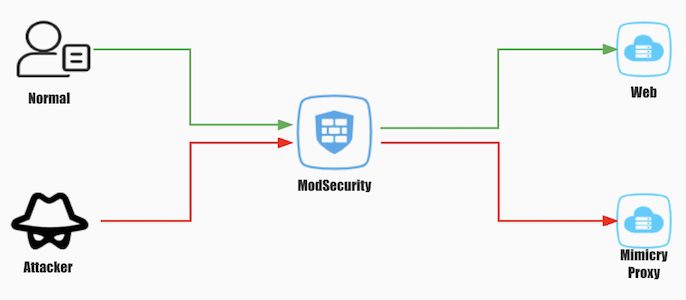
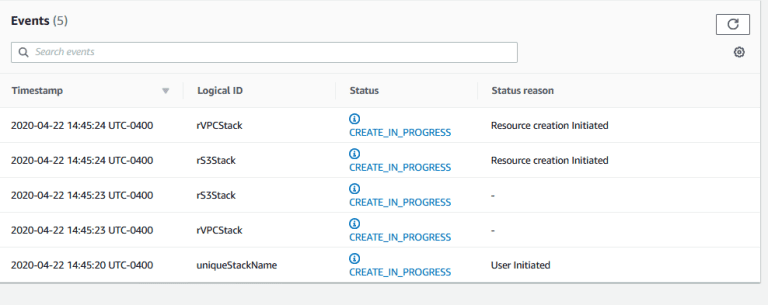
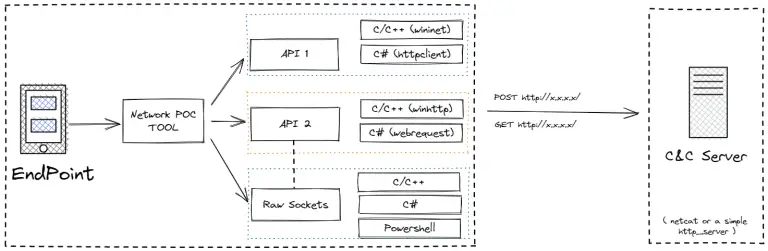
Mimicry Mimicry is a security tool developed by Chaitin Technology for active deception in exploitation and post-exploitation....
Defense
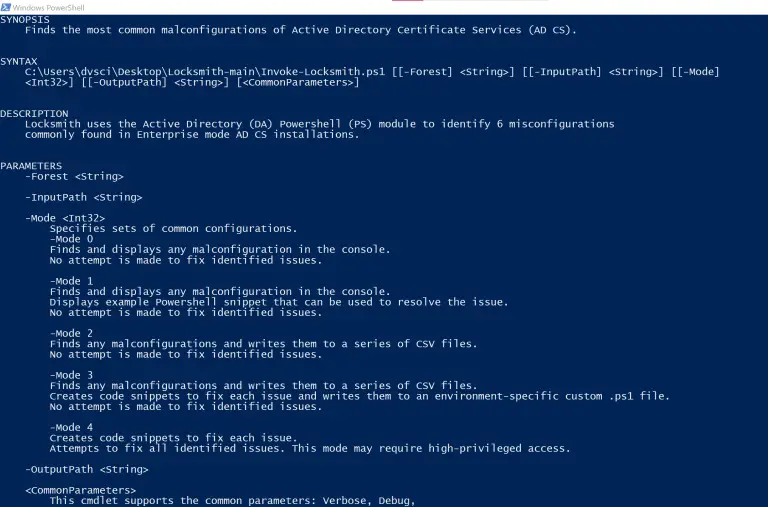
Locksmith A tiny tool to identify and remediate common misconfigurations in Active Directory Certificate Services. Mode 0...
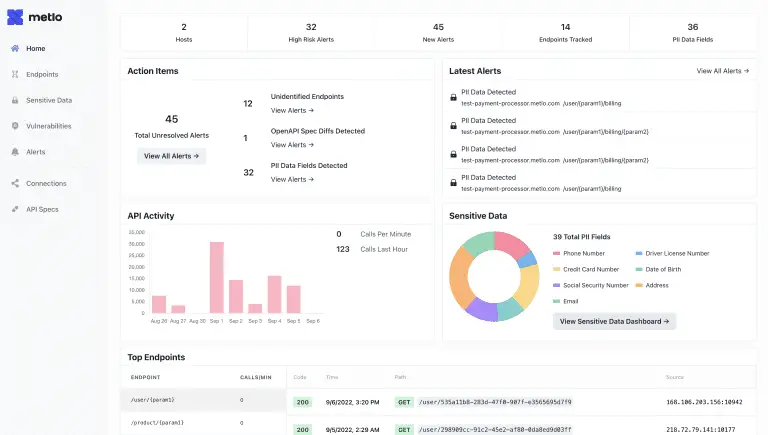
Metlo Metlo is an open-source API security platform Create an Inventory of all your API Endpoints. Proactively...
Indicator-of-Compromise (IOC) Matching IOC matching for incident responders, threat hunters, detection engineers, and security engineers. Use Cases...
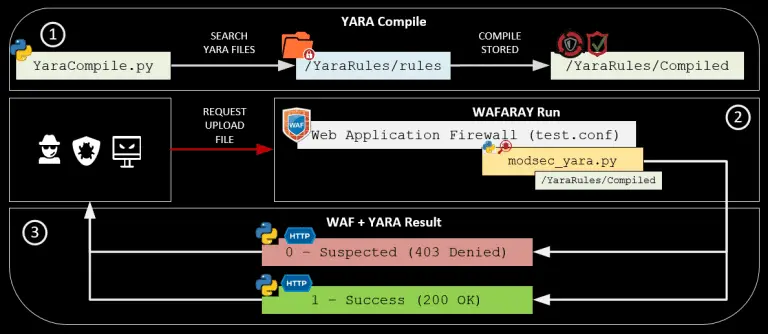
Enhance your malware detection with WAF + YARA (WAFARAY) WAFARAY is a LAB deployment based on Debian...
Self-Service Security Assessment tool Cybersecurity remains a very important topic and point of concern for many CIOs,...
NetLlix A project was created with the aim to emulate and test the exfiltration of data over...
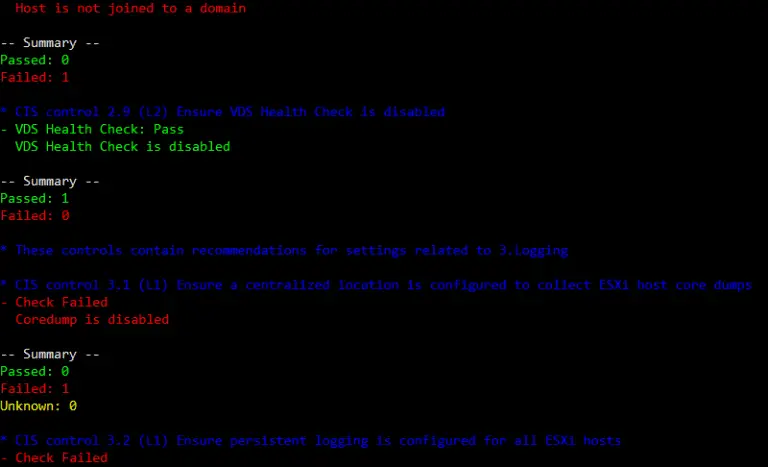
cis-vsphere A tool to assess the compliance of a VMware vSphere environment against the CIS Benchmark for...
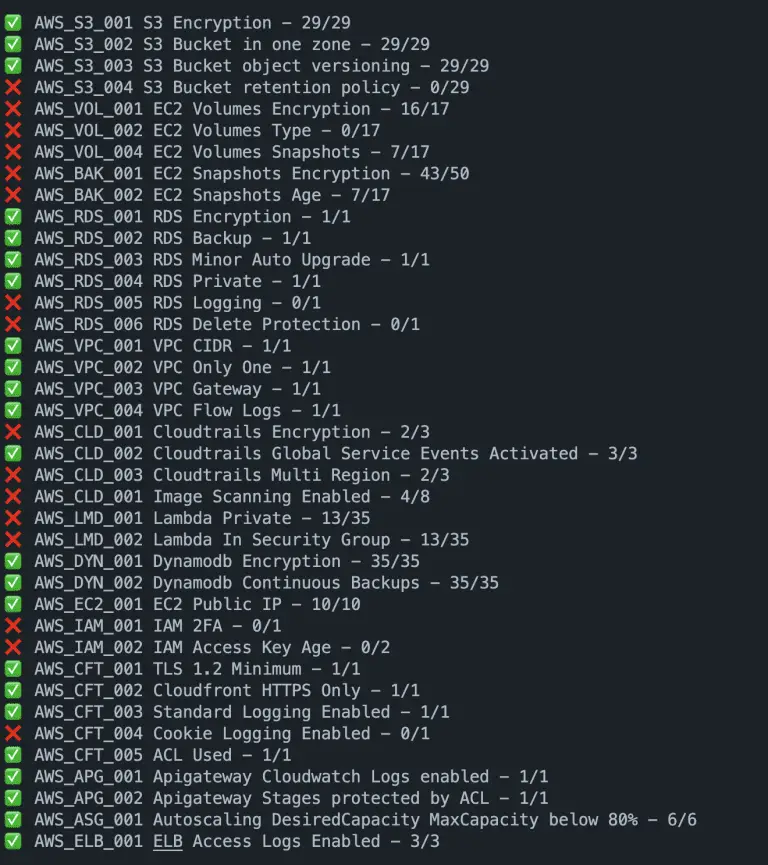
YATAS Yet Another Testing & Auditing Solution Features YATAS is a simple and easy-to-use tool to audit...
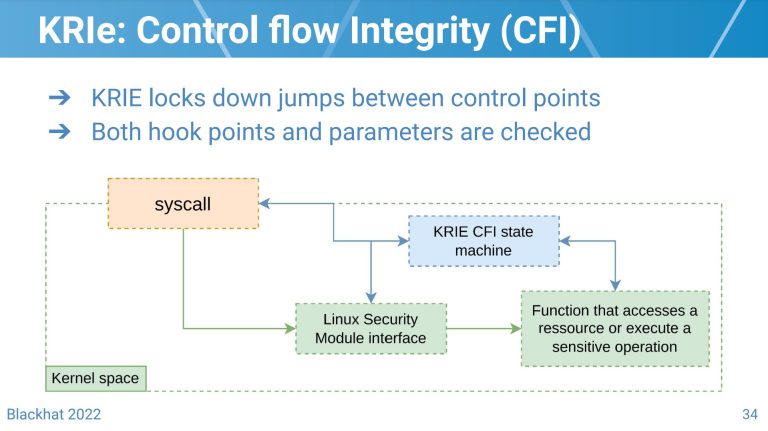
KRIe KRIe is a research project that aims to detect Linux Kernel exploits with eBPF. KRIe is...
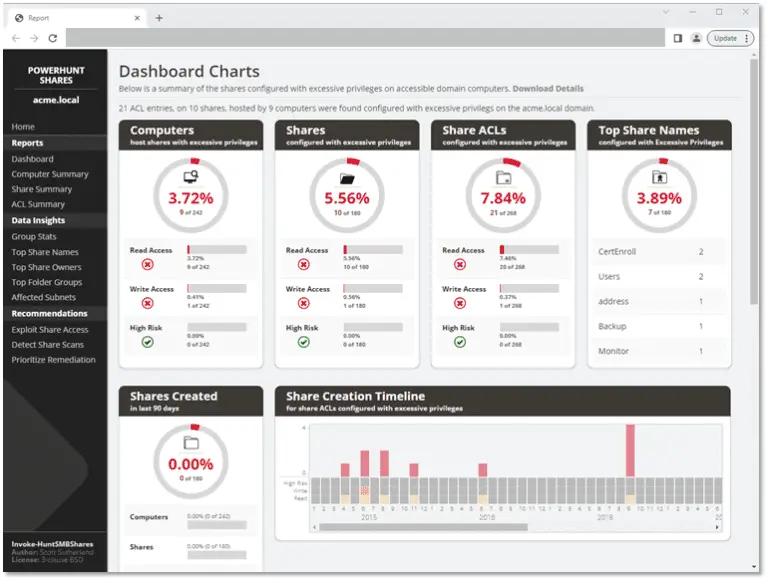
PowerHuntShares PowerHuntShares is designed to automatically inventory, analyze, and report excessive privilege assigned to SMB shares on...
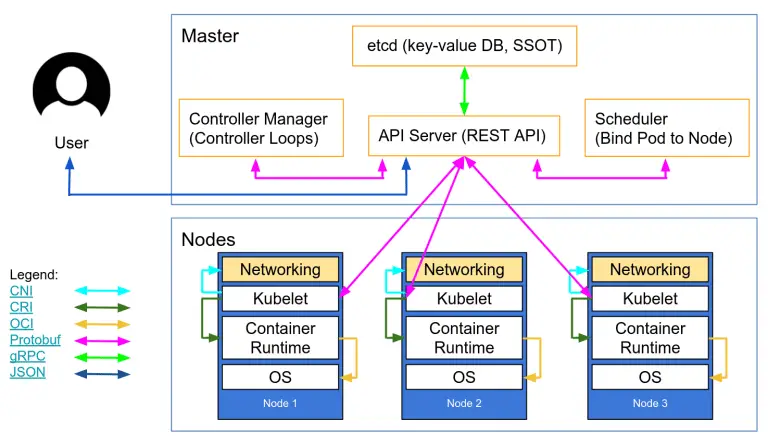
StackRox Kubernetes Security Platform The StackRox Kubernetes Security Platform performs a risk analysis of the container environment,...
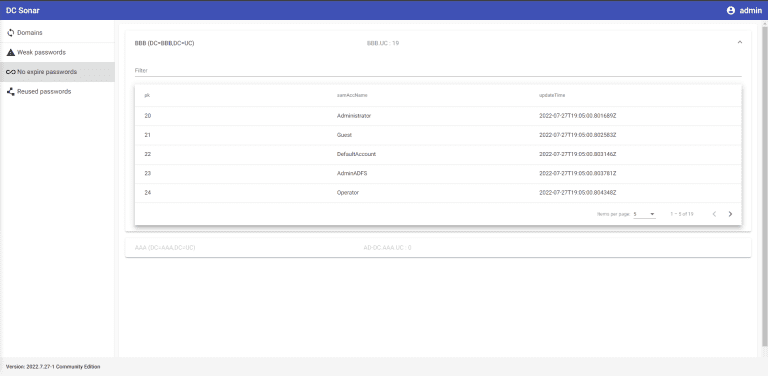
DC Sonar Analyzing AD domains for security risks related to user accounts Architecture For the visual descriptions,...
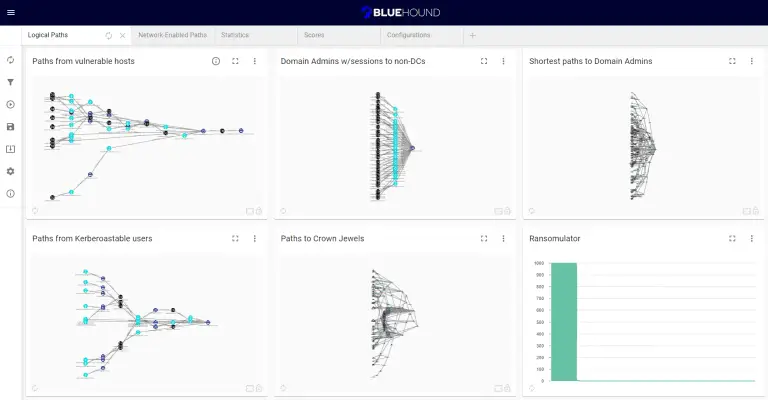
BlueHound BlueHound is an open-source tool that helps blue teams pinpoint the security issues that actually matter....
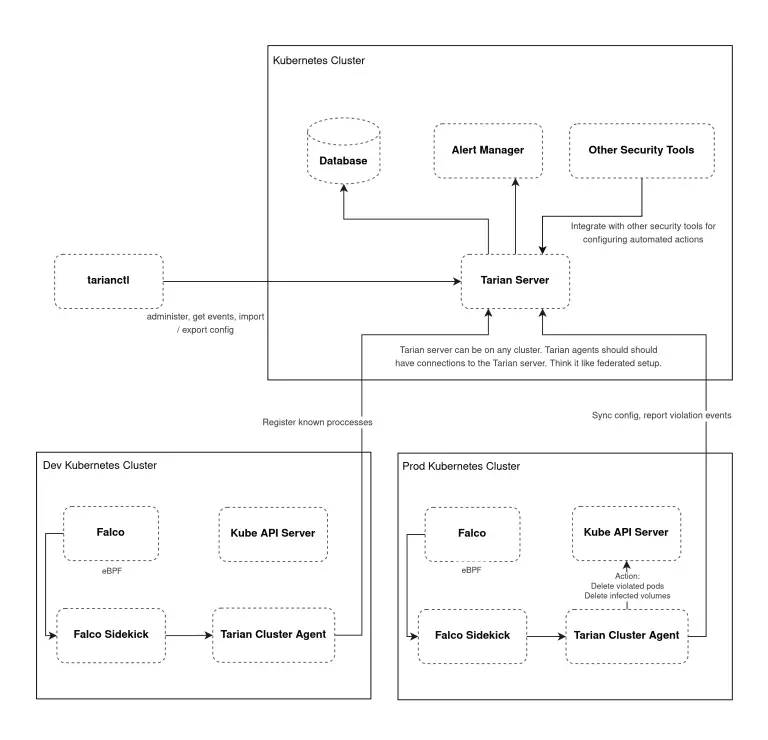
Tarian Protect your applications running on Kubernetes from malicious attacks by pre-registering your trusted processes and trusted...