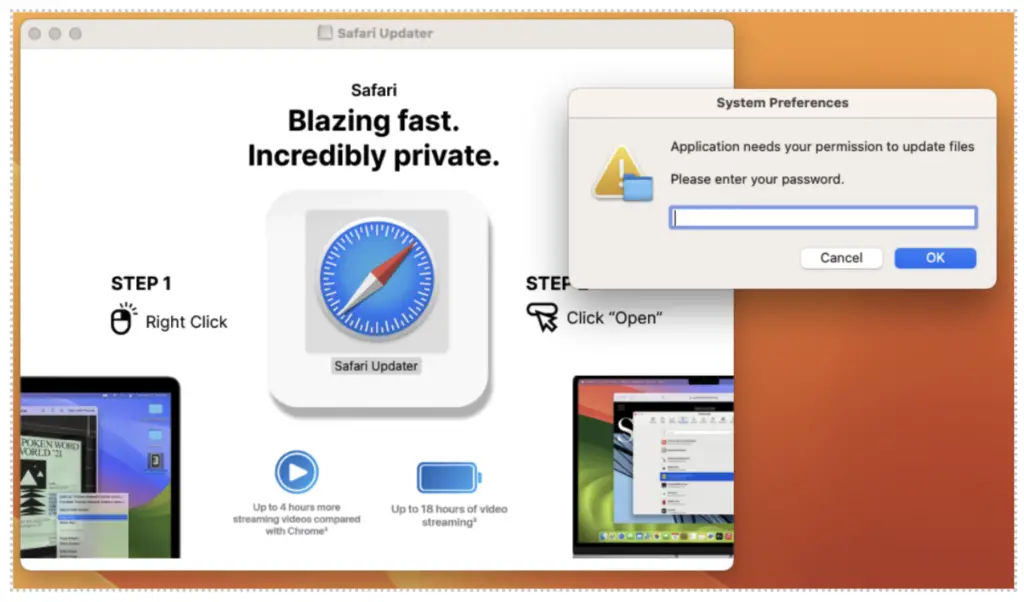
Malicious “Safari Updater” | Source: Proofpoint
Cybersecurity researchers at Proofpoint have identified two new cybercriminal threat actors, TA2726 and TA2727, actively exploiting fake browser update scams to distribute Windows, Android, and Mac malware. Notably, the report reveals the discovery of FrigidStealer, a new MacOS information-stealing malware.
For years, TA569 and its SocGholish web injects have dominated the landscape of fake update scams—a well-known social engineering trick that tricks users into downloading malware disguised as browser updates. However, in 2025, the web inject ecosystem has become increasingly crowded with copycat groups, making it harder for cybersecurity analysts to track who’s behind which attack.
“The web inject campaign landscape is increasing, with a variety of copycat threat actors conducting similar campaigns, which can make it difficult for analysts to track,” Proofpoint researchers reported.
In response to this evolving threat, Proofpoint has named two new threat actors:
- TA2726: A traffic distribution service (TDS) operator, likely selling malicious web traffic to other cybercriminals.
- TA2727: A malware distributor, responsible for deploying multiple infostealers across Windows, Android, and MacOS.
Among TA2727’s malware arsenal, FrigidStealer is a new MacOS information stealer delivered via fake update pages. This marks a significant shift, as MacOS malware has historically been less common than its Windows counterparts. However, cybercriminals are increasingly targeting Mac users, including those in enterprise environments.
How the Attack Works on Mac
- Fake Update Page: A Mac user visiting a compromised website is redirected to a fraudulent browser update page.
- DMG File Download: Clicking “Update” triggers the download of a malicious DMG file.
- Bypassing Gatekeeper: The user is tricked into right-clicking the file and selecting “Open”, bypassing MacOS security warnings.
- FrigidStealer Execution: The malware, written in Go and ad-hoc signed, is executed using Apple Script and osascript.
- Data Theft & Exfiltration: FrigidStealer collects browser cookies, password-related files, cryptocurrency wallets, and Apple Notes, sending them to a Command-and-Control (C2) server at askforupdate[.]org.
“FrigidStealer uses Apple script files and osascript to prompt the user to enter their password, and then to gather data including browser cookies, files with extensions relevant to password material or cryptocurrency from the victim’s Desktop and Documents folders, and any Apple Notes the user has created,” Proofpoint explained.
Mac users aren’t the only victims. TA2727 has been observed distributing multiple malware families, including:
- Lumma Stealer (Windows)
- DeerStealer (Windows)
- Marcher (Android banking trojan).
A key tactic used by TA2727 is geographic filtering—the payload delivered varies based on the visitor’s country and operating system. For example, Windows users in the U.S. and Canada were shown a SocGholish fake update, while Android users in Europe received a Marcher banking trojan.
TA2726 acts as a Traffic Distribution Service (TDS), redirecting users to TA569’s SocGholish campaigns in North America and TA2727’s malware campaigns in other regions. This commercialized infrastructure enables cybercriminals to:
- Compromise websites and inject malicious JavaScript.
- Distribute traffic based on geography and device type.
- Deliver custom malware payloads to each victim.
“TA2726 appears to be a traffic seller and operates a TDS that can serve other threat actors to facilitate their malware distribution,” Proofpoint researchers noted.
“MacOS information stealers are increasingly common. Actors are using web compromises to deliver malware targeting both enterprise and consumer users,” Proofpoint warns.
Related Posts:
- Hacker exploits Google App script to spread malware
- Zero-Day Vulnerability: 18 Years of Exploiting the ‘0.0.0.0’ Flaw
- Trojan Malware Infiltrates Browser Extensions, Impacts 300,000 Users
- Hackers Exploit YouTube for Game Cracks, Steal Your Data
- Temptation from Money: Lazarus APT extended to cryptocurrencies