Category: Malware Analysis
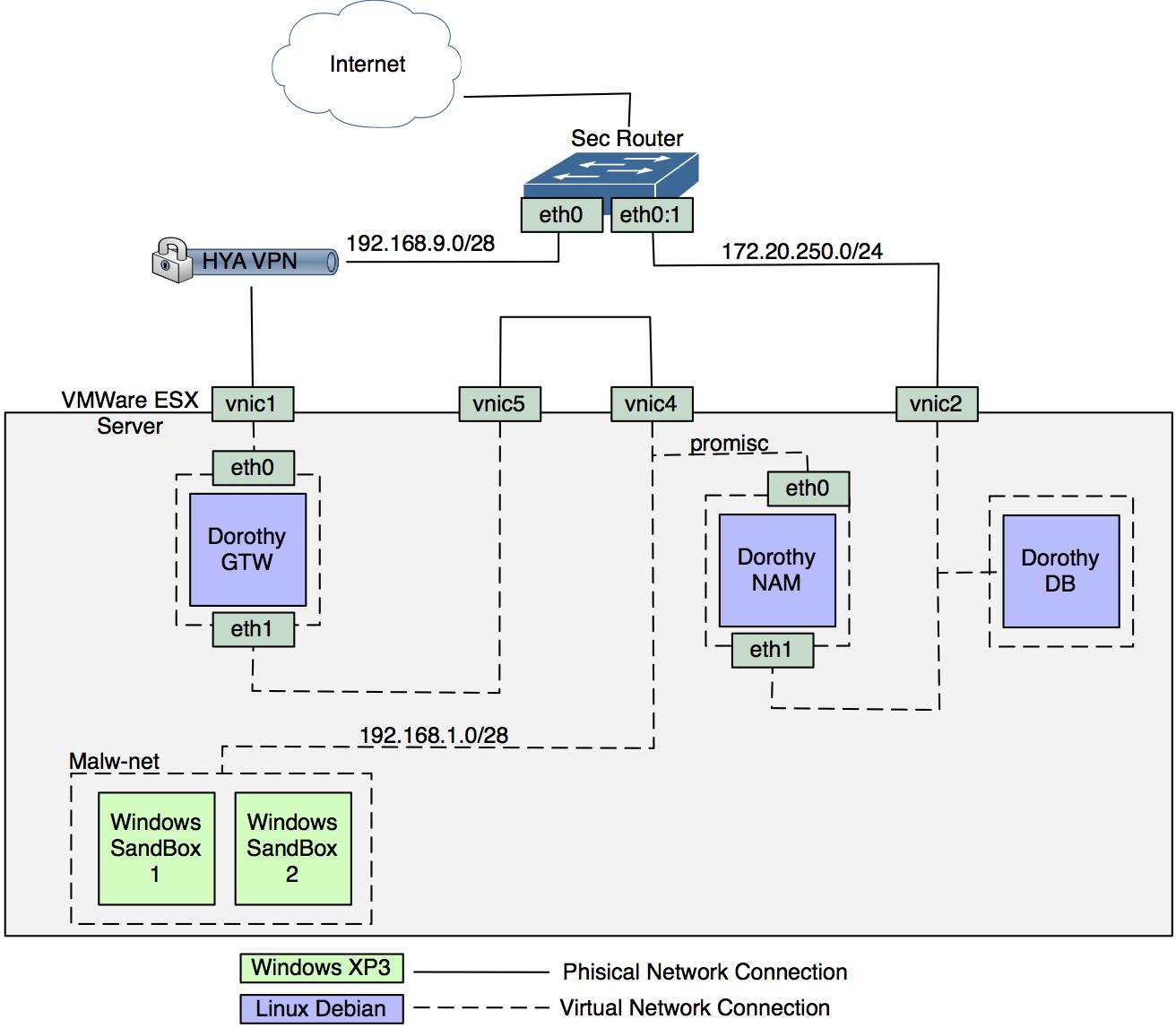
Dorothy2 A malware/botnet analysis framework written in Ruby. Dorothy2 is a framework created for suspicious binary analysis. Its main strengths are a very flexible modular environment and an interactive investigation...
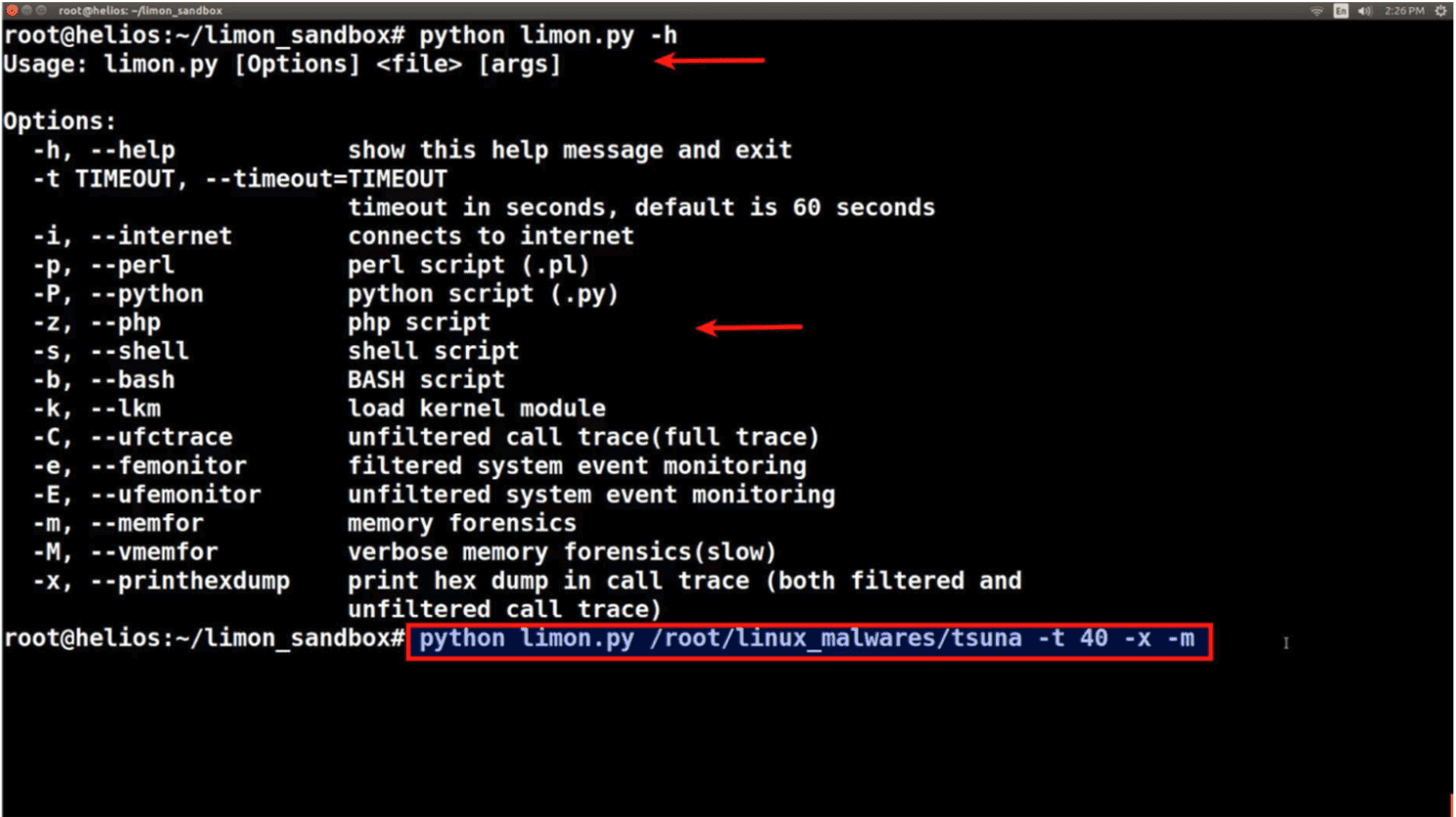
Limon – Sandbox for Analyzing Linux Malwares Limon is a sandbox developed as a research project written in python, which automatically collects, analyzes, and reports on the runtime indicators of...
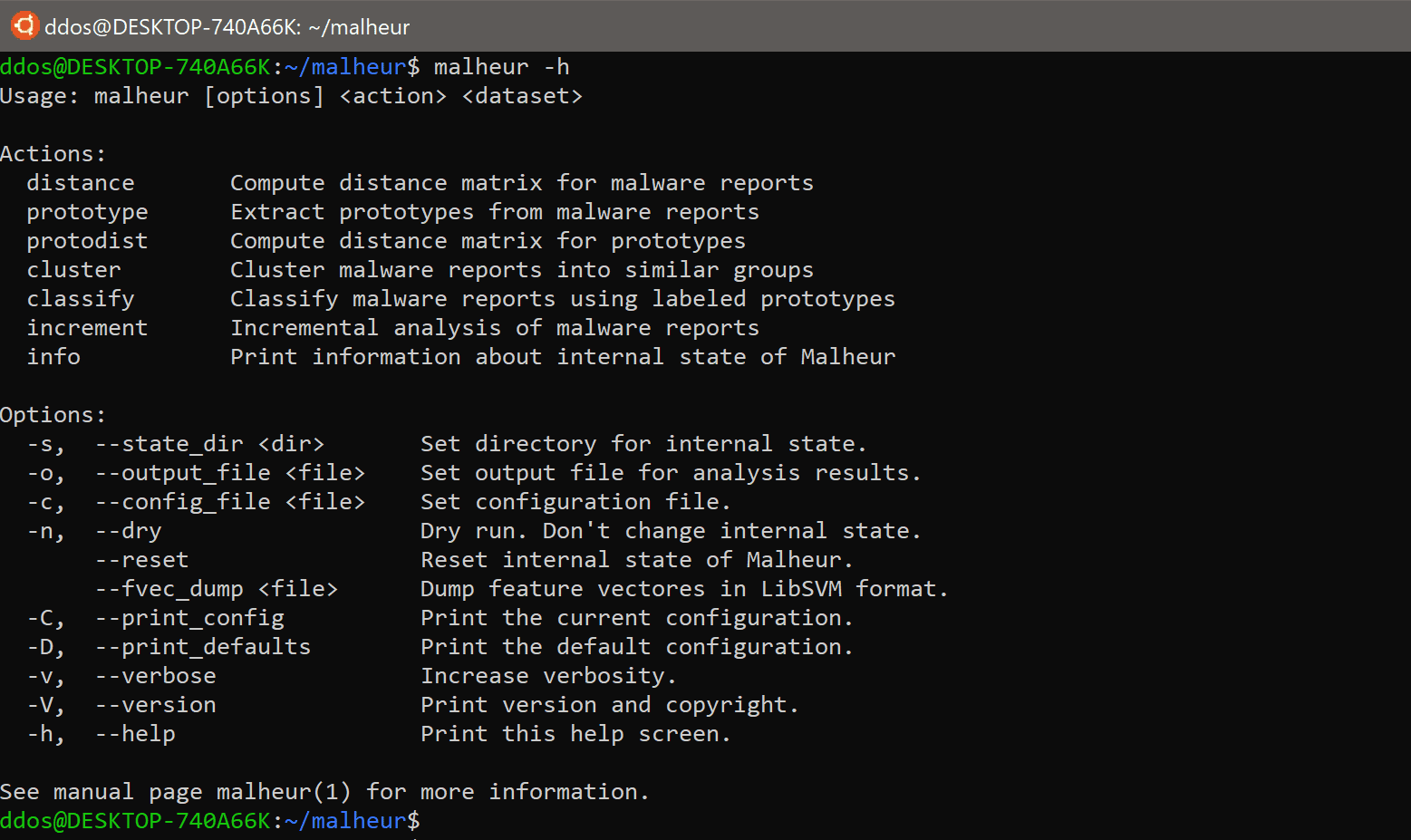
MALHEUR – Automatic Analysis of Malware Behavior Introduction Malheur is a tool for the automatic analysis of malware behavior (program behavior recorded from malicious software in a sandbox environment). It...
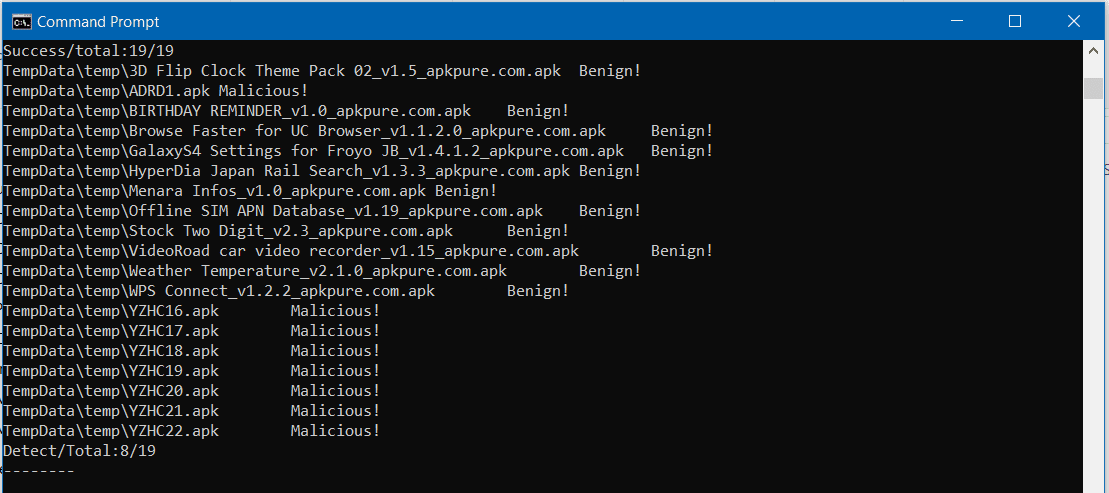
MADLIRA Malware detection using learning and information retrieval for Android Overview MADLIRA is a tool for Android malware detection. It consists of two components: TFIDF component and SVM learning component....
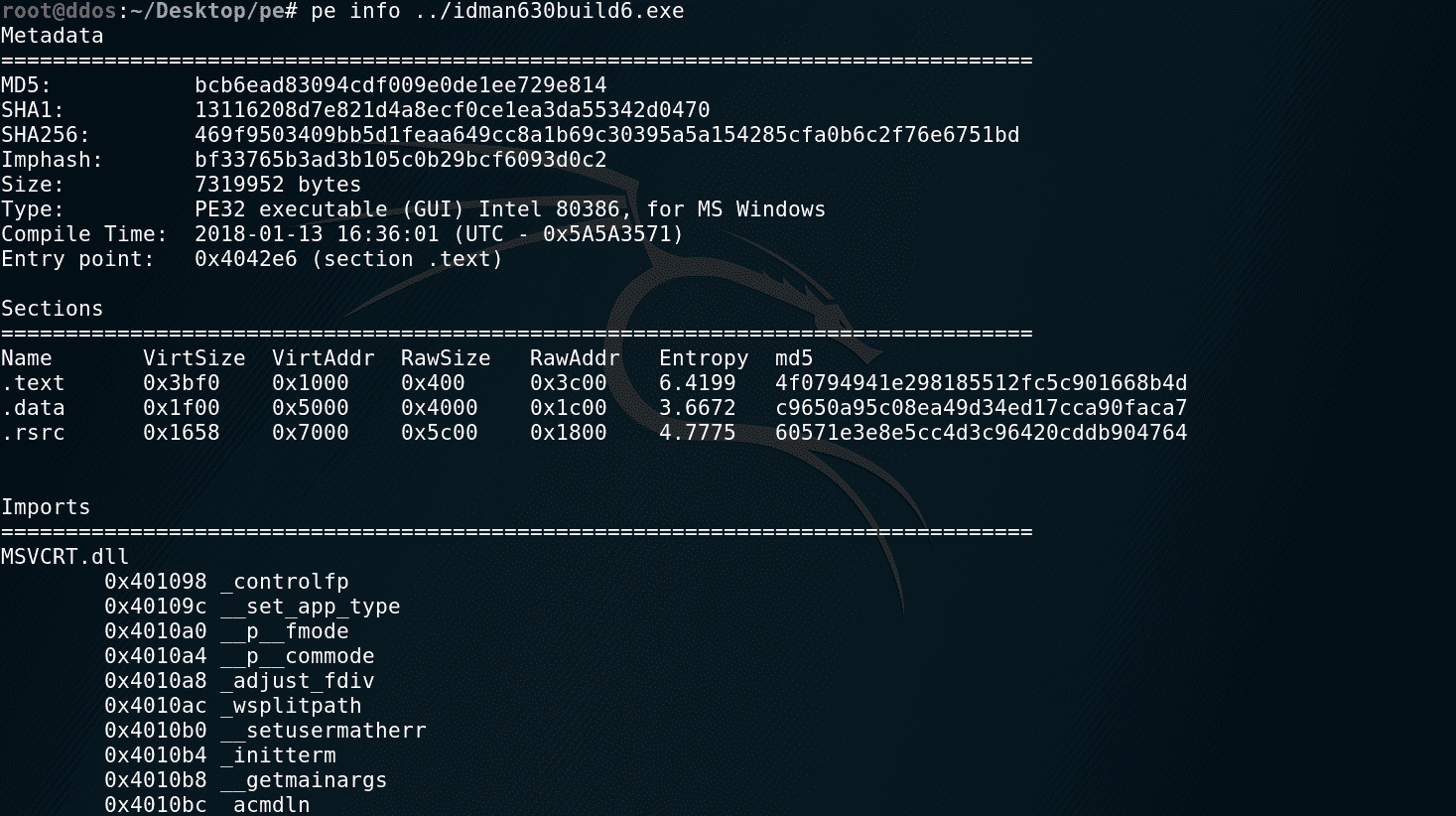
PE Tool to analyze PE files in python 3. Current features : Show information about the file (import, exports, resources) Search for interesting information in the file (abnormal resources, peid…)...
box.js A utility to analyze malicious JavaScript. Changelog v1.19.25 * Track execution of JS served out by a C2 as an IOC. * Track ActiveX object creations as IOCs. *...
Rootkit Hunter (commonly abbreviated as RKH) is a security monitoring and analyzing tool for POSIX compliant systems, to help you detect known rootkits, malware, and signal general bad security practices. Rootkits...
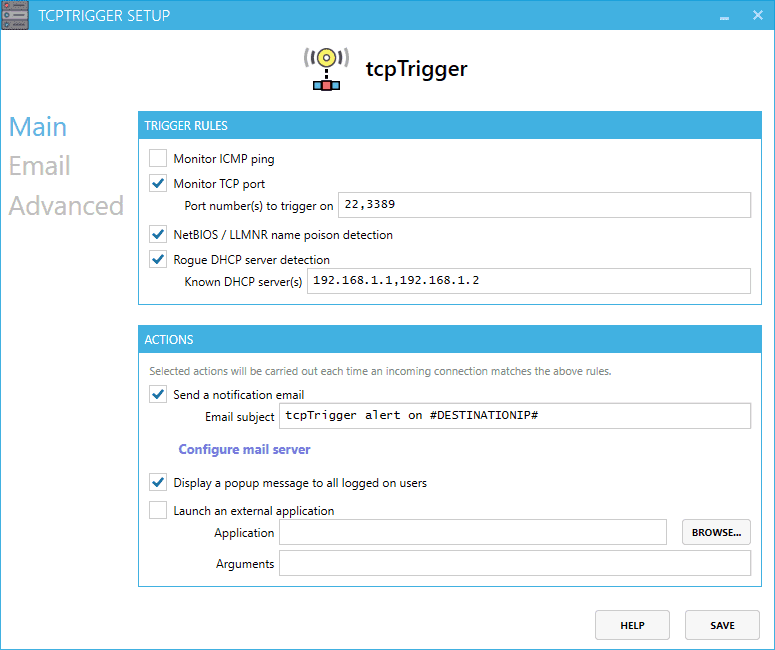
tcpTrigger tcpTrigger is a Windows service intended to notify you of incoming network connections. You specify a TCP port to monitor and an action to take. Actions taken include: sending...
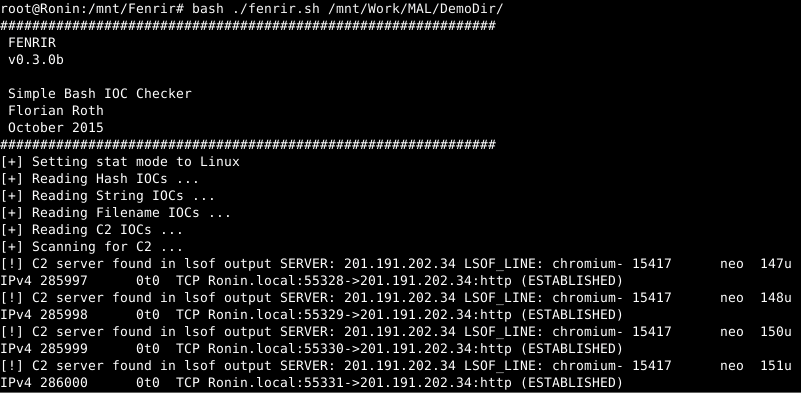
Fenrir Simple Bash IOC Scanner Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise (IOCs): HashesMD5, SHA1, and SHA256 (using...
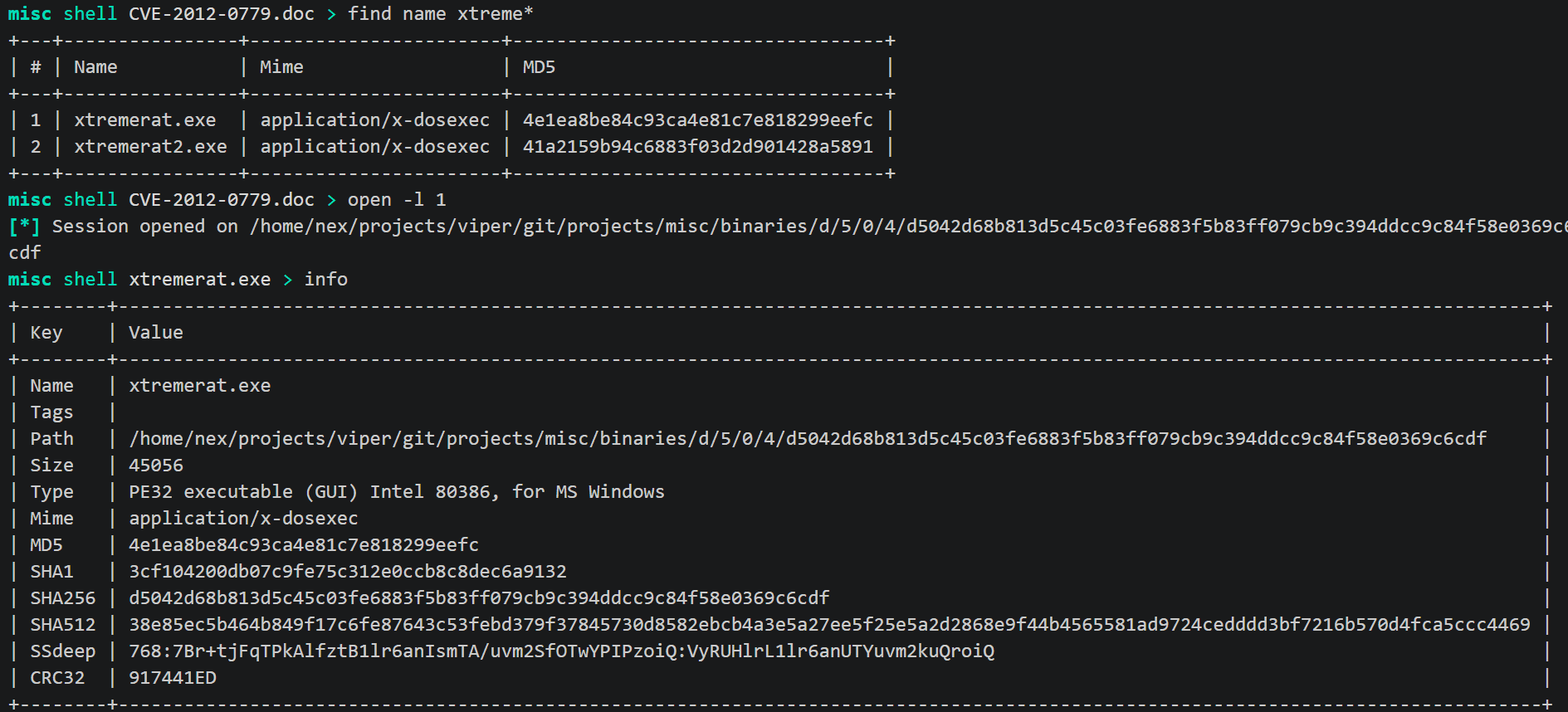
Viper is a binary analysis and management framework. Its fundamental objective is to provide a solution to easily organize your collection of malware and exploit samples as well as your...
binsnitch can be used to detect silent unwanted changes to files on your system. It will scan a given directory recursively for files and keep track of any changes it...
Droidefense (originally named atom: analysis through observation machine)* is the codename for android apps/malware analysis/reversing tool. It was built focused on security issues and tricks that malware researcher have on them everyday work. For those...
AIEngine is a next-generation interactive/programmable Python/Ruby/Java/Lua and Go network intrusion detection system engine with capabilities of learning without any human intervention, DNS domain classification, Spam detection, network collector, network forensics...
PEframe is an open source tool to perform static analysis on Portable Executable malware and generic suspicious file. It can help malware researchers to detect packer, xor, digital signature, mutex, anti-debug, anti-virtual...
Process Refund An attempt to implement Process Doppelgänging Getting Started Just clone the repo git clone https://github.com/Spajed/processrefund.git and open the .sln with Visual Studio 2015. Prerequisites Currently, this works only in...