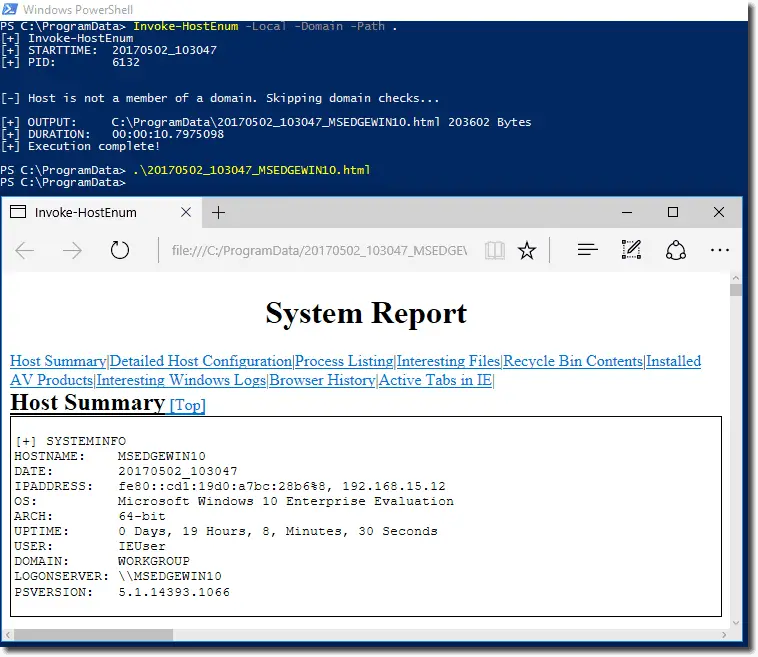
Invoke-HostEnum
Author: Andrew Chiles (@andrewchiles) with code by harmj0y, Joe Bialek, rvrsh3ll, Beau Bullock, Tim Medin
A PowerShell v2.0 compatible script comprised of multiple system enumeration / situational awareness techniques collected over time. If system is a member of a Windows domain, it can also perform limited domain enumeration with the -Domain switch. However, domain enumeration is significantly limited with the intention that PowerView or BoodHound could also be used.
Enumerated Information:
- OS Details, Hostname, Uptime, Installdate
- Installed Applications and Patches
- Network Adapter Configuration, Network Shares, Connections, Routing Table, DNS Cache
- Running Processes and Installed Services
- Interesting Registry Entries
- Local Users, Groups, Administrators
- Personal Security Product Status
- Interesting file locations and keyword searches via file indexing
- Interesting Windows Logs (User logins)
- Basic Domain enumeration (users, groups, trusts, domain controllers, account policy, SPNs)
Privilege Escalation
Optionally performs Privilege Escalation functions from PowerUp in the PowerSploit project.
Empire 2.0 Integration
Use the accompanying hostenum.py script to include Invoke-HostEnum as post-exploitation situational awareness module in Empire. Both files need to be copied to the appropriate locations in Empire.
Function Breakout
Most enumeration functions are now individually callable after loading the script. This means if you’re only interested in what AV processes are running, you can call the Get-AVInfo and Get-AVProcesses functions rather than running the entire script or modifying the code. The following is a subset of the functions and excludes ones specific to PowerUp (although they are also directly callable).
- Invoke-HostEnum
- Get-SysInfo
- Get-ProcessInfo
- Get-GroupMembership
- Get-ActiveTCPConnections
- Get-ActiveListeners
- Get-FirewallStatus
- Get-InterestingRegistryKeys
- Get-IndexedFiles
- Get-InterestingFiles
- Get-RecycleBin
- Get-AVInfo
- Get-McafeeLogs
- Get-AVProcesses
- Get-DomainAdmins
- Get-DomainAccountPolicy
- Get-BrowserInformation
- Get-ChromeHistory
- Get-ChromeBookmarks
- Get-InternetExplorerHistory
- Get-InternetExplorerBookmarks
- Get-FirefoxHistory
- Get-ActiveIEURLS
- Get-UserSPNS
Download
git clone https://github.com/threatexpress/red-team-scripts.git
Usage
Execute locally hosted script in “Quick” mode with console output.
powershell -ep bypass -c Import-Module ./HostEnum.ps1; Invoke-HostEnum -QuickExecute locally hosted script with HTML report output. If you want the most readable format and don’t mind writing a file to disk, consider using the “-HTMLReport” option to create a report in the current directory.
powershell -ep bypass -c Import-Module ./HostEnum.ps1; Invoke-HostEnum -Local -HTMLReportExecute all checks (equivalent to running -Local -Domain -Privesc) and save results as an HTML report.
powershell -ep bypass -c Import-Module ./HostEnum.ps1; Invoke-HostEnum -All -HTMLReportPerform a quick “sysinfo” like check via the Get-SystemInfo function.
powershell -ep bypass -c Import-Module ./HostEnum.ps1; Get-SysInfo
Copyright 2018 Andrew Chiles
Source: https://github.com/threatexpress/