THRecon
THRecon -Threat Hunting Reconnaissance Toolkit-
A collection of PowerShell modules designed for artifact gathering and reconnaissance of Windows-based endpoints. Use cases include incident response triage, threat hunting, baseline monitoring, snapshot comparisons, and more.
| Host Info | Processes* | Services | Autoruns | Drivers |
|---|---|---|---|---|
| ARP | DLLs* | EnvVars | Hosts File | ADS |
| DNS | Strings* | Users & Groups | Ports | Select Registry |
| Hotfixes | Handles* | Sofware | Hardware | Event Logs |
| Net Adapters | Net Routes | Sessions | Shares | Certificates |
| Scheduled Tasks | TPM | Bitlocker | Recycle Bin | User Files |
- Ingest using your SIEM of choice (Check out THRecon-Elasticstack and SIEM Tactics)
Install
Requirements
- Requires Powershell 5.0 or above on the “scanning” device.
- Requires Powershell 3.0 or higher on target systems. You can make this further backward compatible to PowerShell 2.0 by replacing instances of “Get-CIMinstance” with “Get-WMIObject”
- When scanning a remote machine without the psexec wrapper (Invoke-THR_PSExec), requires WinRM service on remote machine.
Install with PowerShell
Copy/paste this into a PowerShell console
Functions can also be used by opening the .psm1 file and copy-pasting its entire contents into a PowerSell console.
To update, simply run the same block of commands again.
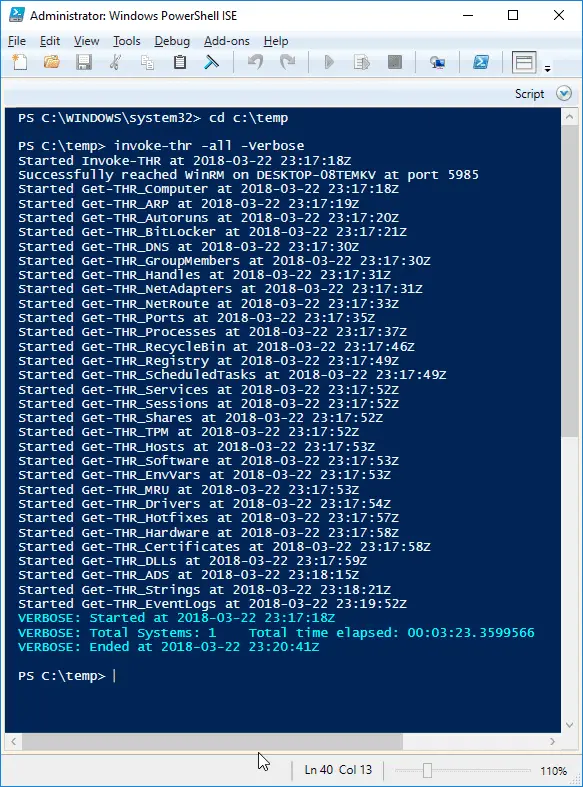
Usage
An output of Command “Invoke-THR”

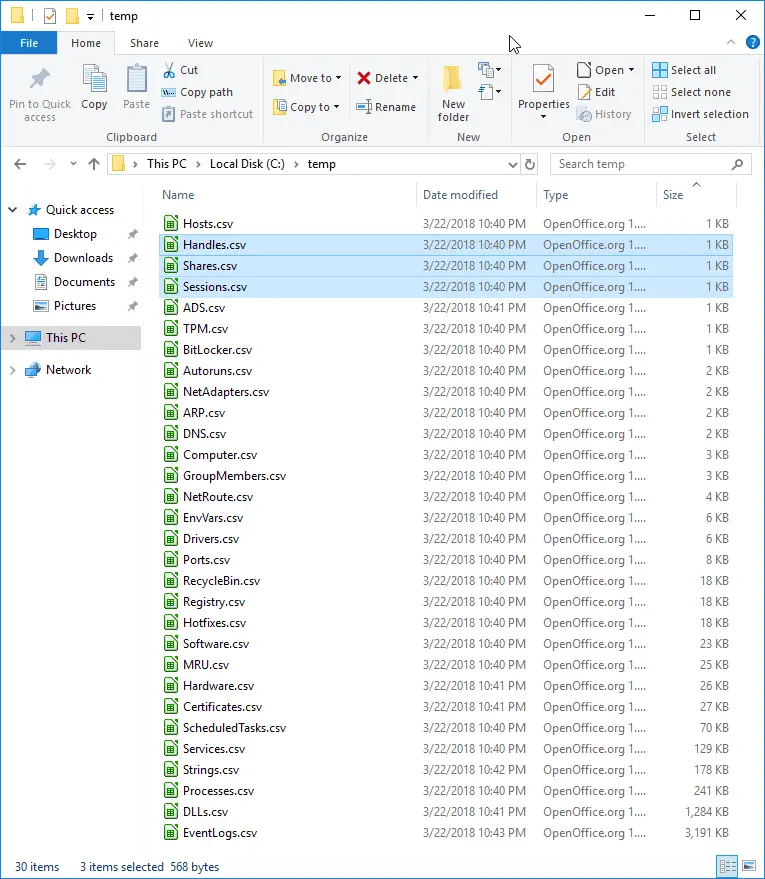
Output Files
Tutorial
Copyright (C) 2018 TonyPhipps
Source: https://github.com/TonyPhipps/