Sync-Scheduler Malware: Unveiling a Sophisticated Espionage Attack
In a detailed report, the BlackBerry Research and Intelligence Team has revealed a highly targeted cyber espionage campaign against the Pakistan Navy, executed by a sophisticated and likely state-sponsored threat actor. The campaign leveraged typosquatted domains, malicious email extensions, and a stealthy information-stealing malware dubbed Sync-Scheduler.
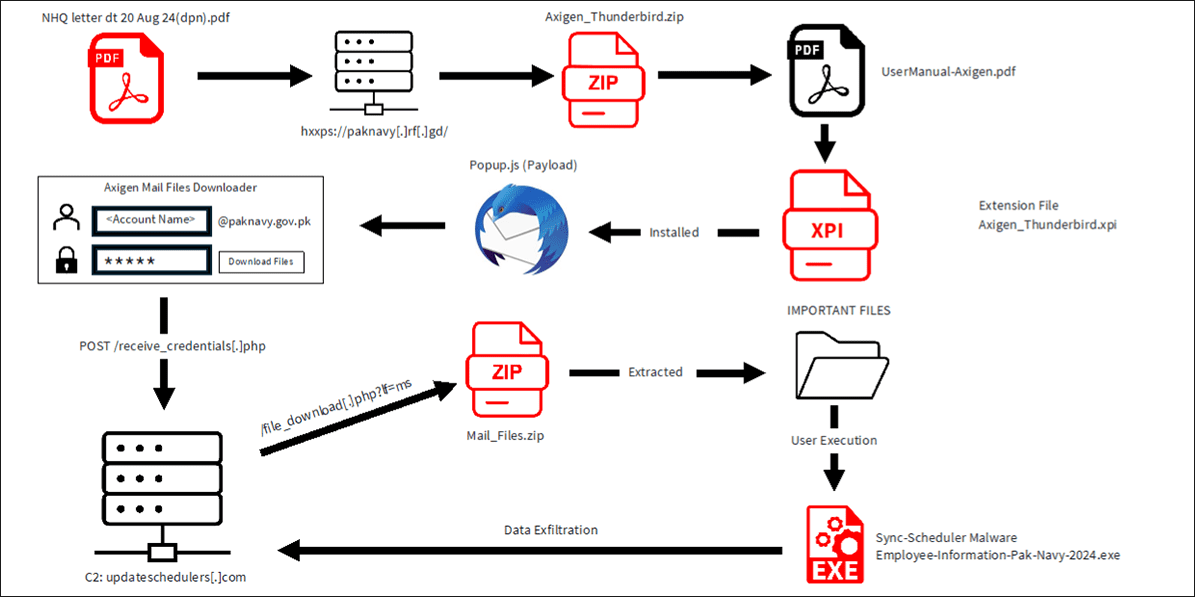
The operation began with a PDF lure, masquerading as an internal Pakistan Navy IT memo for configuring secure email communication with Axigen Thunderbird. Embedded within the document was a malicious URL designed to mimic legitimate Pakistan Navy domains, exploiting typosquatting to trick users. The fake URL—hxxps://paknavy[.]rf[.]gd—closely resembled the official domain but led to a server hosting a malicious Thunderbird extension.
The malicious extension, once installed, posed as a legitimate tool titled “Mail Files Downloader.” BlackBerry’s analysis revealed: “The extension then displays a login form designed specifically for “@paknavy.gov.pk” email addresses, misleading the victim into believing that upon entering their credentials they will be able to access and download their emails.”

Pakistan Navy initial lure document | Image: BlackBerry
At the heart of the operation was Sync-Scheduler, a sophisticated information-stealing malware designed to exfiltrate sensitive documents. Authored in C++ with advanced anti-analysis features, Sync-Scheduler targets specific file types, such as .docx, .pdf, and .xlsx, organizing them for exfiltration. The malware also employs robust evasion techniques, including:
- Dynamic Decryption: Data is decrypted only during runtime to avoid detection.
- Persistence Mechanisms: Scheduled tasks masquerading as legitimate processes like OneDrive and WindowsUpdate
BlackBerry researchers noted that Sync-Scheduler’s core functionality—exfiltration of documents—remained consistent with earlier versions identified in campaigns dating back to mid-2023.
While attribution remains inconclusive, BlackBerry identified overlaps in tactics with two prominent groups:
- SideWinder: Known for targeting Pakistani government entities with similar phishing and credential harvesting techniques.
- APT Bitter: A South Asian group suspected of espionage campaigns against Pakistan and other regional targets.
BlackBerry cautioned: “Despite these overlaps and indications for both groups, at the time of writing this we do not feel there is a strong enough body of evidence to warrant a positive attribution to either of these groups, and will therefore consider this campaign as being perpetuated by an unknown group or nexus.”
This targeted attack on the Pakistan Navy demonstrates the persistent risks posed by state-sponsored cyber espionage campaigns. By leveraging sophisticated tools like Sync-Scheduler and deceptive techniques like typosquatting, the adversaries showcased a high degree of skill and planning.