Infection chain
In a recent analysis, Cyble Research and Intelligence Labs (CRIL) has uncovered alarming developments involving two Advanced Persistent Threat (APT) groups, Transparent Tribe (APT36) and SideCopy. These threat actors are employing sophisticated and overlapping cyber strategies to target India, posing significant risks to both public and private sectors.
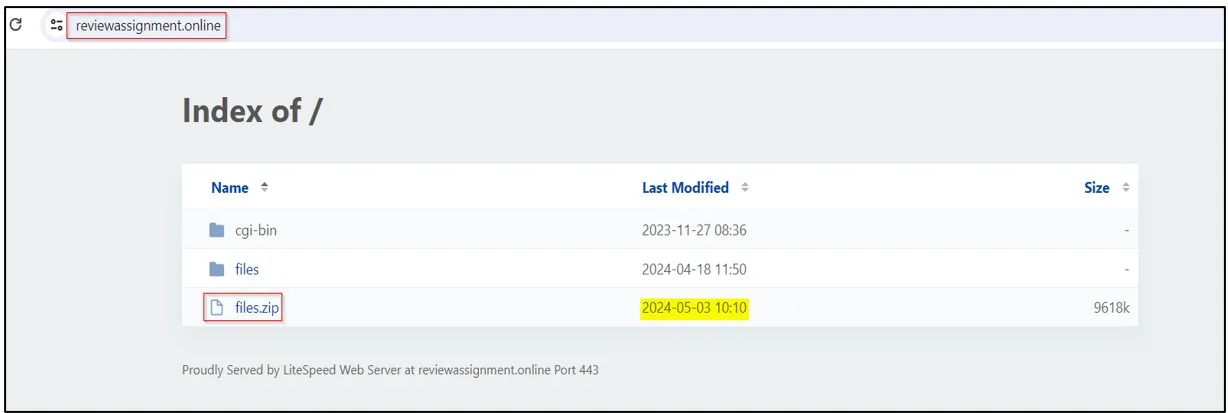
In the first week of May, CRIL identified a malicious website associated with the SideCopy APT group. This website hosted a file named “files.zip,” containing three directories: “economy,” “it,” and “survey.” The “survey” directory was found to contain lure files similar to those used in previous campaigns, while the other two directories remain undisclosed.
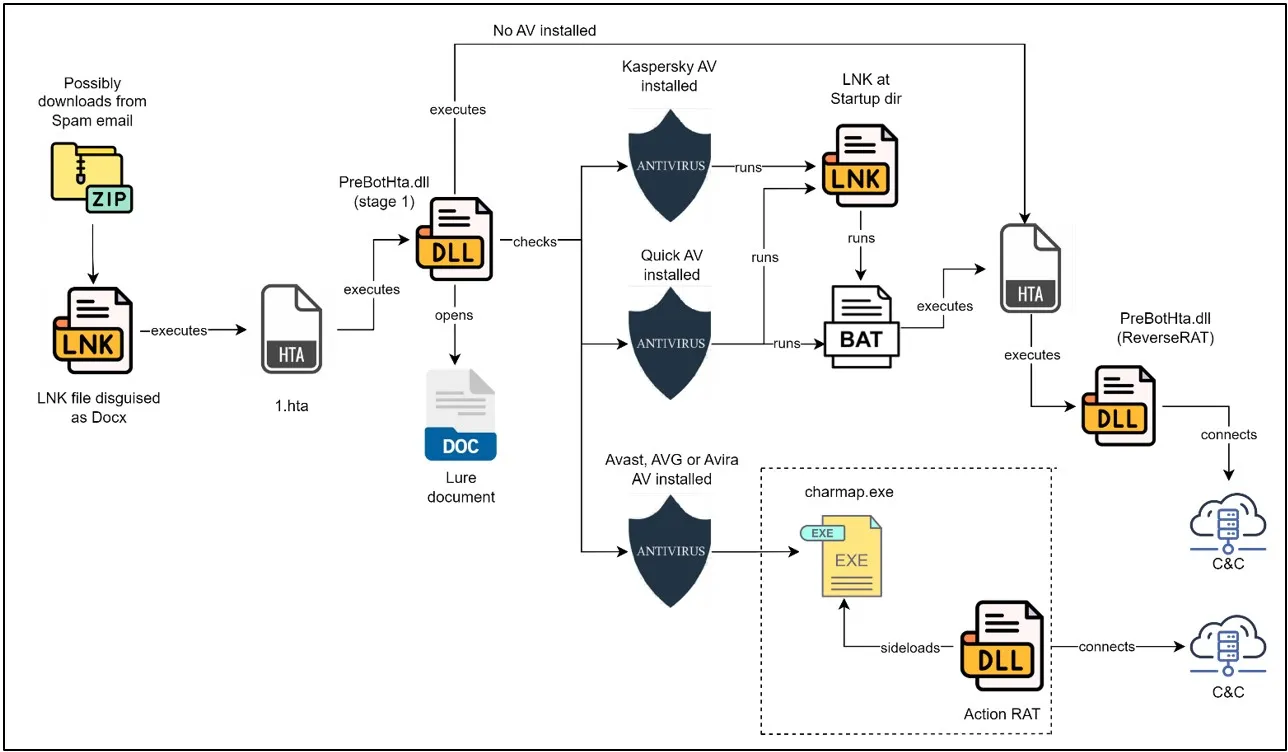
Upon further investigation, CRIL uncovered the use of malicious LNK files in the SideCopy malware campaign. These files, once executed, trigger a series of commands leading to the deployment of malware. The infection starts with a spam email, prompting the download of a ZIP file containing an LNK file disguised as a document. When executed, this file initiates the launch of “mshta.exe” to connect to a malicious URL and download an HTA file, which further executes a malicious DLL.
The HTA file concatenates embedded Base64-encoded strings, decodes them, and writes the resulting content into memory as a malicious DLL named “PreBotHTta.dll.” This DLL uses ActiveX objects for dynamic method invocation to execute its payload, which includes decoding and decompressing additional malicious content.

The malware then downloads a text file from a specified URL, saves it as “newFile.txt,” and utilizes it for further malicious activities. Depending on the installed antivirus software, different execution paths are followed. For instance, if Kaspersky AV is detected, the malware drops additional HTA and batch files to maintain persistence. Similar methods are employed for systems with other antivirus software, ensuring the malware remains active and undetected.
In some cases, the malware deploys ReverseRAT, a Remote Access Trojan, by continuously performing malicious activities such as data exfiltration and system monitoring. This RAT adapts its behavior based on the installed antivirus software, showcasing the attackers’ adaptability and sophistication.
The SideCopy APT group, operating as a subgroup of Transparent Tribe, presents a significant threat due to their advanced and coordinated attack vectors. Their ability to deploy versatile malware like ReverseRAT and Action RAT underscores the need for robust and flexible cybersecurity defenses.