Using Nessus and Metasploit Together
Introduction to Nessus
Nessus is a vulnerability scanning and analysis software from tenable, a leading information security services company, known as “the world’s most popular vulnerability scanner, used by more than 75,000 organizations worldwide.” Although the scanner is available for free download, the cost of direct ordering is $ 1,200 per year, or $ 100 per month, to update from Tenable to all the latest threat information. Nessus is available on Linux, FreeBSD, Solaris, Mac OS X, and Windows.
Nessus is currently divided into four versions: Nessus Home, Nessus Professional, Nessus Manager, Nessus Cloud.
- Nessus Home freeware for home users limited for scanning 16 hosts and for non-commercial home use only. It doesn’t support compliance checks (it is written on a site, but as fact it does) or content audits.
- Nessus Professional can scan any amount of hosts without limitations. Ideal for the companies with low budgets or/and companies with enormous amount of host in network. Costs only $2,190.00. Extremely cheap comparing with other commercial vulnerability scanner.
- Nessus Manager for small enterprises. It is positioned by Tenable as “Vulnerability management” solution. As I see it, some Tenable users could said “We use Nessus, we like it, but we want some more features: dashboards, integration with Active Directory and somehow to control nessus slave-scanner with nessus-master scanner. So, now we have more expansive Nessus Manager for such users. And we need to use it for multiscanner feature and the local agents. And it is licensed by Ip. In may 2016 Nessus Manager cost $2,920.00 for 128 Hosts/128 Agents and $4,745.00 for 256 Hosts/256 Agents. Upd. I wrote a separate post about Nessus Manager and agent scanning, so if you are interested plz check out: “Nessus Manager and Agents“
- Nessus Cloud – like Nessus Manager but hosted on Tenable servers (Service As A Service, SaaS). Cost is the same as Nessus Manager. In April 2016 Tenable added some more advanced dashboards and scanning management features in Nessus Cloud. Maybe they will add such features in Nessus Manager. Maybe not.
Installation
Registration & installation Tenable Nessus on Linux
Update plugin
Nessus update include online update method and offline update method:
Online update method:
- Login> setting> Scanners> Local / Overview
- Click Version, Last Updated automatically in the Overview interface
- Setting> Scanners> Local> Software Update
Automatic Updates has three options – Update all components – Update plugins – Disabled – - Update Frequency, you can select the daily, weekly, monthly check update.
Offline update method:
- Close the nessus program, command:
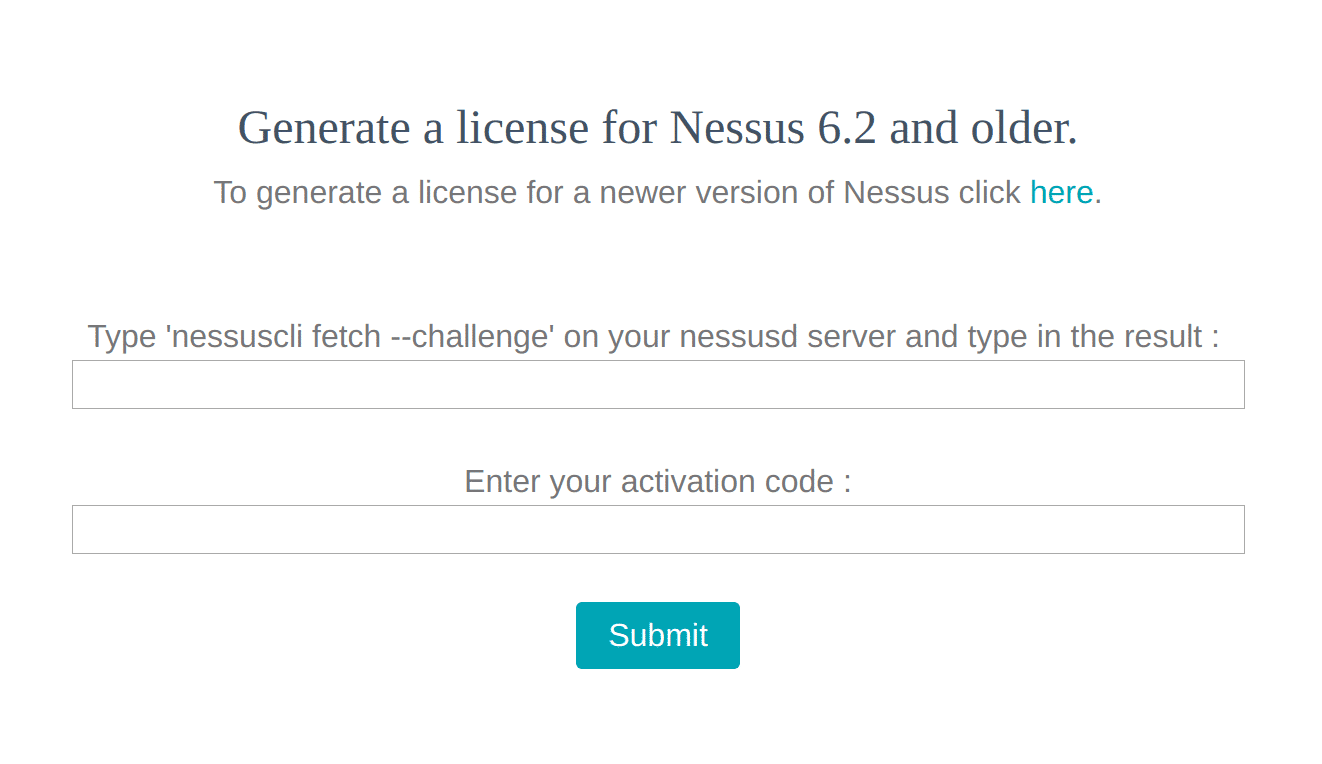
>/etc/init.d/nessusd stop - Obtain the Challenge code, command
>/opt/nessus/sbin/nessuscli fetch –challenge - Get the Active code and log back in to the URL
http://www.tenable.com/products/nessus-home - After logging in to https://plugins.nessus.org/offline.php , enter Challenge code and Active code.
- Download all-2.0.tar.gz with the nessus.license file
- After downloading the terminal command:
>/opt/nessus/sbin/nessuscli update /root/Downloads/all-2.0.tar.gz >/opt/nessus/sbin/nessuscli fecth –register-offline nessus.license - Restart the service
>/etc/init.d/nessusd restart
Using Nessus and Metasploit Together
- Start Nessus service
>/etc/init.d/nesssusd start - Start postgresql service and msfconsole
>service postgresql start
>msfconsole
>db_status
[*] postgresql connected to msf
- Load Nessus plugin on Metasploit
>load nessus
[*] Nessus Bridge for Metasploit
[*] Type nessus_help for a command listing
[*] Successfully loaded plugin: Nessus - To view Nessus option, use help command
>nessus_help
Command Help Text
——- ———
Generic Commands
—————– —————–
nessus_connect Connect to a Nessus server
nessus_logout Logout from the Nessus server
nessus_login Login into the connected Nesssus server with a different username and password
nessus_save Save credentials of the logged in user to nessus.yml
nessus_help Listing of available nessus commands
nessus_server_properties Nessus server properties such as feed type, version, plugin set and server UUID.
nessus_server_status Check the status of your Nessus Server
nessus_admin Checks if user is an admin
nessus_template_list List scan or policy templates
nessus_folder_list List all configured folders on the Nessus server
nessus_scanner_list List all the scanners configured on the Nessus server
Nessus Database Commands
—————– —————–
nessus_db_scan Create a scan of all IP addresses in db_hosts
nessus_db_scan_workspace Create a scan of all IP addresses in db_hosts for a given workspace
nessus_db_import Import Nessus scan to the Metasploit connected databaseReports Commands
—————– —————–
nessus_report_hosts Get list of hosts from a report
nessus_report_vulns Get list of vulns from a report
nessus_report_host_details Get detailed information from a report item on a hostScan Commands
—————– —————–
nessus_scan_list List of all current Nessus scans
nessus_scan_new Create a new Nessus Scan
nessus_scan_launch Launch a newly created scan. New scans need to be manually launched through this command
nessus_scan_pause Pause a running Nessus scan
nessus_scan_pause_all Pause all running Nessus scans
nessus_scan_stop Stop a running or paused Nessus scan
nessus_scan_stop_all Stop all running or paused Nessus scans
nessus_scan_resume Resume a pasued Nessus scan
nessus_scan_resume_all Resume all paused Nessus scans
nessus_scan_details Return detailed information of a given scan
nessus_scan_export Export a scan result in either Nessus, HTML, PDF, CSV, or DB format
nessus_scan_export_status Check the status of an exported scanPlugin Commands
—————– —————–
nessus_plugin_list List all plugins in a particular plugin family.
nessus_family_list List all the plugin families along with their corresponding family IDs and plugin count.
nessus_plugin_details List details of a particular pluginUser Commands
—————– —————–
nessus_user_list Show Nessus Users
nessus_user_add Add a new Nessus User
nessus_user_del Delete a Nessus User
nessus_user_passwd Change Nessus Users PasswordPolicy Commands
—————– —————–
nessus_policy_list List all polciies
nessus_policy_del Delete a policy - Connect msf to nessus
>nessus_connect username:password@localhost:8834
[*] Connecting to https://localhost:8834/ as ddos
[*] User ddos authenticated successfully. - View nessus policy
>nessus_policy_list Policy ID、Name、Policy UUID -
Create a scan task
> nessus_scan_new
[*] Usage:
[*] nessus_scan_new <UUID of Policy> <Scan name> <Description> <Targets>
[*] Use nessus_policy_list to list all available policies with their corresponding UUIDs -
Perform a scan task
> nessus_scan_launch
[*] Usage:
[*] nessus_scan_launch <scan ID>
[*] Use nessus_scan_list to list all the availabla scans with their corresponding scan IDs - View scan report
> nessus_report_vulns
[*] Usage:
[*] nessus_report_vulns <scan ID>
[*] Use nessus_scan_list to get a list of all the scans. Only completed scans can be reported. -
Import the postgresql database:
> > nessus_db_import
[*] Usage:
[*] nessus_db_import <scan ID>
[*] Example:> nessus_db_import 500
[*] Use nessus_scan_list -c to list all completed scans
[-] Only completed scans could be used for import





