
In a rare window into the operations of an advanced persistent threat, a KeyPlug-linked infrastructure briefly went live, exposing tools and scripts tied to APT41/RedGolf operations. The server, active for less than 24 hours, revealed a trove of Fortinet exploit scripts, encrypted webshells, and reconnaissance tools specifically aimed at a major Japanese enterprise, believed to be Shiseido.
According to threat hunters at Hunt.io, the short-lived exposure provided an “unfettered view into a likely advanced adversary’s operational staging and planning.” The exposed server presented exploitation tooling, post-access payloads, and output logs—offering defenders valuable insights into how these attackers prepare, execute, and manage long-term operations.
The exposed server—IP 45.77.34[.]88—was flagged in a post by @Jane_0sint, pointing to its connection with KeyPlug, a malware family attributed to RedGolf, which overlaps with APT41. Researchers noted it shared TLS certificates with known KeyPlug infrastructure.
“This IP had already been under long-term monitoring as part of our broader research into KeyPlug infrastructure,” the report notes.
A Python SimpleHTTP/0.6 server was identified on port 80, indicating a file staging environment. Though direct access to the directory was eventually blocked, Hunt.io’s AttackCapture module had already indexed the server’s contents.
Unpacking the Toolset: What Was Exposed
Reconnaissance Output Targeting Shiseido
Inside the /awvs directory, a file named alive_urls_20250305_090959.txt listed nearly 100 Shiseido-related domains—including login portals, staging environments, and Okta/Keycloak-based identity providers across Singapore and Europe. This points to focused reconnaissance on authentication surfaces.
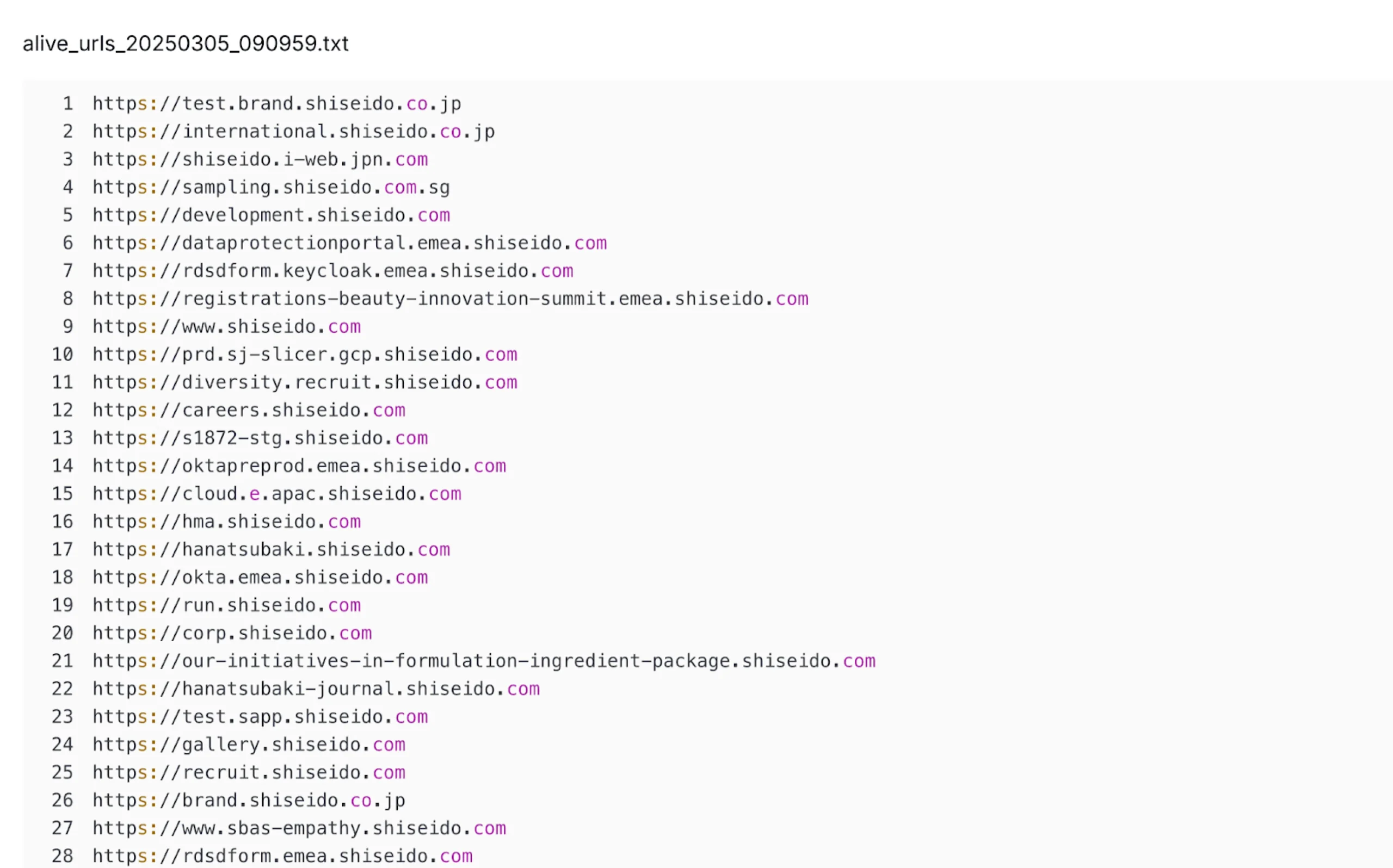
A second file, non_cdn_ips_20250305_090959.txt, correlated those domains to non-CDN protected IPs, supporting direct targeting.
script.py: CDN Fingerprinting Tool
This Python script scanned domains for CDN-related headers (like CF-RAY or Akamai-Cache-Status) and flagged those directly exposed to the internet. Its goal: isolate high-value assets without edge protections for follow-on exploitation. The absence of CDN-related headers doesn’t guarantee direct access, but the logic reflects a tactic to identify infrastructure with fewer mitigation layers.
1.py: Fortinet Fingerprinting and Recon
The 1.py script scanned for Fortinet VPN/firewall endpoints, collecting version-specific JavaScript hash values to determine software builds. This information aids in identifying vulnerable FortiOS versions. It automates requests to Fortinet login paths and parses responses to locate a login.js script URL containing a version-specific hash.
ws_test.py: WebSocket CLI Exploitation
Scripts like ws_test.py exploited CVE-2024-23108 and CVE-2024-23109, which allow unauthenticated WebSocket-based access to Fortinet CLI interfaces.
By spoofing local traffic with headers like:
The script bypasses authentication and executes privileged CLI commands such as: show full-configuration.
bx.php: Stealthy AES Webshell
This PHP webshell accepts encrypted payloads over POST requests, decrypts them using AES-128, and executes in memory. It suppresses errors and avoids using standard POST parameters—making it stealthy and hard to detect. By using AES-128 to obfuscate payloads and evaluating them only in memory, bx.php avoids leaving readable command content on disk or in logs.
client.ps1: PowerShell Reverse Shell
This PowerShell implant connects back to the server via TCP port 8080, using AES-128 in ECB mode to encrypt all communications. It operates silently, with heartbeat checks and 30-minute retry intervals for persistence.
Server: Minimal HTTP-Based Listener
The ELF binary Server functioned as an operator console, listening on port 8080. It allowed the attacker to manage sessions, issue commands, and interact with implants using plaintext commands—offering a central command-and-control interface.
“Operators rarely leave behind the logic of their work. Yet for a brief moment… it captured the cadence of an operation: scanning, filtering, staging, and tasking.”
This brief exposure granted a unique look into a sophisticated operational pipeline: from asset discovery and filtering to exploitation and remote access. For defenders, these snapshots are invaluable.
Related Posts:
- Cyber Espionage Alert: APT41 Strikes Global Industries, Steals Sensitive Data
- Chinese APT41 Group Breaches Taiwanese Research Institute
- ThreatMon Revealed APT41’s Stealthy PowerShell Backdoor
- Fortinet Faces Potential Data Breach, Customer Data at Risk
