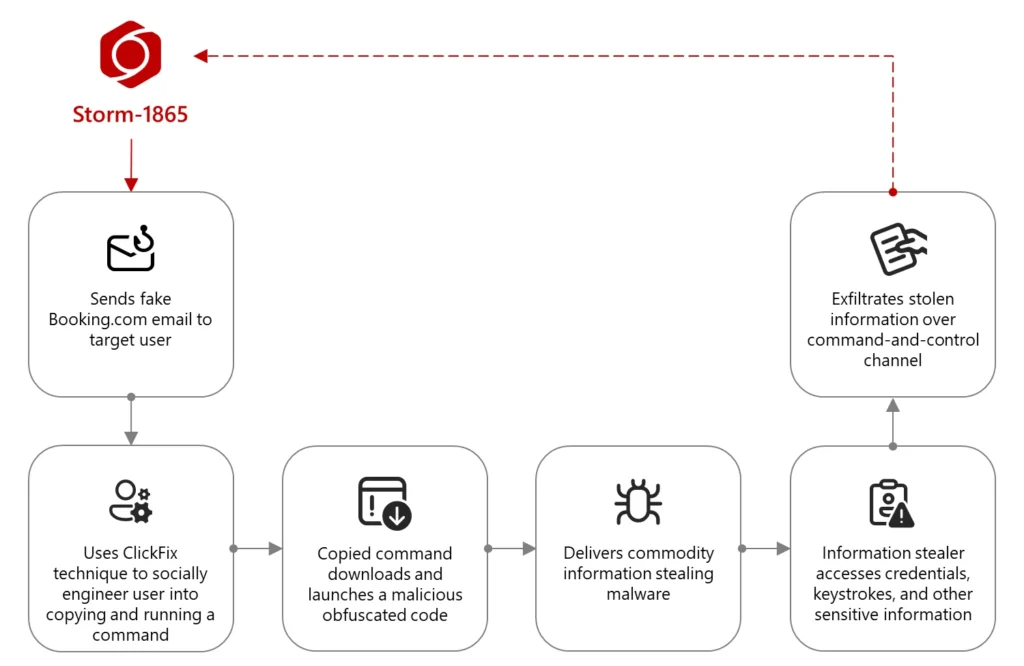
Diagram illustrating the stages of the infection process in this campaign | Image: Microsoft
A sophisticated phishing campaign impersonating Booking.com is targeting organizations in the hospitality industry, using a novel social engineering technique to deliver credential-stealing malware, according to a report from Microsoft Threat Intelligence.
The campaign, which began in December 2024 and is ongoing as of February 2025, employs a social engineering tactic called ClickFix to trick users into downloading malware. “In the ClickFix technique, a threat actor attempts to take advantage of human problem-solving tendencies by displaying fake error messages or prompts that instruct target users to fix issues by copying, pasting, and launching commands that eventually result in the download of malware,” the report explains. This user interaction is crucial to the attack’s success, potentially allowing it to bypass conventional security measures.
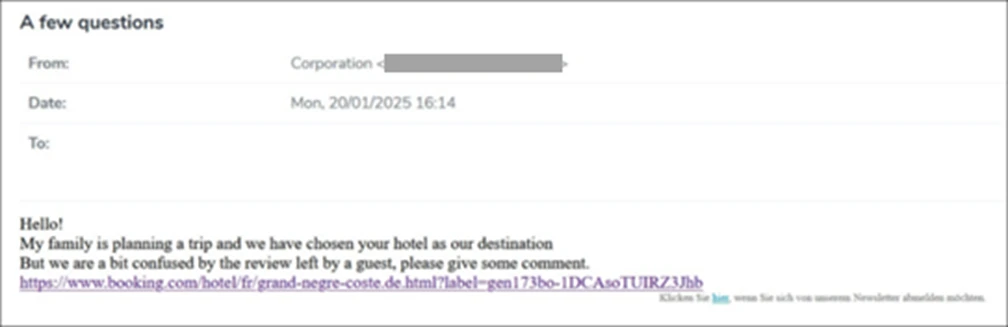
In this campaign, users are lured with fake emails purporting to be from Booking.com. The emails often reference negative guest reviews, requests from prospective guests, online promotion opportunities, or account verification. These emails contain a link or a PDF attachment that claims to direct recipients to Booking.com.
Clicking the link leads to a webpage with a fake CAPTCHA overlaying a background designed to mimic a legitimate Booking.com page. “This webpage gives the illusion that Booking.com uses additional verification checks, which might give the targeted user a false sense of security and therefore increase their chances of getting compromised,” the report states.
The fake CAPTCHA employs the ClickFix technique, instructing the user to use a keyboard shortcut to open a Windows Run window, and then paste and launch a command that the webpage adds to the clipboard. This command downloads and launches malicious code via mshta.exe.
The campaign delivers various families of commodity malware, including XWorm, Lumma Stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT. These payloads are designed to steal financial data and credentials for fraudulent use, which is characteristic of the threat actor tracked by Microsoft as Storm-1865.
Storm-1865 has been involved in phishing campaigns leading to payment data theft and fraudulent charges since at least early 2023. The use of ClickFix in this campaign demonstrates the actor’s evolving tactics to evade security measures.
Microsoft provides recommendations for users and organizations to defend against these threats:
-
Verify the sender: Check the sender’s email address for legitimacy and assess if the sender is marked as “[External]”.
-
Be cautious of unsolicited requests: Legitimate organizations do not request personal or financial information through unsolicited messages or calls.
-
Navigate directly: Instead of clicking links in emails, go directly to the organization’s website to sign in.
-
Beware of urgency and threats: Phishing attacks often create a false sense of urgency.
-
Hover over links: Check the full URL before clicking.
-
Look for typos: Phishing emails often contain typos and subtle misspellings of legitimate domains (typosquatting).
Related Posts:
- Travelers Targeted: Booking.com Phishing Scam Unveiled
- com Impersonation Campaign: Agent Tesla Malware Analysis
- Beware of Fake Google Meet Invites: ClickFix Campaign Spreading Infostealers
- ClickFix: The Rising Threat of Clipboard-Based Social Engineering
- Lazarus APT Targets Job Seekers with “Contagious Interview” Campaign Using ClickFix Technique