
A new report from Cisco Talos Intelligence Group reveals the continued global spread and evolution of the XorDDoS malware, a notorious Distributed Denial-of-Service (DDoS) trojan that targets Linux machines. The research highlights the emergence of a new “VIP version” of the XorDDoS controller and its central controller, signaling a significant advancement in the capabilities of this malicious tool.
The XorDDoS trojan has been a persistent threat since its initial discovery in 2014. It operates by compromising Linux machines, turning them into “zombie bots” that can be used to launch DDoS attacks. Cisco Talos’s ongoing monitoring has shown a significant increase in XorDDoS prevalence between 2020 and 2023, a trend attributed to both its widespread distribution and an increase in malicious DNS requests linked to its command-and-control (C2) infrastructure. The trojan’s targets have also expanded from commonly exposed Linux machines to include Docker servers.
Talos’s investigation uncovered a new “VIP version” of the XorDDoS sub-controller and its corresponding central controller, which are being used to orchestrate more sophisticated and widespread attacks. According to the report, “Talos discovered the latest version of the XorDDoS controller, called the ‘VIP version,’ and its corresponding central controller were used to build the DDoS bot network for more sophisticated and widespread attacks.” This new central controller enables attackers to manage multiple XorDDoS controllers simultaneously, significantly enhancing their ability to coordinate and execute large-scale DDoS campaigns.
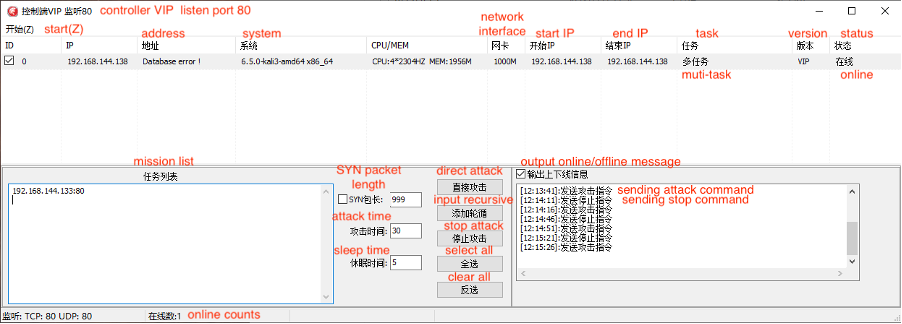
The report emphasizes the commercial nature of these new tools, stating, “With the newest version of the XorDDoS sub-controller and trojan builder, Talos believes that this collection is a product suite developed for sale.” This is further supported by feature descriptions within the builder, such as “Stable Anti-Kick, 100% Packet Sending, Fixes for Over Ten Thousand Online Without Lag. Supports Domain Online, IP Online, with New Packet Sending Code and Wall-Penetration Optimization. Can Send 1024 Packets with Resource Utilization Optimization.”
Cisco Talos’s research provides insights into the geographic focus of XorDDoS attacks. Between November 2023 and February 2025, nearly 50 percent of successfully compromised victims were located in the United States. However, the impact is global, with compromised systems being used to launch attacks against a wide range of countries. Notably, the United States was the target of over 70 percent of attempted attacks employing XorDDoS. As the report states, “Talos also used our Cisco Secure Network/Cloud Analysis to observe actors using those compromised machines to launch DDoS attack and the attacks are globalized,” and “Notably, we found that the United States accounted for over 70 percent of attempted attacks employing XorDDoS.”
The evolution of XorDDoS from a crude DDoS bot into a modular, multilingual attack suite with centralized control underscores the increasing industrialization of cybercrime.
