
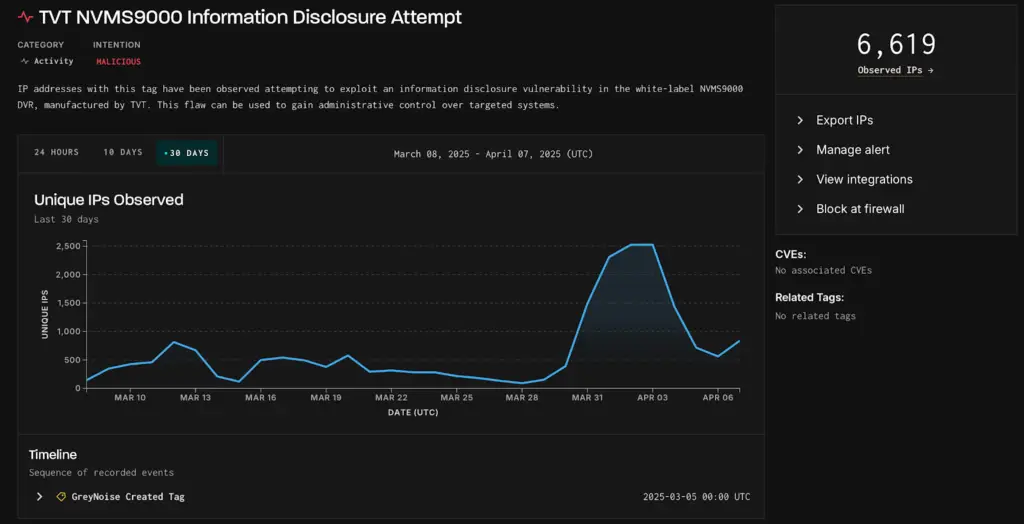
A significant surge in malicious cyber activity has been detected, raising alarms for organizations utilizing TVT NVMS9000 DVRs. GreyNoise intelligence reports “a significant spike 3 times that of typical activity in exploitation attempts against TVT NVMS9000 DVRs,” with the peak occurring on April 3rd, registering over 2,500 unique attacking IP addresses.
The core issue lies within an information disclosure vulnerability in the TVT NVMS9000 DVR. According to GreyNoise, “This information disclosure vulnerability can be used to gain administrative control over affected systems“. This level of access could enable malicious actors to manipulate video footage, disable surveillance, or use the compromised DVRs as part of a larger attack infrastructure. The report explicitly warns that attackers “could potentially use this flaw to gain full control of the DVR“.
GreyNoise’s analysis points towards a familiar culprit. The report has “identified sufficient overlap with Mirai, indicating this activity is associated with the botnet“. This finding is particularly concerning given the history of the Mirai botnet, known for launching large-scale DDoS attacks. The GreyNoise report notes that “Countless reports in the past have named the TVT NVMS9000 DVR as a target for botnet enlistment, including a GreyNoise update reporting Mirai targeting in early March“.
The affected DVRs, manufactured by TVT Digital Technology Co., Ltd., are used in security and surveillance systems for recording, storing, and managing video footage. TVT has a substantial global presence, with a report mentioning the company “has served customers in more than 120 countries“. This widespread deployment amplifies the potential impact of the vulnerability.
GreyNoise data reveals that the surge in exploitation attempts began on March 31, 2025, with the number of attacking IPs peaking at over 2,500 by April 3rd. In the 30-day window leading up to the report, over 6,600 IPs were involved in these malicious activities. Importantly, “GreyNoise can confirm that all IPs targeting the flaw in the past 30 days are malicious, and none of them are spoofable“.
The geographical distribution of these attacks is noteworthy. “The majority of IPs in the past 30 days have originated from the Asia-Pacific (APAC) region,” while the primary targets are in other parts of the world. Specifically, the top source countries include Taiwan (3,637 IPs), Japan (809 IPs), and South Korea (542 IPs). Conversely, the top destination countries are the United States (6,471 IPs), the United Kingdom (5,738 IPs), and Germany (5,713 IPs). This disparity highlights the global nature of cyber threats, where attackers from one region target vulnerable systems in others.
In light of these findings, GreyNoise strongly advises organizations using TVT NVMS9000 DVRs or similar systems to take immediate action to secure their devices. The recommended steps include:
- Blocking Malicious IPs: Use GreyNoise to block known malicious IP addresses attempting to exploit this vulnerability.
- Patching: Apply all available patches to the DVR systems.
- Restricting Public Access: Restrict public internet access to DVR interfaces to minimize exposure.
- Network Monitoring: Monitor network traffic for signs of unusual scanning or exploitation attempts.
- Proactive Threat Intelligence: Monitor attacker activity targeting this flaw and block malicious IPs.
Related Posts:
- CVE-2024-7339: DVR Vulnerability Exposes Over 400,000 Devices to Hackers
- HiatusRAT Campaign Targets Web Cameras and DVRs: FBI Warns of Rising IoT Exploits
- Argentinian security researcher found how to access a bunch of DVRs
- CVE-2024-8956 & CVE-2024-8957: Two Actively Exploited Vulnerabilities in PTZ Cameras