
In today’s digital age, online file converters have become indispensable tools for streamlining daily workflows. However, a recent report by CloudSEK’s Security Research team has uncovered a sophisticated threat lurking behind the convenience of these services: malicious PDF-to-DOCX converters.
The core of the attack involves threat actors creating malicious websites that perfectly mimic legitimate services. In one instance, the attackers meticulously replicated the user interface of pdfcandy.com, even using similar-looking domain names to deceive unsuspecting users.
The attack unfolds through a series of carefully orchestrated social engineering tactics. Users are prompted to upload a PDF file for conversion, a common need that initiates the attack vector. The malicious site then employs a simulated loading sequence to create the illusion of genuine file processing, building trust and lowering the user’s guard. Following this, users are presented with a fake captcha verification dialog. CloudSEK’s report emphasizes the multi-purpose nature of this unexpected interruption:
- It mimics legitimate security practices, enhancing the site’s perceived authenticity.
- It creates a sense of urgency, potentially rushing the user into action.
- The CAPTCHA acts as a pivotal interaction point to trigger the malicious payload.
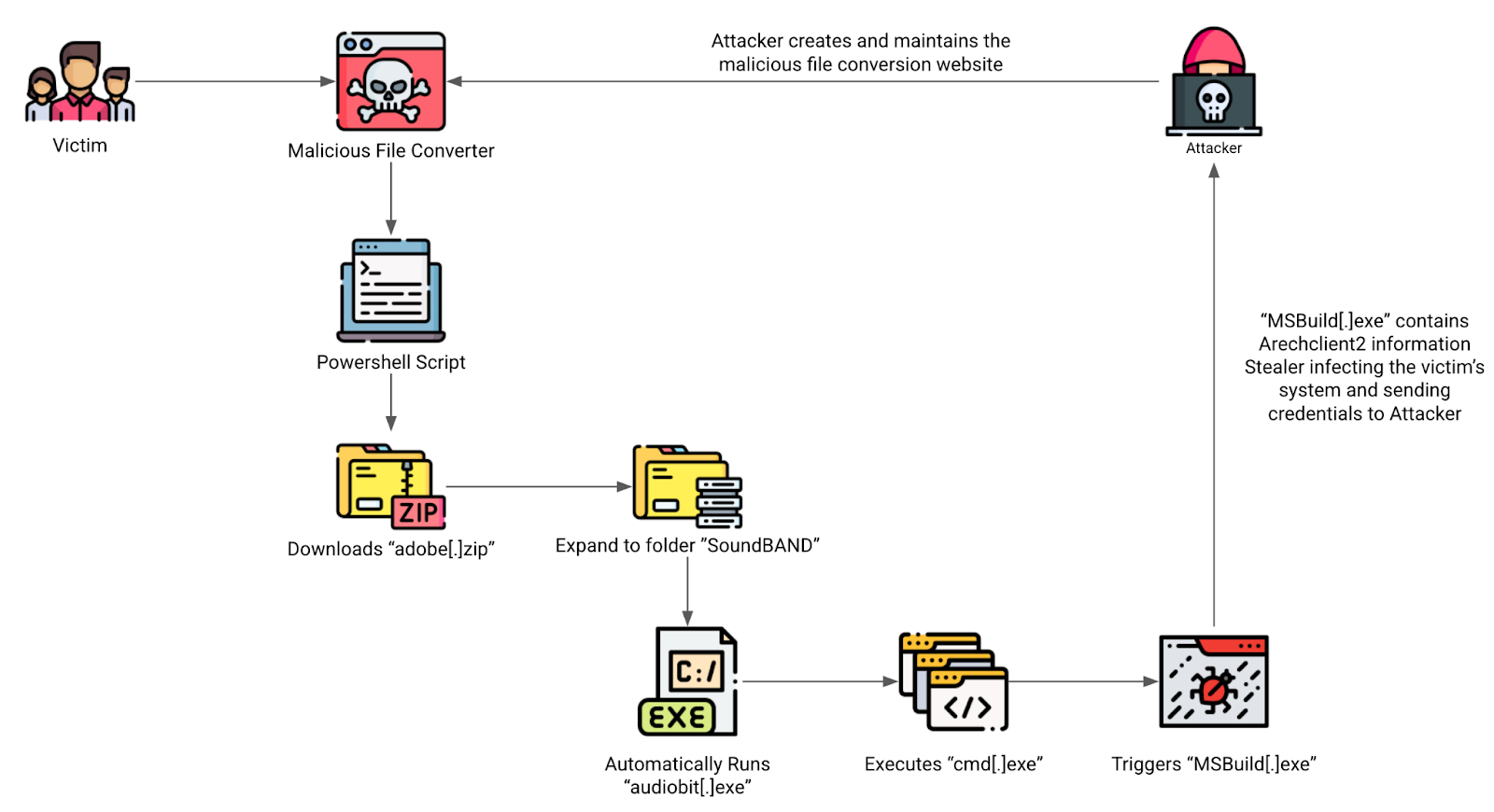
The deception doesn’t end with the fake conversion process. The report reveals that after the CAPTCHA interaction, users are prompted to execute a PowerShell command. This is a critical point where social engineering transitions into system compromise.
The PowerShell command initiates a sophisticated redirection chain to obscure the malware delivery. The final destination of this chain serves a malicious “adobe.zip” payload.
The report identifies the domain “bind-new-connect[.]click” as a known distributor of the ArechClient malware, a variant of the SectopRAT family of information stealers. This Remote Access Trojan has been active since 2019 and is known for its ability to steal sensitive data, including browser credentials and cryptocurrency wallet information.
The “adobe.zip” file expands into a folder containing a malicious executable, “audiobit[.]exe”. Executing this file triggers a multi-stage attack chain, ultimately leading to the execution of the ArechClient2 information stealer.
CloudSEK’s report exposes the intricate tactics employed by cybercriminals to exploit the trust users place in online services. By meticulously impersonating legitimate websites and using social engineering to manipulate user behavior, attackers can deliver dangerous malware capable of stealing sensitive information.